Secure tactical, operational, and strategic critical assets from the edge to the core to assure mission success.
Zero Trust Cybersecurity To Protect Mission Operations
U.S. Government Agencies and Partners Trust Xage to Deliver Zero Trust Security











“Xage Security empowers federal agencies to adopt zero trust principles and maintain mission assurance without the need for costly asset replacements. With Xage's identity-based secure local and remote access, edge protection, and data security, every interaction from the tactical and operational edge to the strategic cloud is trusted, ensuring the highest level of security for critical systems and data.”
Nicolas M. ChaillanFirst (former) U.S. Air Force and Space Force Chief Software Officer

Xage Awarded $17 Million Cybersecurity Contract by U.S. Space Force
Xage Contract Vehicle Listings




Department of Defense Cybersecurity Challenges
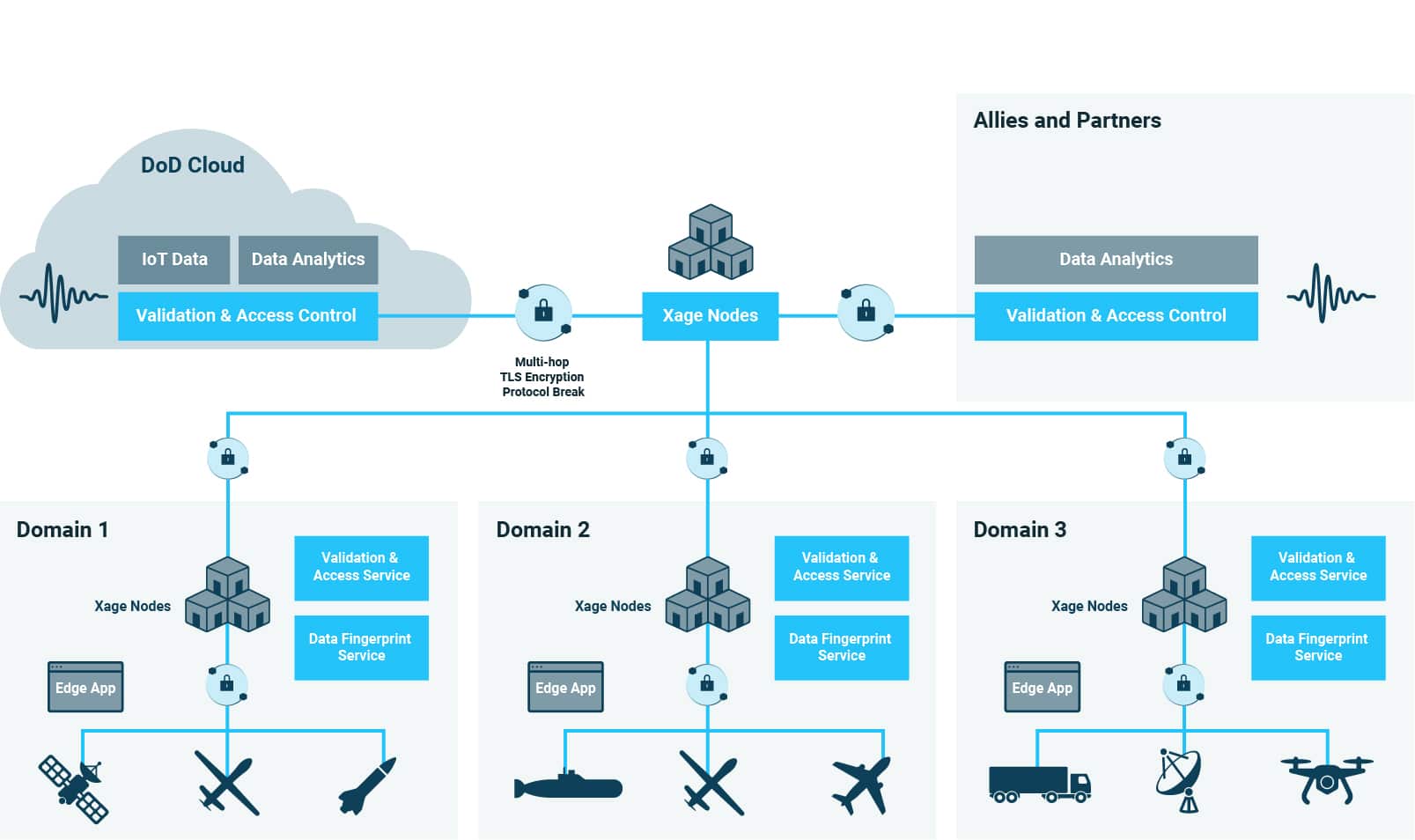
The Department of Defense is moving rapidly to adopt Zero Trust security principles to secure the mission from strategic core to tactical edge. Collaborating across agencies and organizations to secure a wide range of tactical systems, many in the field with intermittent or degraded connectivity, all while assuring data integrity and control, but enabling cross-domain data sharing, is a massive challenge.
From the Tactical Edge to the Strategic Core
Data integrity and authenticity must be assured to deliver secure Resilient Data Sharing and support the mission.

