Stop data leakage and rogue AIs with jailbreak-proof Zero Trust for LLMs, agents, data, and apps. Cloud, in-house, or hybrid. Unified control, end-to-end protection.
Unified Zero Trust for AI
The Challenge
AI is breaking traditional security approaches. With LLMs, agents, and data scattered across cloud, IT, data centers, operational infrastructure, endpoints and the open Internet, AI systems interact in unpredictable ways—combining user and agent privileges, sensitive data, and automation in complex workflows. One prompt can trigger actions, leak confidential information, or spread false outputs with real-world impact. The attack surface is massive. The risk? Even bigger.
LLM & AI Agent Protection Challenges

AI Risk in Complex, Distributed Environments
Modern AI ecosystems—spanning LLMs, agents, APIs, cloud, on-prem IT, and Internet-exposed endpoints—operate across fragmented stacks with overlapping entitlements. This complexity, combined with inconsistent policy enforcement and fluid data flows, creates vulnerabilities to privilege abuse and unauthorized access. Without fine-grained, identity-aware end-to-end controls, interactions easily lead to over-permissioning, data leaks, rogue AI risks, insider threats, and external breaches.
Unauthorized Data Access
Users and AI apps should have access to the same data – no more, no less – when accessing data via LLMs or agents as they do when fetching data directly – yet these entitlements need to be imposed without excessive complexity or restrictions on AI capabilities – and without relying solely on jailbreak-vulnerable prompt filtering.


Regulatory and Real-World Consequences
AI-driven decisions have tangible impact—from automation failures to biased outputs and misinformation. At the same time, enterprises may require compliance with standards like NIST 800-53, ISO 27001, and GDPR. Weak governance can lead to audit failures, brand damage, or legal exposure, making secure AI integration both a business and regulatory imperative.
“Identity must be reimagined for AI. Applying Zero Trust principles to AI provides organizations with the ability to safeguard their AI initiatives while maintaining compliance and governance across complex, distributed environments.”
– Frank Dickson, Global VP of Security & Trust, IDC

DOWNLOAD THE WHITEPAPER
Securing AI with Zero Trust: Managing Identity and MCP Risks
Xage Delivers Unified Zero Trust for LLMs and AI Agents
Outcomes
Xage unified Zero Trust for LLMs and AI agents delivers outcomes that drive your organization forward.

Unleash AI With Confidence
Unlock organization-wide AI with confidence—secure, governed, jailbreak-proof and responsible, while avoiding burdensome data classification and tagging.

Simplify Compliance and Operations
Centralize compliance, security, UX, and admin with a single scalable platform spanning your entire infrastructure and AI ecosystem.

