Protect distributed energy resources, cyber harden systems, and meet compliance mandates with identity-based access management and data security from Xage Security.
Zero Trust Cybersecurity for Clean Energy
Leading Clean & Renewable Energy Organizations Trust Xage




Clean Energy Industry Challenges
Demand for clean and renewable energy shows no sign of slowing. As the growth of installed capacity accelerates globally, so do the challenges facing owners and operators scaling their operations to keep pace.
- Rising cost of installation
- Supply chain risks
- Growing regulatory pressures
- Cost-effective energy storage
Utility-scale energy producers continue to benefit from hundreds of billions in new investments. However, meeting aggressive decarbonization targets places enormous stress on cybersecurity safeguards.

U.S. Department of Energy’s National Renewable Energy Laboratory Selects Xage for Clean Energy Cybersecurity Program.
From Fluctuating Sunshine to Sophisticated Cyber Threats

Widely-distributed assets must be defended from costly cyberattacks and nation-state threat actors

Power generation and storage infrastructure must comply with mandates to avoid interruptions and fines

Automation and digitalization must be embraced to reduce maintenance overhead and boost profits
Rapid Growth Requires Rethinking Cybersecurity
Energy operators often rely on IT-centric tools to meet demands for secure access to the distributed infrastructure that underpins energy generation and storage. However, IT-centric tools cannot natively secure Industrial Control Systems (ICS), leading to security gaps. These gaps, magnified across interconnected OT, IT, and cloud environments, create ideal circumstances for cyberattackers and failed regulatory compliance.
No utility-scale energy operator can afford a weak cybersecurity posture.
Modernize without Compromise
You can protect your operations from escalating cyberattacks and reduce regulatory burdens without impacting digitalization. It starts by modernizing secure access to vital operational technology assets using an approach grounded in zero trust principles.
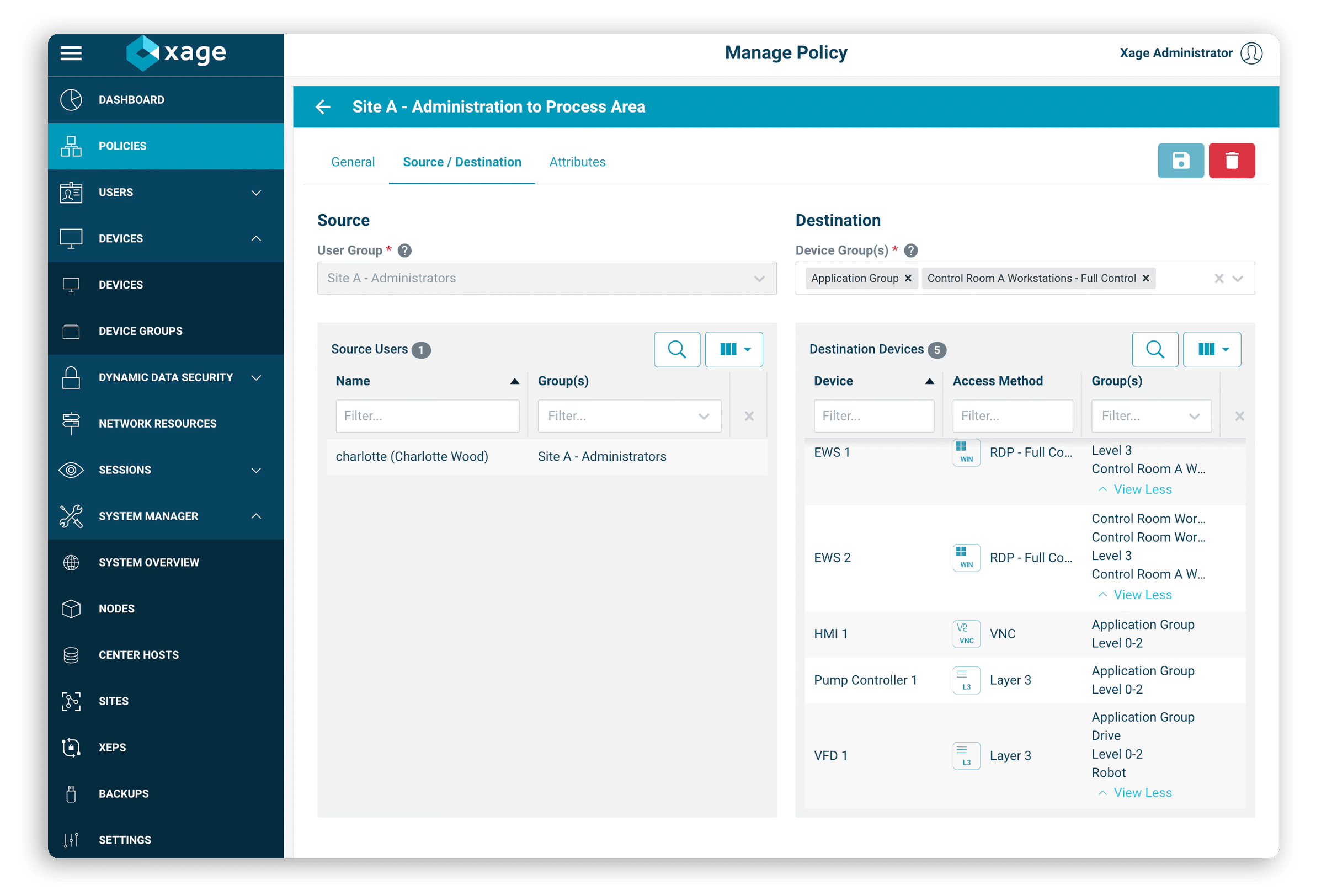
Achieve Zero Trust Access with Xage
Xage accelerates the adoption of zero trust identity-based access management for energy owners and operators.
The Xage Fabric is purpose-built for operational technology and securing the OT-IT-Cloud interconnected environments commonplace in clean & renewable energy deployments. Its identity-centric approach reduces the complexity of real-time, multi-party secure access to energy generation and storage assets. With Xage, your security teams can enact granular, just-in-time access controlled down to the asset level.
The unique mesh architecture removes any need to rip and replace your current investments or jeopardize productivity to protect your OT, IT, and cloud infrastructure.

WHITEPAPER
Unified Zero Trust Access and Protection for Operational Technology (OT) and Cyber Physical Systems (CPS)
Download for a technical deep dive and deployment architecture.
Zero Trust Cyber Hardening to Protect Clean Energy Sources
Xage delivers proactive protection to address your cybersecurity initiatives. Xage Fabric strengthens your operational cybersecurity posture to safeguard critical assets anywhere you generate and store clean energy.
Key Cybersecurity Initiatives

Secure Multi-Party Remote Access
Enable secure and efficient remote access for third-party partners to maintain distributed operations. Xage Zero Trust Remote Access simplifies and secures access to and through OT-IT DMZ.

Cyber Harden Critical Infrastructure
Simplify strengthening the cyber-physical security posture of your distributed energy resources. Xage eliminates the complexity of implementing credential management and password rotation for devices and applications.
Protect OT/IT Interconnectivity
Securely interconnect operational assets and data with modern, cloud-based systems to gain new efficiencies. Xage multi-hop architecture preserves logical segmentation to protect all digital interactions and data transfers between devices, applications, and users.

Meet Regulatory Mandates
Speed up compliance with industry standards, risk management frameworks, and cybersecurity mandates, such as NERC-CIP, ISA 62443, and NIST 800.






