Resilient, highly-available cybersecurity mesh for zero trust access and protection.
Xage Fabric Platform
Benefits of The Xage Fabric Platform Architecture
The Xage Fabric Platform is a resilient, highly available cybersecurity mesh that underpins all Xage Security products and solutions. The unique architecture of the Fabric enables Xage to deliver zero trust access and protection, combining the best capabilities of ZTNA, PAM, and segmentation into a single solution that covers OT, IT, IIoT, and the cloud.
Distributed Mesh Overlay for Security and Compatibility
- No single point of failure. No single point to hack
- Distributed password vault prevents credential theft and abuse
- Deployable at every layer of an environment to enable granular protection, authentication, and policy enforcement across layers
- Multi-factor authentication at every layer, and even per-device

Fast, Frictionless Deployment, Anywhere
- Xage Fabric nodes can be deployed on premises, in the cloud, and at remote sites to grant immediate access, authentication, and protection
- Mesh overlay architecture means you don’t have to change your firewall rules or network routing
- Works across all types of assets, regardless of their native security, from legacy OT to cloud workloads
- No downtime to deploy or upgrade, since Fabric Nodes can take over for each other if one or more is disconnected
No Cloud Connection? No Problem
- Distributes credential and policy information across nodes, so you can still authenticate and enforce policy even if your site goes offline
- No cloud dependencies for enforcing zero trust, unlike others that require a cloud connection to broker trust
- Shamir’s Secret Sharing and Federated Byzantine Agreement keep your data synced even if some assets go offline periodically
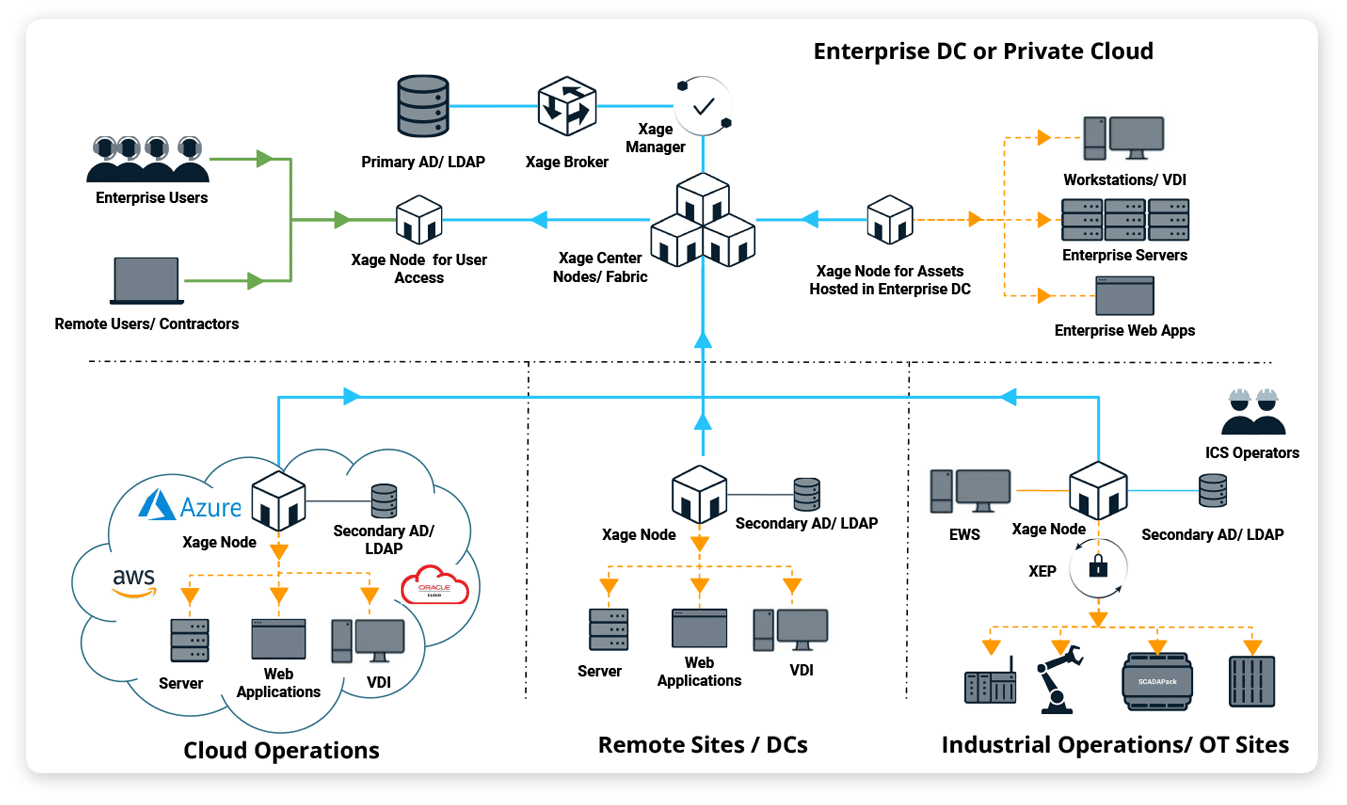
What Is the Xage Fabric Platform, and How Is it Deployed?
The Xage Fabric is overlaid on top of your existing environment architecture without requiring any network changes, rip-and-replace, or installation of any endpoint agents or clients.
Xage Nodes are deployed as VMs or containers and managed centrally from a browser. Then policy is enforced locally at distributed sites, and even down to individual assets.
The Fabric’s cybersecurity mesh architecture means there is no single point to hack, making the Fabric itself secure.

WHITEPAPER
Explore the power and simplicity of Xage Zero Trust Access.
Solutions and Use Cases Supported by Xage Fabric
The Xage Fabric’s unique architecture enables us to deliver multiple business-critical solutions and use cases in a single, resilient and rapidly-deployed platform.