Cybersecurity Mesh for Zero Trust Access Management and Data Security.
The Xage Fabric is a cyber-resilient, highly available cybersecurity mesh platform that defends your assets against attacks across OT, IIoT, IT, and the Cloud.
Don’t just detect attacks. Stop them.
Benefits of the Xage Fabric Platform
Cyber-harden Modern and Legacy Assets
- Granular protection and multi-factor authentication down to individual assets.
- Block attacks from compromising assets and expanding laterally.
- No agents or client software required. No down time. No rip and replace.
- Mesh overlay protects any application, workload, device, and data across public cloud, private datacenter, and remote operational sites.

Asset Protection with Defense In Depth
- Multi-hop, multi-zone security
- Multi-factor authentication at every layer
- Identity-based segmentation, down to device level
- Control user-to-machine, user-to-application, application-to-machine, and machine-to-machine interactions
Highly Available, Highly Resilient
- No single point to hack – multinode consensus-protected data and policy
- Policy is still enforced even if a site loses outside connectivity
- Assures data integrity
- Underpins continuous operation
What Makes the Xage Fabric Different?

Go Beyond Threat Detection to Protect Your Assets
Xage Fabric doesn’t just detect threats, it protects your assets before they’re compromised.
The Xage Fabric prevents attackers from discovering and enumerating targets in your environment, escalating privileges, or moving laterally. By cutting off these key attack steps, Xage Fabric stops compromises.
Eliminate Blind Spots and Risky Implicit Trust Zones
The Xage Fabric eliminates blind spots and cuts out the need to use a patchwork of point solutions for identity management, access control (including secure remote access), privileged access management, and secure data transfer.
The Xage Fabric allows you to stop poking holes in your firewall and using VPNs and jump servers that expose your assets to the internet and your business to excessive risk.

Simplify Access and Improve User Experience
The Xage Fabric simplifies security administration by automating actions such as encrypted-tunnel configuration, identity-centric segmentation, credential management, workstation account management, and even policy creation, while also enhancing end-user experience by providing a unified interface for authentication and access, whether local or remote.
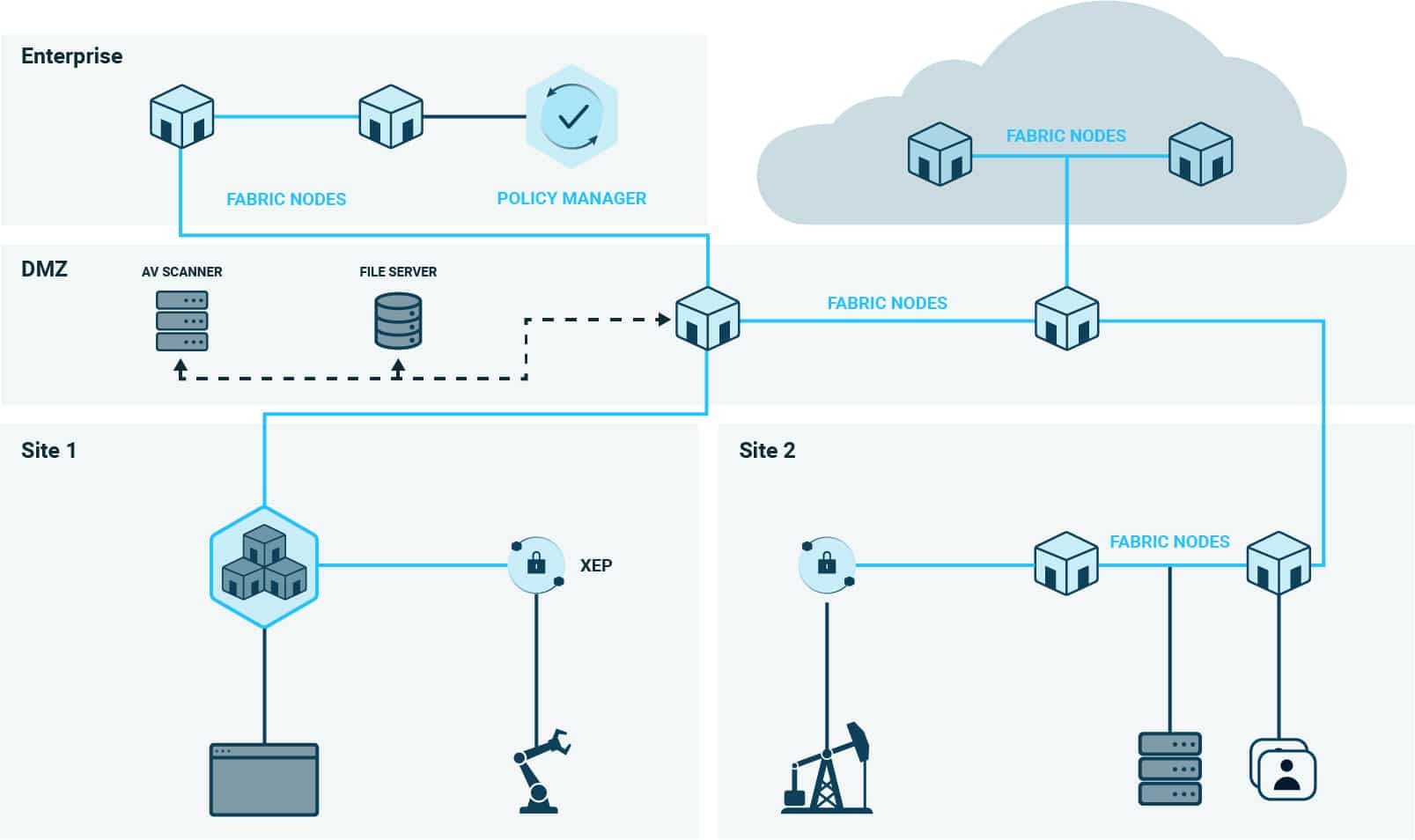
What Is the Xage Fabric Platform, and How Is it Deployed?
The Xage Fabric is overlaid on top of your existing environment architecture without requiring any network changes, rip-and-replace, or installation of any endpoint agents or clients.
Xage Nodes are deployed as VMs or containers and managed centrally from a browser. Then policy is enforced locally at distributed sites, and even down to individual assets.
The Fabric’s cybersecurity mesh architecture means there is no single point to hack, making the Fabric itself secure.
For a technical deep dive and deployment architecture, read our Xage Fabric Technical White Paper.
Products and Solutions Enabled by Xage Fabric
The unique cybersecurity mesh architecture and identity-based approach used by Xage Fabric allows you to achieve several key cyber-hardening use cases across IT, OT, and Cloud environments with no agents required. These capabilities are available even for legacy equipment with no built-in security features. It is managed through a single, browser-based console.