Access control policy must be enforced in disconnected, denied, intermittent, or limited (DDIL) connectivity environments.

Modern and legacy assets must be cyber-hardened in a device agnostic way to secure OT operations and major industrial processes.
How Can The DoD Zero Trust Strategy Apply to Operational Technology (OT)?
Today the technology exists to implement the DOD Zero Trust Architecture in IT systems perspective, but many agencies may face challenges extending zero trust principles into OT at the operational edge. To accomplish the goals laid out in the DoD Zero Trust Strategy and Roadmap documents, and realize the vision set forth in JADC2, new technologies will have to step up to the challenges and complexities presented by the modern battlefield environment.
Overcoming Security Challenges in Operational Systems
Today’s warfighters are supported by a large interconnected system of industrial operations, from civil engineering to HVAC to fuel distribution, airfields, port infrastructure, and their logistics. Assuring cyber hardened assets at the tactical edge alongside secure data sharing across this complex array of assets is vital to mission success.
Achieve Cyber Hardening and Secure Cross-Domain Data Sharing with Xage
With the Xage Fabric leveraging a cyber mesh architecture, operational assets (including Mission Sensors/OT, IIoT and Cloud environments) can be protected to ensure data integrity and authenticity to support the mission. The Fabric is agentless and deploys with minimal network changes, while supporting assets and sensors already in the field.
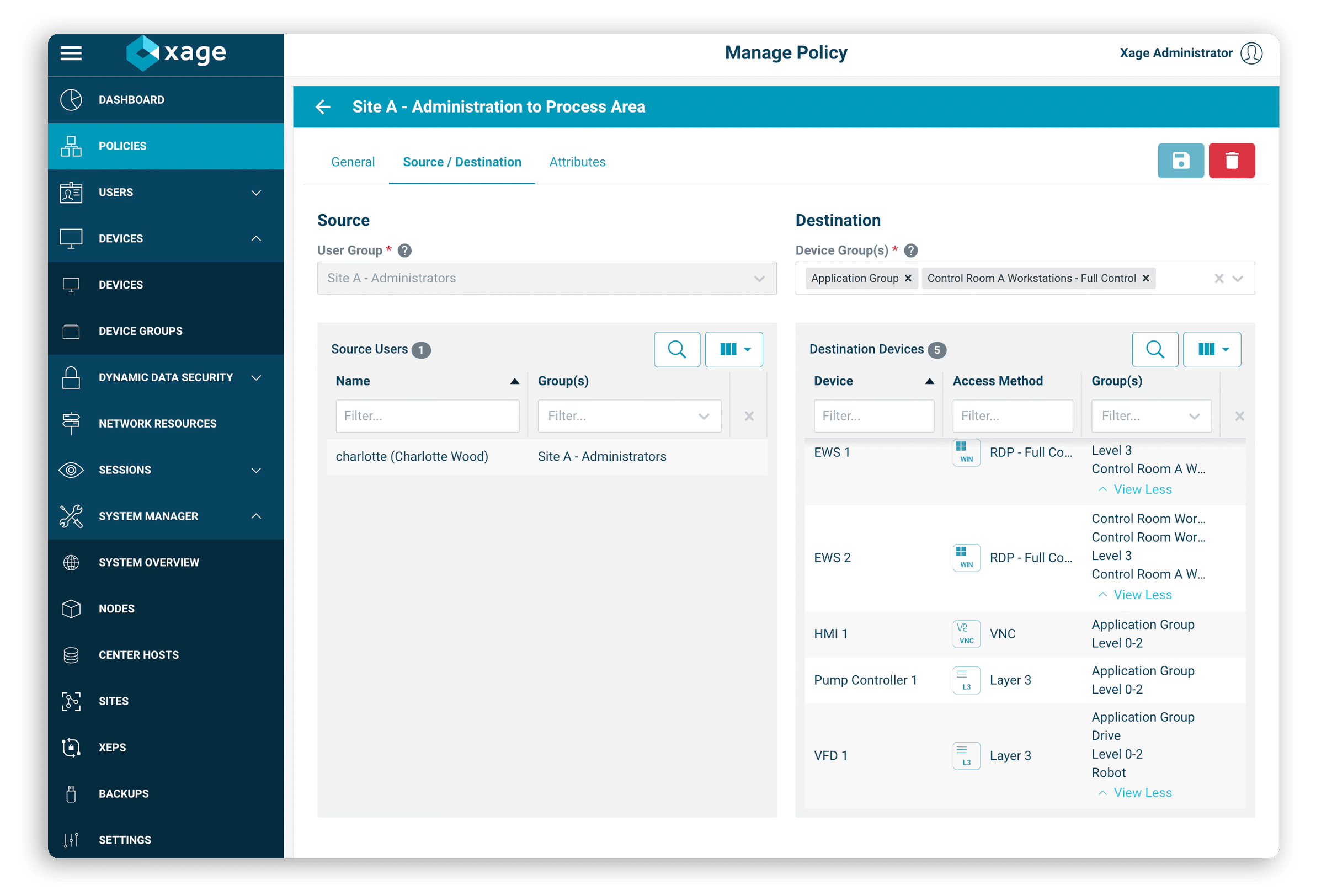
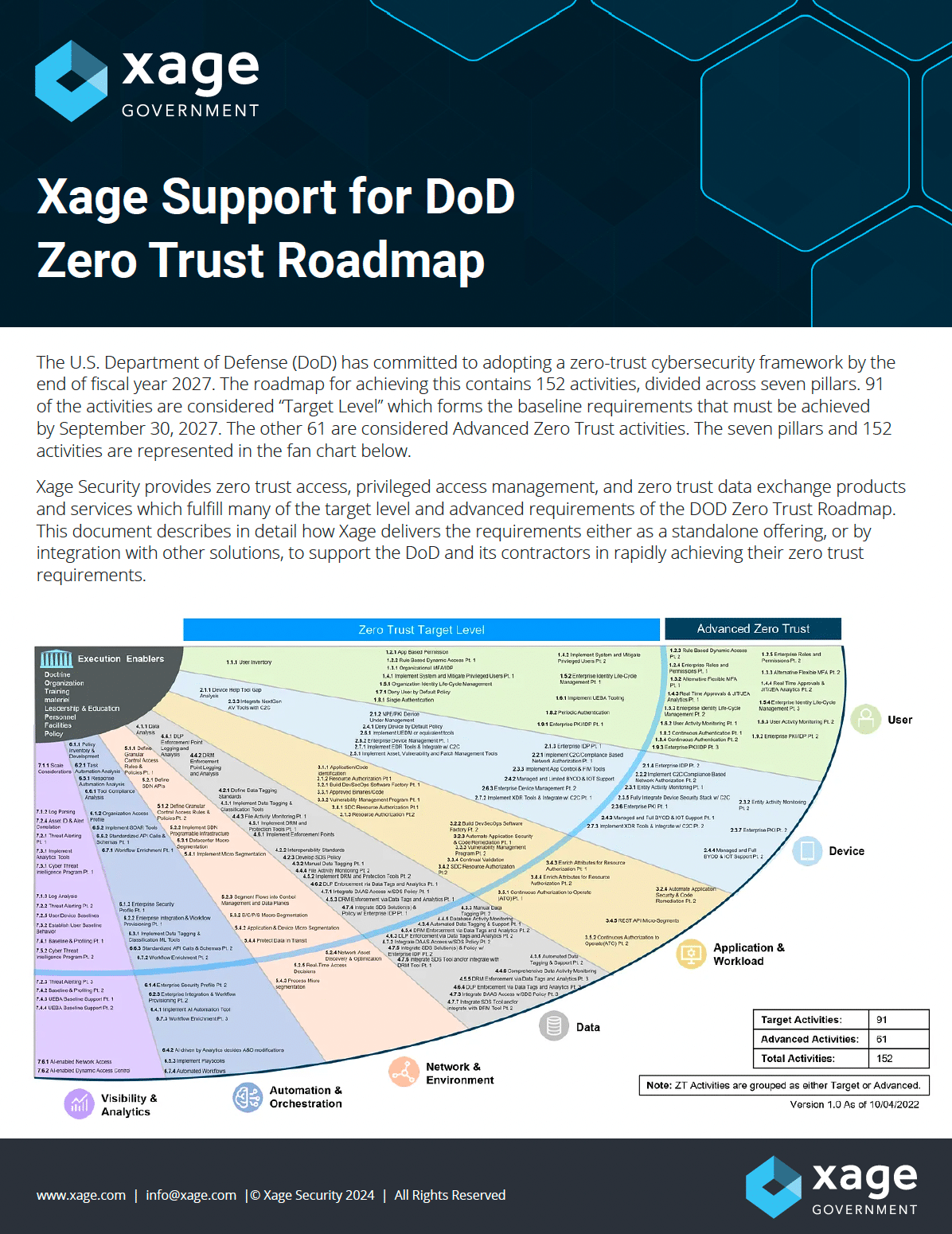
REPORT
Xage Support for DoD Zero Trust Roadmap
Download the technical brief for detailed descriptions of Xage’s support or applicability to each activity and function, for a total of 90% full or conditional support.
Resilient Zero Trust Cyber Hardening to Support the Mission
Xage delivers secure information sharing and cyber hardening across the modern battle environment. Xage is a highly available, cyber resilient platform that enables central policy creation and distributed enforcement, even in scenarios with denied, disconnected, intermittent, or low-bandwidth connectivity (DDIL).
Key Cybersecurity Initiatives

