Author: Roman Arutyunov, Co-founder and SVP of Products, Xage Security

The CPGs were developed and released in coordination with the National Institute of Standards and Technology (NIST) and other agencies. The CPGs are being used as the foundation for more sector specific regulations driven by the Transportation Security Administration (TSA), the Environmental Protection Agency (EPA), and others. This is likely to drive a great deal of regulatory activity, including enforcement, and a shift in cybersecurity investment across all 16 critical infrastructure industries.
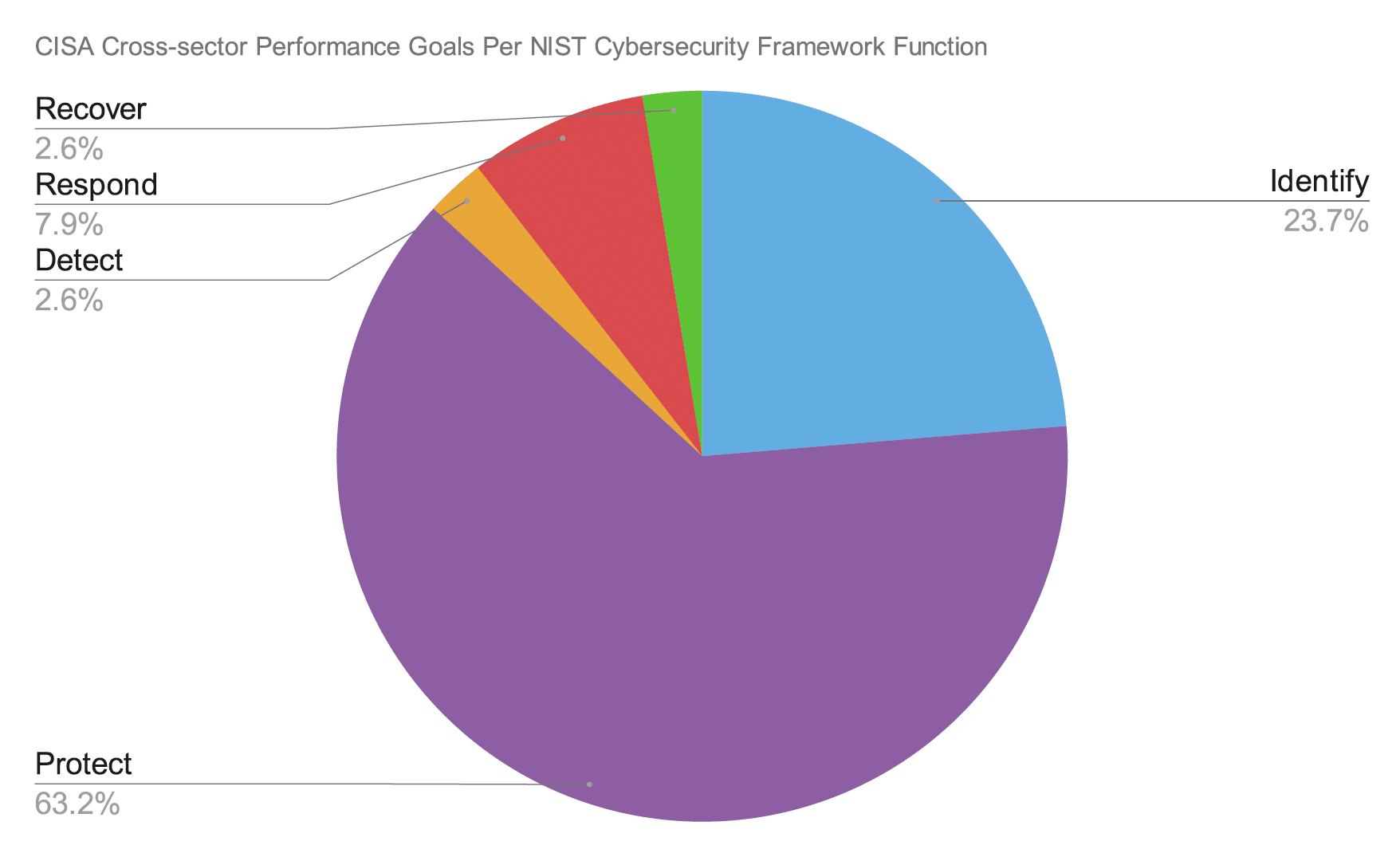
The CPGs Focus Heavily on Asset Protection
The CPGs were built with the goal of maximizing risk reduction in ways that are achievable across a wide range of organizations of any scale, in any of the critical infrastructure industries. While the CPGs are mapped to all five of the NIST CSF function categories–Identify, Protect, Detect, Respond, and Recover–the vast majority of CPG items fall into the Protect function. This is reflective of a broader trend in the cybersecurity field, where investment is being moved from detection initiatives to asset protection initiatives.
Top 10 Checklist for Achieving CISA Cross-sector Performance Goals
Here are the top ten actions you can take now to achieve the CISA Cross-sector Performance Goals in your organization, to defend your organization against the rapidly escalating threats targeting critical infrastructure.
