Day-One Protection Across IT, OT, and Cloud with Extended Privileged Access Management
Author: Vishal Gupta, VP of Product Management, Xage Security
The digital landscape has evolved significantly, with a notable increase in both the sophistication and frequency of attacks on enterprises. Protecting identities, assets, and data are the top priority rather than accounts. Privileged Access Management (PAM) has been a cornerstone of enterprise cybersecurity, safeguarding critical systems by limiting access to privileged accounts. However, as cyber threats evolve and cloud adoption accelerates, legacy PAM solutions are struggling to keep pace. Enter Xage XPAM—a next-generation PAM solution designed to address the complexities of modern cybersecurity.
In this blog, we’ll explore the limitations of legacy PAM solutions and explain why Xage XPAM is the preferred choice for comprehensive, agile, and future-proof access management.
The Challenges with Legacy PAM Solutions
While PAM has long been essential to cybersecurity, legacy PAM solutions have significant drawbacks. Legacy PAM vendors like CyberArk, BeyondTrust, and Delinea, have dominated the market with outdated approaches that are failing today’s enterprises. Here’s where legacy PAM falls short:
- Lengthy Deployment Times: Legacy PAM systems can take months to deploy, delaying critical protection and consuming valuable resources. Discovering all privileged accounts is cumbersome and sometimes never-ending, further delaying protection. In the modern threat landscape, enterprises cannot afford to wait months to start protecting their valuable data and assets.
- Limited Coverage: Legacy PAM focuses solely on privileged accounts, leaving other accounts and assets vulnerable. These accounts and assets need protection just as much as privileged accounts. Additionally, legacy PAM fails to cover all account types and assets, particularly in mixed IT/OT and legacy environments. As cybercriminals target both privileged and non-privileged accounts from across the entire enterprise, this limited focus leaves a significant gap in enterprise security.
- Centralized Risk: Legacy PAMs rely on a centralized vault for credentials and secrets storage. There is also increased reliance on cloud connectivity. If connection drops, or if the vault goes offline or is compromised, it leads to a total security breakdown—an unacceptable risk in critical operations.
- Complex Management: With hybrid environments becoming the norm, integrating on-premises and cloud-based systems is often complex and costly. Legacy PAM solutions hinder quick user adoption, creating friction and inefficiencies, sometimes even forcing users to bypass the PAM solution.
- High Total Cost of Ownership: Legacy PAM vendors continue to increase the cost of their offerings, despite delivering products that are cumbersome and complex to manage. Maintaining legacy PAM systems requires continuous professional services, which can also eat into cybersecurity budgets – leaving enterprises with high total cost of ownership. Furthermore, the lengthy deployment and discovery phases lead to not only slower time-to-protection, but slower time-to-value as well.
These limitations leave organizations exposed to cyber threats, such as ransomware and unauthorized lateral movement. Legacy PAM solutions are no longer sufficient for today’s security challenges. For a detailed comparison of capabilities, check out our competitive brief: Xage XPAM vs Traditional PAM.
Xage XPAM is Changing the Future of PAM
Xage’s Extended Privileged Access Management (XPAM) redefines what PAM can achieve by addressing the gaps left by legacy PAM solutions. Let’s look at how Xage XPAM is revolutionizing PAM:
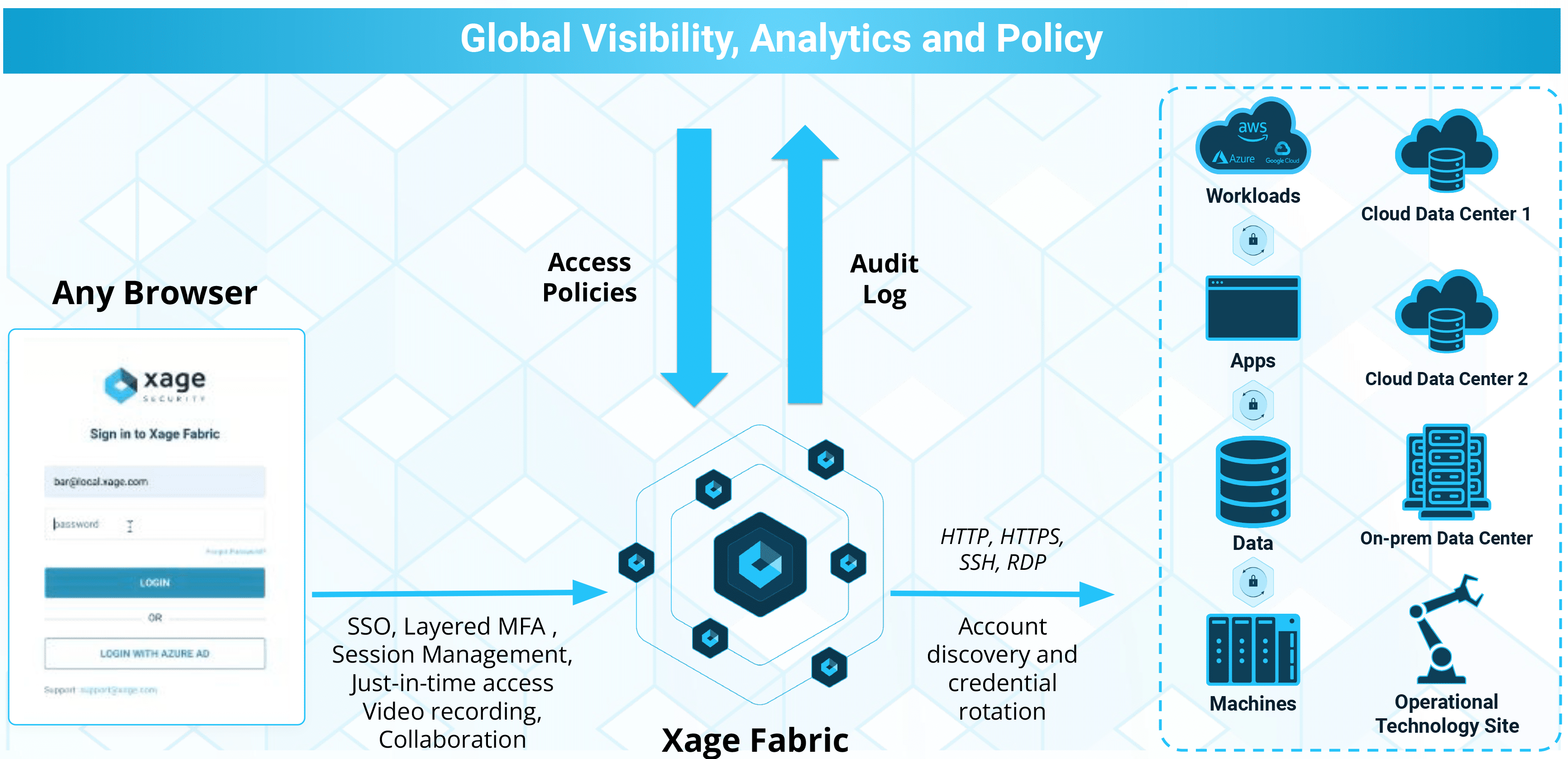
- Asset Protection from Day One: Xage XPAM protects all assets, simplifying asset management and security before a single privileged account is discovered and onboarded. Xage immediately creates a layer between users and assets, managing access. Protection is applied immediately to all assets for all interactions including user-to-machine, user-to-app, and machine-to-machine, even before discovery of privileged accounts begins, providing protection immediately.