Secure Cross-Domain Data Sharing
Xage enables secure, real-time information sharing across various units, organizations and allies, from the tactical edge to the strategic core to ensure operational dominance.

Integrated ICAM with Continuous Authentication
Xage controls access to every asset across OT, IT, and Cloud, with zero-trust principles including least-privilege and continuous identity authentication and verification from the tactical edge to the strategic core.

Cyber-harden Modern and Legacy Operational Assets
Xage protects the full spectrum of legacy and modern systems with asset protection that is resilient, flexible, and highly available. Ensure mission security across all network types, applications, and devices.

Support JADC2 & Achieve DoD Zero Trust Strategy Requirements
Xage delivers zero trust asset protection and data security to enable zero trust security across OT, IT, IoT, and Cloud to meet and exceed the requirements in major Federal guidelines.

Xage Security Secures $1.5 Million Contract with the U.S. Navy to Accelerate Zero Trust Initiatives
How Xage Supports The Mission and Secures The Tactical Edge
The Xage Fabric delivers secure data sharing and identity-based access management , protecting every asset and assuring the confidentiality, integrity, and availability of sensitive data from the strategic core to the cloud to the tactical edge.
- Eliminate complexity across legacy and modern assets.
- Enable cybersecurity interoperability between devices, agencies, and allies.
- Protect every asset across interconnected OT, IT, IIoT, and Cloud.

“Xage is tackling one of our nation’s most urgent challenges – to cyber harden digital systems and critical infrastructure while protecting them against increasingly advanced cyber threats. Xage and SAIC help accelerate the adoption of Zero Trust principles throughout the Federal Government, using Xage’s technology to protect digitally transforming enterprises from cyber-attacks.”
Lauren Knausenberger, Chief Innovation Officer at SAIC