A high-value PAM solution that provides protection on day one, is simple to use, and extends coverage across the whole enterprise and every asset, including semi-privileged assets, multi-cloud and hybrid environments, and even the operational edge.
Extended Privileged Access Management
Legacy PAM Solutions Are Failing
Legacy PAM solutions are not providing enough value for the cost, eating up budgets while not giving the full protection necessary for enterprises to stop increasingly sophisticated attackers who are exploiting the complexity of modern environments.
Introducing Xage XPAM

Better Total Cost of Ownership
More protection without eating your whole budget

Eliminate Complexity
Easy to deploy, manage, and use

Innovative Technology
Its resilient architecture sets Xage apart
“Legacy PAM deployments can resemble a slow crawl up a mountain as new applications and accounts accumulate over time. Xage turns that around by starting at the mountaintop. Xage is designed to cover an enterprise’s critical mass of assets on day one and offers simplified manageability for optimal enterprise value over time.”
Todd Thiemann, Senior Analyst
Enterprise Strategy Group (ESG)

SOLUTION SHOWCASE
Changing the Privileged Access Management Game With a Protection-first Approach
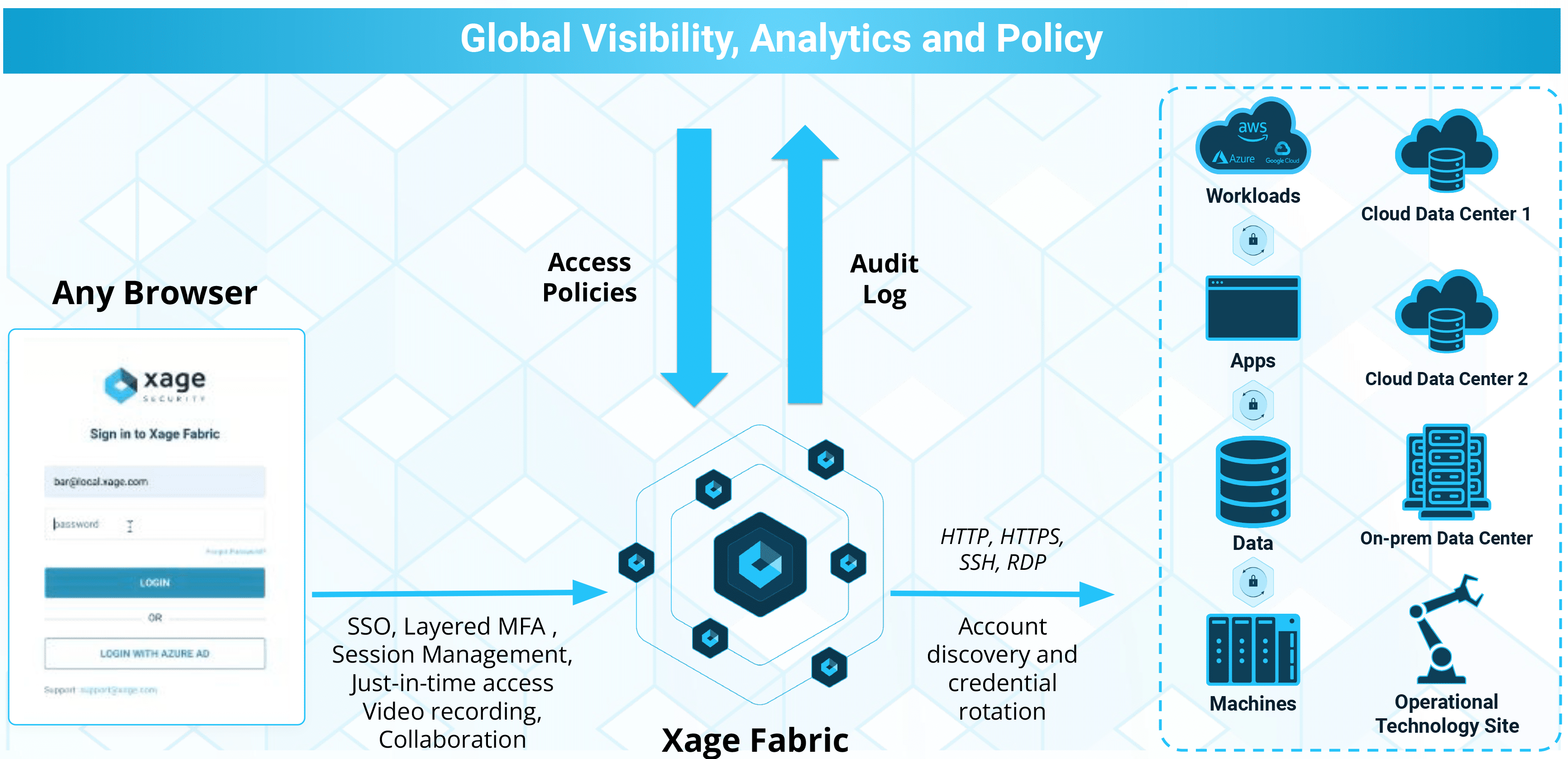
Xage Extended Privileged Access Management (XPAM)
Xage is extending PAM to cover three critical areas where it currently falls short.
We’re expanding what counts as privileged. PAM was created because there were certain accounts that, if compromised, gave attackers the keys to the kingdom. But we’re seeing more sophisticated attackers exploiting “non-privileged” user accounts in creative ways. These accounts need protection just as much as privileged accounts.
We’re expanding to protect more than just accounts. Why do we have separate security controls to protect assets (like apps, machines, and devices) vs. accounts? There are many assets within your infrastructure that are capable of interacting with the network, meaning they can be exploited by hackers. They aren’t protected by legacy PAM, even though they can represent the same risk as privileged accounts.
We’re expanding and simplifying coverage. Xage works across IT, operational technology (OT), and cloud and it’s the same solution whether in the cloud or onsite.
“The risk of users with excessive as well as standing privileges remains high, even with PAM tools in place. Identity and access management leaders must implement just enough privilege and just-in-time strategies to minimize the risk of standing privileges.”
May 2025 Reduce Risk Through a Just-in-Time Approach to PAM

