Author: Roman Arutyunov, Co-Founder, SVP Products, Xage Security
Many organizations with industrial control systems (ICS) and operational technology (OT) in place are going through rapid digital transformation. They are driven to increasing the amount of network connectivity between their OT, ICS, IT, and Cloud systems in order to enable process automation, collaboration, data-driven optimization, and remote access, to stay competitive in a challenging market.
This is forcing them to make new decisions about the overall architecture of their environment and the flow of information between their systems. Historically, ICS/OT systems were secured via air gapped architectures, but this is no longer compatible with the current realities of industry.

First, it must be said that no security tool alone can create a defensible architecture. A defensible architecture is created through many structural decisions, tool deployments, and effective work by humans. SANS puts eloquently, “It is the human element that allows a defensible architecture to become a defended architecture.”
However, every security tool or platform in your environment either strengthens or weakens your security architecture. Every tool either increases or decreases the defensibility of your environment. As we have demonstrated before, many ICS/OT environments use a combination of VPNs, jump servers, and firewall rules to enable remote access in ways that require the organization to actively increase their attack surface and reduce the defensibility of their architecture by poking holes in their existing security posture!
What Is A Defensible Architecture?
There is plenty of room for discussion and expansion on the concept, but for the purpose of this post we are going to quote SANS’ whitepaper as referenced above:
“A defensible architecture is an architecture that reduces as much of the agreed-upon risk as possible through system design and implementation while also facilitating the efforts of human defenders.”
SANS goes on to identify several common attributes of defensible architecture. The table below includes direct quotes from SANS on the left, and how Xage supports each attribute on the right.
SANS’ attributes of defensible architectures
How Xage Supports this attribute
Asset identification and inventory for at least the crown jewels of the key sites.
Xage Fabric automatically and continuously discovers and categorizes IT and OT assets, as well as all the interactions between assets and users to build the asset inventory and identify process and network interdependencies. Xage is uniquely capable of discovering assets and interaction deep within the OT network without reliance on SPAN or TAP ports.
Xage’s asset-centric approach enables the operators to easily identify and designate Critical Cyber Systems (or groups of systems) as protected assets to focus enforcement of security policies on these critical assets. Xage also enables the operators to gradually extend the security protection to the remainder of the assets. Xage also integrates with a variety of existing asset management solutions to enrich the inventory data where appropriate.
Segmented environments where possible to reduce ingress and egress into as few pathways as possible, ultimately creating “choke points” for enhanced security and monitoring.
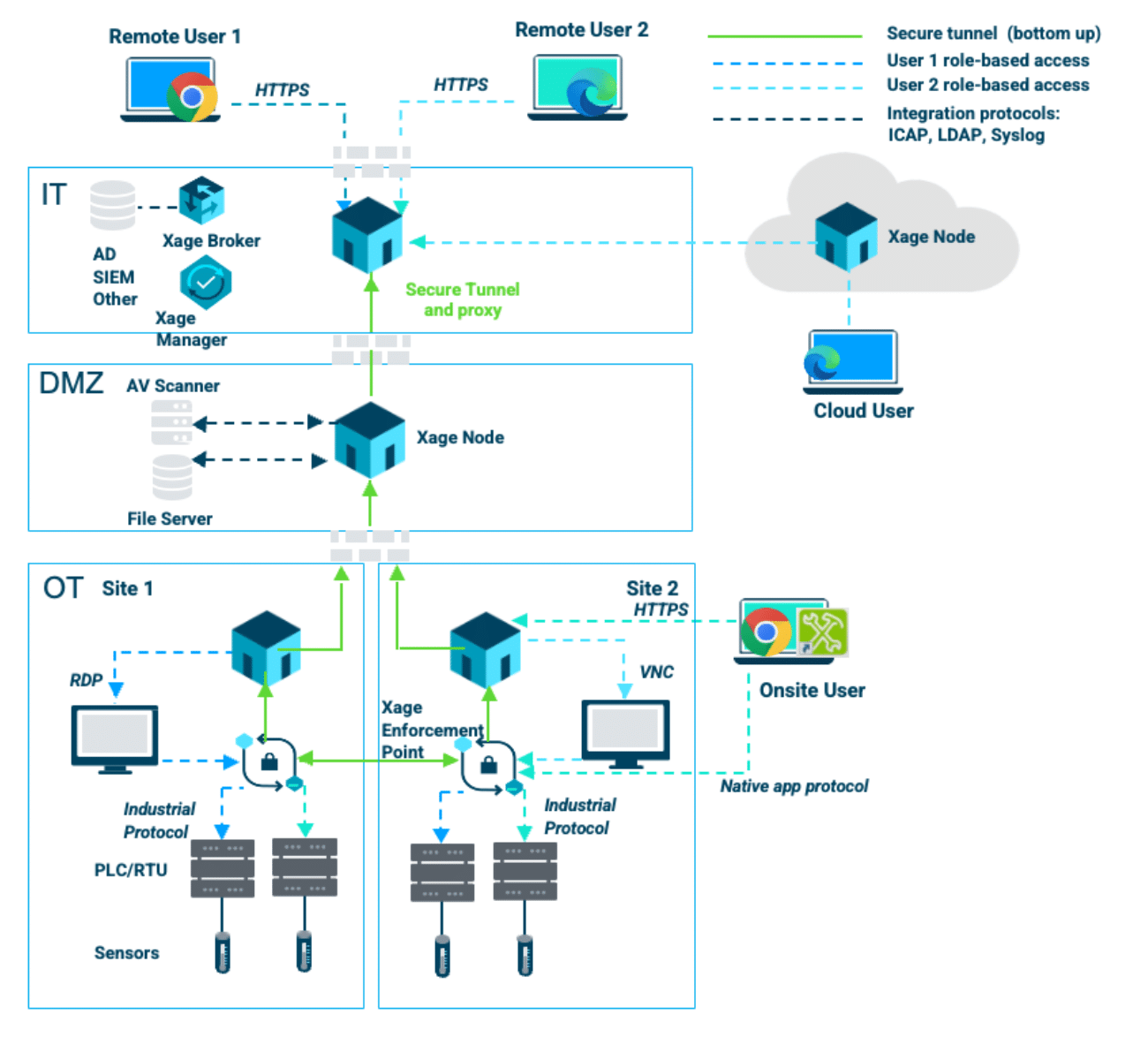
Xage Fabric enables asset-centric zero-trust segmentation. Groups of assets can be defined in the Xage Manager on a per-site, per-function, or Purdue-Model-layer basis. Once Xage Nodes and Xage Extended Protection are deployed in various locations, the zero-trust segmentation is enforced for all interactions, vertical (North-South) and horizontal (East-West), without requiring complex VLANs and firewall rules. These segmentations can be dynamically changed by simply adjusting the policy on the Xage Manager. Furthermore, enforcement occurs on individual asset identity and interactions basis. Enforcement is not just site-to-site and zone-to-zone, but is on a per-asset basis. You can control control of which asset in site one may communicate to another specific asset in site one or site two, and so on. Xage Fabric nodes deployed at various levels (IT, iDMZ, and/or various OT levels) also offer protocol breaks with malware scanning integration. This eliminates the complexities and vulnerabilities associated with jump box and firewall management.