Zero Trust Access
- User-to-machine, user-to-application, and machine-to-machine control
- Multifactor and multilayer authentication
- Role-based access control per device and application
- Secure remote access across every app, workload and device
- Credential rotation
- Identity-based Segmentation
Zero Trust Privileged Access Management
- Simplify privilege management and provisioning
- Granular PAM for third-parties, vendors, and remote workers (RPAM)
- Complete audit of all remote-access activity
- Enforce least-privilege principles by default
Zero Trust Data Exchange
- Secure cross-domain data transfer with malware scanning
- Granular validation and access control
- Hash, sign, and encrypt data at source for any application, device, or protocol
- Define policy centrally, enforce locally at every site
- Assure data authenticity, integrity, and privacy across distributed sites
Technology Integrations
The Xage Fabric Platform delivers zero trust remote access and asset protection across your entire environment. We integrate with leading organizations across the OT, IT, and cloud cybersecurity ecosystem to deliver complete, frictionless protection that’s quick to deploy, simple to manage, and provides comprehensive coverage in the most challenging and distributed environments.
Featured Integrations

Discover and Protect Every Asset
This joint solution combines Nozomi’s advanced asset discovery with Xage’s robust security solutions, introducing a one-click asset inventory import feature that aligns with the MITRE ICS and NIST CSF guidelines.
- Discover every asset, managed or unmanaged, across your OT network.
- Rapidly enable Xage Zero Trust Access Control and Asset Protection across your entire environment to protect unmanaged devices.
- Combine granular access controls with rich asset details.

Discover Every Device and Detect Threats for Complete Security Coverage
Xage and Armis partner to provide complete visibility and attack prevention in the most challenging environments.
- Armis delivers asset discovery and inventory so you can know what you have—and protect it.
- Xage brings identity and access management for every device, even legacy assets, PLCs, and more.
- Xage brings MFA and SSO to every asset to ensure secure access anywhere.

Streamline Integration Among Critical Security and Operations Tools
Xage and Tines together make it simple to exchange access logs and trigger enforcement based on analysis across the full cybersecurity stack.
- Send and receive logs between Xage and SIEM solutions
- Trigger user suspensions via Xage access control based on threats detected by other solutions
- Simply integrate with the rest of your security tools to streamline attack prevention, detection, investigation, and response