- Comprehensive, Enterprise-Wide Protection: Every user, account, and asset—whether on IT, OT, or cloud platforms—is protected from the outset with Xage XPAM. This holistic approach closes the gaps left by legacy PAM and significantly reduces major risks.
- Resilient Architecture, Future-Proofed Against Quantum Threats: With the rise of quantum computing, legacy encryption methods are at risk. Xage XPAM addresses this by offering a distributed quantum-proof vault eliminating any single point of failure, thus ensuring that your enterprise is protected against quantum-based attacks. Its architecture scales horizontally, adapting to an organization’s growth without major overhauls or added costs.
- Better for multiple self-managed sites: Deploying Xage across multiple self-managed sites and even hybrid cloud is fast and easy since each node automatically inherits policy, user, and credential data from other nodes. With legacy PAM you have to either connect everything to the cloud or run completely separate deployments on-premises that you have to manage individually.
- Operational in DDIL Scenarios: Xage XPAM maintains the operation of its Privileged Identity and Access functions even in denied, disrupted, intermittent, and limited impact (DDIL) environments. In other words, access and privilege zero trust policies can still be enforced even if a remote site, data center, or edge containing Xage Fabric nodes loses connectivity to the central network.
- Advanced Security Features for Enhanced Protection: Xage XPAM includes layered multi-factor authentication and MFA, single sign-on (SSO) to a vast variety of targets – eradicating a need for static and shared credentials or privileged accounts – privileged session management and recording, just-in-time access, and secure file transfer and sharing. Xage XPAM exists within the broader Xage Fabric Platform, which offers security capabilities that are superior to those offered by legacy PAM, supporting multi-user session collaboration, non-existential cloud dependency, and secured privileged access over multi-hop encrypted tunnels across contested networks – leading to an extensive reduction in the risk of unauthorized access.
Solving Modern PAM Challenges: Cloud, Identity, and Authorization
As enterprises move to the cloud, legacy PAM solutions are increasingly obsolete. According to Gartner, by 2025 over half of IT spending will shift to public cloud services, highlighting the need for PAM solutions that can handle cloud-native challenges. In cloud environments, identity and authorization have become crucial aspects of access management.
Instead of managing static credentials, Xage XPAM is designed for dynamic environments. It embraces just-in-time (JIT) permissions, a model that grants users temporary time-bound access when they need it, for as long as they need it and no longer. By avoiding permanent “birthright” access, Xage XPAM reduces exposure to threats and prevents over-permissioned accounts from becoming security liabilities.
Xage XPAM’s JIT access approach not only strengthens security but also eases compliance. By making sensitive roles and permissions ephemeral, Xage XPAM reduces the administrative burden of compliance by requiring users to re-request or justify access every time. This helps companies identify and remove unneeded permissions while maintaining a robust audit trail.
The Bottom Line: Invest in Future-Proof Security with Xage XPAM
If your organization is grappling with the limitations of legacy PAM and seeking a solution that meets the demands of today’s cloud-driven, hybrid environments or fully air-gapped networks, Xage XPAM offers a clear path forward. With its enterprise-wide coverage, rapid deployment, resilient architecture, advanced security features, and quantum-proof vault, Xage XPAM represents the next generation of privileged access management.
By using Xage XPAM, you’re not just securing privileged assets, you’re securing the future of your enterprise. It’s time to leave behind the inefficiencies of legacy PAM and embrace a solution built for the complexities of modern cybersecurity and advanced threats.
If you’re ready to revolutionize your approach to privileged access management, consider Xage XPAM and experience comprehensive, agile, and future-proof security. Book a conversation with a Xage expert to discuss if XPAM is the right solution for your organization.
“Legacy PAM deployments can resemble a slow crawl up a mountain as new applications and accounts accumulate over time. Xage turns that around by starting at the mountaintop. Xage is designed to cover an enterprise’s critical mass of assets on day one and offers simplified manageability for optimal enterprise value over time.”
Todd Thiemann, Senior Analyst
Enterprise Strategy Group (ESG)

SOLUTION SHOWCASE