1. Inventory ALL of your assets across OT, IT, and Cloud. Operational Technology has historically been insulated from risk by an airgap separating it from the public internet. The airgap is rapidly disappearing, and the risk of an unmanaged OT device providing attackers with a toehold to breach your environment is skyrocketing. Protection requires an asset-centric approach across OT, IT, and Cloud.
2. Get Your Identities and Credentials in Order. At least five of the controls in the CPGs are focused on securing identities and credentials. 80% of cyberattacks involve stolen credentials, so figuring out your identity and credential security has a huge impact on securing you against attack. A few of the most important steps to take are:
- Change default passwords. If you have devices that ship with default usernames and passwords, change those immediately, and bring those devices under a regime of credential management.
- Rotate credentials. There are many ways for credentials to be lost or stolen and to end up in the hands of a threat actor. Change credentials often, especially on critical assets.
- Stop sharing accounts. Often, privileged accounts are shared among employees and contractors to manage specific devices. While this may offer a way of reducing the total number of privileged accounts, it creates enormous risk if the shared privileged account falls into the wrong hands.
- Revoke credentials from departed employees. Every credential adds to your attack surface. Take every opportunity to reduce this.
- Separate user and privileged accounts. Basic everyday user accounts have different requirements than privileged accounts. Conforming to the zero trust principle of “just enough, just in time” access privileges reduces risk.
3. For Assets with no credentials, implement compensating and commensurate controls. Many OT assets do not have the inherent ability to authenticate access with credentials, but these still need to be secured. A cybersecurity mesh overlay can provide security for devices with no credentials.
4. Use Multi Factor Authentication (MFA) for access to every site and asset. MFA is one of the best ways to reduce risk of compromise due to stolen credentials. Attackers have developed techniques such as MFA-bombing to get around it, but defenders can prevent this with the right approach to MFA at multiple layers of your environment.
5. Secure Your Sensitive Data. This one sounds obvious on the face of it, but it deserves continuous re-examination in every organization. Keeping sensitive data encrypted, and behind multiple layers of defense, and requiring extra layers of authentication in order to access sensitive data, are increasingly urgent for critical infrastructure organizations.
6. Use Strong Encryption. TLS 1.3 and AES256 should be applied judiciously to assure the security and confidentiality of data at rest and in motion.
7. Limit OT Connections to the Public Internet. OT assets have historically been kept separate from the public internet by an airgap. Increasing needs for remote access and data sharing have eroded the airgap. Critical infrastructure organizations need to be extremely careful and intentional about controlling any mechanism that allows connectivity to critical assets. VPNs, Jump Boxes, and other remote access methods introduce new risks and complexities that must be managed. A new approach is needed to enable necessary access without exposing OT assets to the internet.
8. Collect and Store Logs. Many critical infrastructure assets may not have inherent logging capabilities. An overlay approach to controlling and logging access and activity on critical assets, especially OT, is necessary to secure and audit this activity.
9. Segment your networks at the most granular possible level. Lateral movement is a key step in any cyber attack. Once an attacker is inside your OT, IT, or Cloud environment, they will try to move laterally to compromise other assets. The effective way to combat this is to control machine-to-machine connectivity and to segment the network based on granular identities for every user and asset.
10. Mitigate Known Vulnerabilities. There are hundreds of new vulnerabilities being announced in assets commonly used across critical infrastructure. OT assets are often difficult or impossible to patch, but there are other options for mitigating these, including identity-based access control that applies at a granular per asset basis. An attacker can’t compromise a vulnerable asset if they can’t access it, or even see it in the first place.
How Xage Security Can Support Your CISA Cross-Performance Goal Journey
The Xage Fabric is a cyber-resilient, highly available cybersecurity mesh that protects your assets against attacks with a single platform across OT, IIoT, IT, and the Cloud. The Fabric delivers Identity-based Access Management, Zero Trust Remote Access, and Dynamic Data Security capabilities. It is deployed as an overlay on existing systems, meaning that these capabilities can be achieved without down-time or disruption to operations, and are effective even for legacy equipment that has no built-in security features or compatibility with modern security solutions.
Xage also offers a comprehensive assessment through our professional services team that helps organizations identify their current cybersecurity state and provides tailored recommendations for a more secure future state. By conducting a thorough risk analysis and evaluating the existing security posture, Xage’s expert team can pinpoint vulnerabilities, gaps, and areas of improvement. Leveraging deep understanding of industry best practices and the CISA Cross-sector Cybersecurity Performance Goals, Xage’s team of OT Cybersecurity Experts develops a customized roadmap that prioritizes security investments and outlines actionable steps to strengthen an organization’s defenses. This holistic approach ensures that companies not only address immediate concerns but also establish a robust, long-term cybersecurity strategy that evolves with the ever-changing threat landscape.
For a thorough breakdown of the CISA Cross-sector Performance Goals, and how Xage supports all of your needs for each of the controls, request our white paper: How Xage Supports the CISA Cross-Sector Performance Goals for Critical Infrastructure.
Related Resources
Top 10 Checklist for Achieving TSA Guidelines for Oil & Gas Operators
Top 10 Checklist for Achieving TSA Guidelines for Passenger and Freight Railways
How Xage Supports the Saudi National Cybersecurity Authority’s OT Cybersecurity Controls