Download the Gartner® Report
Reduce Risk Through a Just-in-Time Approach to PAM

PAM That Won’t Eat Your Whole Budget
Xage’s unique architecture provides better security that gives protection starting on day one and protects more: privileged accounts, regular user access (and other identities), and everything in between.
- Protects assets, devices, and environments like OT that aren’t covered by legacy PAM
- Highly responsive customer support team
- Saves money by being easier to use and manage

A PAM Approach That Flips the Script
Most PAM requires complex setup (identifying privileged accounts and defining policies) before protection starts. Xage immediately acts as a layer between users and what they’re accessing.
- You don’t have to wait on the endless cycles of account discovery and management to see real protection
- A single solution that works across on-premises and cloud
- Comprehensive PAM, MFA, SSO, and session recording & management

Innovative Architecture Improves Security and Is Easier to Use
Xage has a unique and modern resilient architecture that enables it to provide security that’s both easier to use and harder for adversaries to compromise.
- Control of credentials and policy enforcement in Xage is decentralized, creating stronger security posture
- A more modern and resilient architecture means better protection of all credentials
- A quantum-proof credential vault
Zero Trust PAM
Xage’s innovative architecture provides privileged access management that follows a zero trust approach to protect cloud, IT, and OT environments without any disruption of existing systems.
What Makes Xage XPAM Different?

Xage provides the fastest time-to-value
Xage allows customers to realize the full value of PAM rapidly across their entire enterprise and get more value for their money.

Protection on day one
Xage immediately creates a layer between users and assets, securing access. You don’t have to wait to discover every privileged account and define every policy before your environment is protected.

No single point of security failure
Control of credentials and policy enforcement in Xage is decentralized and extremely secure. Nodes check in with each other and use consensus to validate the authenticity of the request. Legacy PAM has a central vault and central policy enforcement which, if compromised, is game over.

Better for multiple self-managed sites
Deploying Xage across multiple self-managed sites and even hybrid cloud is fast and easy since each node automatically inherits policy, user, and credential data from other nodes. With legacy PAM you have to either connect everything to the cloud or run completely separate deployments that you have to manage individually.

Secure zones
Xage allows you to create deeper layers of higher security. It provides session termination between layers with additional validation using multi-layer MFA. So you can protect and isolate secure datacenters or sensitive resources like vaults, databases, or critical OT assets from less-secure or internet-connected infrastructure.
Offline functionality
Xage still works when offline.
Get More With the Complete Xage Platform
Comprehensive Accounts Discovery and Management
Enable automated accounts discovery and password rotation. Store all secrets and passwords in a quantum-proof and distributed password vault that can span across IT/OT/Cloud.
- Perform account operations such as account check-in/check-out, account reconciliation, password verification etc.
- Out-of-the box accounts discovery and password management plugins for Windows, Linux, Active Directory, config files, ESXi, PAN firewall, SQL server
- Extendable plugin architecture that can be used to write custom plugins to program and execute advanced automations and workflows
- Zero trust policy management between users and privileged accounts
Remote Privileged Access
Enable remote and local access while exerting granular access controls to stop lateral movement and living-off-the-land tactics. Xage eliminates the complexity of implementing clunky, agent-based PAM, firewall rule management, VLAN/ACLs, and other compensating controls.
- Enforce MFA, credential rotation, and SSO for every resource
- Enable remote access to any device—no VPN, agent, or client needed
- Simplify privilege management, password management, and revocation for users, including third parties
Achieve Layered Zero Trust Security
Xage’s multi-hop architecture allows for deployment in multi-layer networks eliminating the need to poke holes through firewalls and provides session and protocol termination at each layer.
- All accounts and policies are easily managed and enforced across the entire enterprise
- This includes any type of asset including IoT/OT devices that do not have credentials
- An MFA overlay is provided as an option at each layer and asset without added complexity or friction for the remote user
Prevent Cyberattacks
Defenders must adopt defensive strategies as dynamic as the threats they face to safeguard organizations effectively. Xage controls access to prevent privileged accounts and living off the land techniques from being weaponized against your enterprise.
- Enable user-to-machine and machine-to-machine access control to limit attack blast radius
- Secure file transfer between users and IT assets stops malware and ransomware from spreading
- Tighten security with just-in-time access, session monitoring, and more