Harden the AI Attack Surface
Use rigorous, jailbreak-proof data request-response-level least-privilege access control (just-in-time access, zero standing privileges) to block data leakage and stop a rogue AI agent from being able to inflict damage.
“As AI factories emerge as the foundational infrastructure accelerating AI innovation, safeguarding them has become a critical priority. Together, NVIDIA BlueField and Xage’s zero-trust security enable organizations to modernize their protection strategies across AI factories and infrastructure —driving secure, scalable innovation forward.”
– Ofir Arkin, Sr. Distinguished Architect, Cybersecurity Team at NVIDIA
Xage Benefits and Differentiation
Xage Fabric delivers unified AI control by overlaying identity-based security across cloud, edge, and on-prem environments. It maps user and agent identities, roles, and attributes to precise data access policies—preventing unauthorized access and sensitive data exposure. With unified Zero Trust for LLMs and AI agents, organizations can:
Secure Every AI Deployment
- Apply unified Zero Trust protection across corporate, vendor, and BYOAI LLM and AI-agent deployments.
- Enforce consistent identity and policy controls across the full AI pipeline.
- Enable third-party or in-house chatbots (e.g., Microsoft Copilot) to securely use corporate data—without risk of leaks.
Deploy Zero Trust from Agents to Infrastructure
- Govern sensitive data access for LLMs, agents, and users.
- Enforce least-privilege on training, inference, and orchestration.
- Lock down access to digital infrastructure—servers, GPUs, and edge hardware.
- Extend Zero Trust policies to cyber physical systems: DCIM, power, cooling, and building management.
Streamline Adoption at Scale
- Extend existing access controls to AI—no tagging, reclassification, or infrastructure rebuilds.
- Automatically enforce existing identity-based access controls
- Trace identity and entitlements across users, agents, and LLM workflows with multihop security.
- Accelerate AI rollouts without disrupting existing security policies.
Stop Jailbreaks Before They Start
- Enforce identity-based access at the network level to block data leaks and prompt-based jailbreaks.
- Use rigorous network-level enforcement with identity-based controls to stop unauthorized access or exposure—no matter the manipulation.
- Prevent AI agents and LLMs from leaking sensitive data, even under jailbreak attack.
- Deliver deterministic, policy-driven enforcement for guaranteed access control—beyond what LLM firewalls, guardrails, or prompt/output filters can provide.
Simplify Compliance and Visibility
- Centralize Zero Trust enforcement across your entire AI ecosystem, with every access and attempt logged for full traceability.
- Protect logs in Xage’s tamperproof, quantum-proof Fabric—ensuring attackers can’t erase evidence and compliance requirements are always met.
Key Capabilities: Unified Zero Trust for LLMs and AI Agents
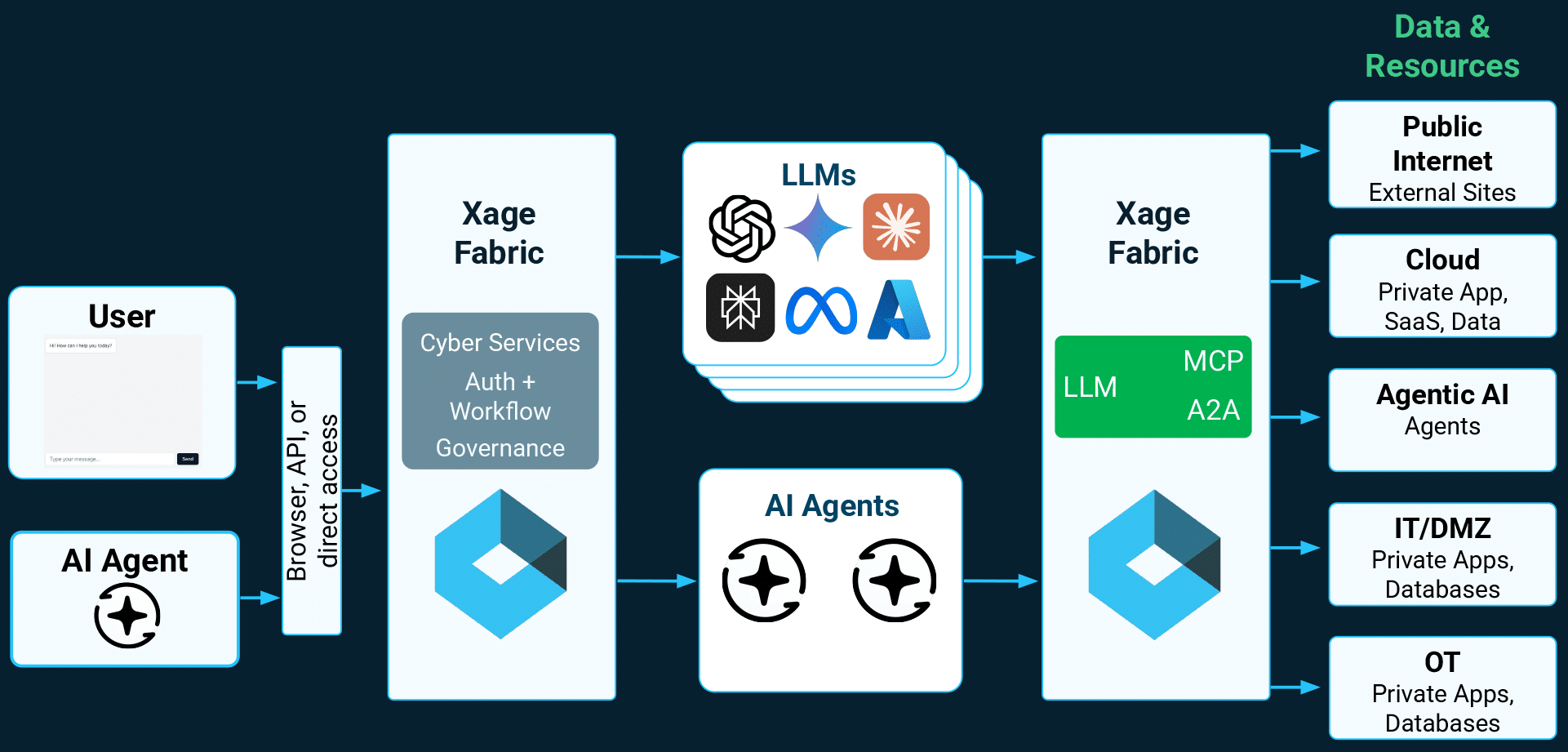
Overlay Architecture
Bring AI wherever you need it—Xage keeps it secure.
- Unified overlay mesh enforces Zero Trust across corporate, vendor, and BYOAI deployments.
- Covers the full spectrum—from enterprise LLMs to autonomous agents operating in IT, OT, and Cloud.
- Consistent policy and identity control across fragmented AI environments, without re-architecting.
- Tamperproof and quantum proof—nodes of the mesh co-operate to store identity, policy and log data securely, with no single point to hack.
Identity-based Access to AI infrastructure
Whether it’s infrastructure, AI pipelines, or agent activity—Xage ensures Zero Trust at every layer.
- Physical infrastructure — lock down access to servers, GPUs, and edge hardware – even cooling and power systems where required.
- Workloads & runtimes — enforce least-privilege controls on training, inference, and orchestration layers.
- Data & interactions — govern how LLMs, agents, and users access and act on sensitive data.
Mapping Identity-based Access to Data
- Extend existing protections—no rework required. Xage makes AI adoption seamless by honoring the controls you already trust:
- Automatically enforces existing identity-based access rules when AI retrieves data from protected sources.
- No need to tag and rebuild: AI adheres to the same access boundaries as your users and apps.
Eliminates friction in AI rollouts, preserving security while accelerating deployment.
Just-in-Time, Just-Enough Access for AI and Users
Adaptive, Just-in-Time and Just-enough Access
- Just-in-time authorization grants access only when required—no standing privileges.
- Fine-grained, identity-based policies adapt to user roles, agent behavior, and workload context.
- No trade-off between speed and security—maintain operational agility while locking down overreach.
- Put Data and Rogue-AI concerns to rest with certainty—thanks to network-protocol-level enforcement.
Multihop for AI Interactions
- Automatic multihop security for chains of AI components. Xage traces identity and entitlements across chains of user, agents, LLMs and data sources to ensure correct access controls.
- Automatic multihop security across multi-layered and multi-zone architectures. Xage maintains identity, data and entitlement integrity across internal and external environments that may span IT, data center, cloud, and even third-party partners.
- LLM-to-Data Integration Across Layered and Zoned Networks: Xage enables secure LLM access to distributed data sources across segmented and multi-hop environments. For instance, an LLM hosted in the cloud can securely query data deep within an operational network—without exposing the core environment or requiring manual data uploads from each site to the main datacenter for LLM ingestion.
Continuous Enforcement for AI Pipelines
- Secure every interaction—Xage enforces policy from start to finish. Protect RAG pipelines, multi-LLM workflows, and autonomous agents with continuous, identity-based control across the entire AI lifecycle.
- Maintains real-time control over data access and behavior across dynamic AI processes.
- Enforces identity-based policies at each stage of the AI pipeline—training, retrieval, inference, and response.
- Prevents unauthorized access or actions across interconnected LLMs, agents, and data sources.
- Enables secure orchestration of complex, multi-agent workflows without sacrificing performance or agility.
Model Context Protocol (MCP) Security
Model Context Protocol (MCP) systems are expanding fast—but still lack standard credential controls. Xage fills the gap with modern, Zero Trust protection for all client-server interactions
- Protect Every Transaction: Enforce identity, role, and policy on every MCP request—human or machine.
- Credential Management at Scale: Centralize issuance, rotation, and revocation of MCP client/server credentials.
- Privileged Access: Apply just-in-time access and session controls across all MCP command paths.
AI Agent and A2A Security
Xage secures autonomous Agent2Agent (A2A) communications by applying identity-centric access controls to every machine interaction. This prevents unauthorized automation, data access, or command execution across distributed AI systems.
The Xage Isolation Shield (XIS) provides a software wrapper for each AI agent, ensuring that i) only authenticated and authorized users or apps can send commands to the agent; ii) the agent must itself be authenticated and can only send commands and access data and other resources according to its own, and its users, authorizations. In other words, the XIS and the Xage Fabric apply Zero Trust control to each AI agent and to the interactions between them.
AI Guardrails
The Xage Fabric supplements its core Zero Trust access control capabilities with advanced sanitization and redaction capabilities for AI prompts, data retrievals and outputs to protect data privacy and compliance. Sensitive information such as PII, intellectual property, or confidential business data is automatically identified and masked out before reaching LLMs, AI agents, apps or users as applicable, reducing leakage risk. The Xage architecture also enables the use of third-party sanitization and redaction tools within the AI data flows.
AI Isn't Waiting. Neither Should Your Security.
Fill out the form and someone will be in touch with you within 24 hours to schedule a meeting.