Determining when bi-directional access is needed, both now and in the future vs. truly read-only applications.
– For example, air gaps are not realistic in almost all environments outside of nuclear power plants. Modernization efforts and data access requirements significantly limit the ability of data diodes to be deployed across many sites. Data diodes can be successful in specific use cases, however, such as remote diagnostics monitoring of gas turbines where no other control or return access is required. In most organizations, a switched network and proper application of firewalls are common.
Xage Fabric enables granular controls over all interactions based not only on the direction, but also on the function, role, location, and other characteristics of the interaction and participating assets. These controls can be applied granularly on a per asset, user, or group basis. Policies are defined centrally and enforced across the operation where Xage Fabric is deployed. Policies can also be adjusted dynamically, greatly simplifying new asset introduction and incident response activities.
Ability to collect network traffic and systems communication, such as managed network infrastructure with switched port analyzer (SPAN) ports or tap infrastructure.
Xage Fabric collects and monitors network traffic utilizing SPAN and TAP ports where available. Alternatively, Xage can be deployed as “bump on the wire” utilizing a small form factor Xage Extended Protection (XEP), which is especially useful when no SPAN or TAP ports are available. This is typically the case for lower levels where actual assets such as PLCs and RTUs reside.
Log collection from systems of value such as host-based log collection on HMIs and EWS, Sequence of Event logs from supervisory systems, and event and access logs from industrial equipment that supports it such as Syslog from PLCs.
Xage Fabric deploys as an overlay to protect access to IT and OT assets such as servers, PLCs, HMIs, EWS, and others, enabling identity-based access control and interaction visibility where it was previously impossible since most assets do not have a concept of accounts and identities. Xage provides information about which users interacted with which assets, when, where, and how. All interactions including failed or repeated login attempts are logged in tamperproof audit logs and forwarded via syslog and other methods to SIEM systems.
Ability to go into a “defensible cyber position,” where enhanced connectivity and devices unnecessary for constrained operations are reduced during heightened situations.
Xage Fabric provides the technical controls to quickly isolate assets and interactions during heightened situations. These policy changes can be implemented centrally using the Xage Manager and enforced across the distributed deployment of Xage Nodes to immediately enforce updated policies on all assets and interactions. Furthermore, Xage provides the controls to quickly isolate infected assets to contain the contagion so that operations can continue.
From Defensible Architecture to Defended Architecture
Organizations with ICS and OT environments are going through rapid change. This represents an opportunity for them to shift towards a defensible architecture and more effectively secure their critical infrastructure. This requires certain decisions to be made, both from an architecture perspective and a security tooling perspective. Selecting security tools that support defensible architecture rather than undermining is of vital importance.
Xage delivers multi-layer access management across OT, IT, and Cloud, even in ICS environments with many devices that have no built-in security capabilities, and cannot be patched.
Beyond that, Xage supports all the attributes of a defensible architecture, as well as the humans that must defend it. Learn more about Xage Security products here.