By: Matt Heideman, VP of US Federal
In November 2022, the U.S. Department of Defense (DOD) released a Zero Trust Strategy and Roadmap to defend against increasingly sophisticated cyberattacks. The strategy defines a vision, key goals, and specific objectives for what the DOD will achieve, and how. This blog post will provide a brief overview of the DOD strategy, including how DOD defines Zero Trust, the goals laid out in the strategy, and the pillars of DOD Zero Trust capabilities.
While the strategy initially emphasized traditional IT systems, The DOD Zero Trust Strategy also indicates the need to accelerate zero trust adoption for cyber-physical environments. The DOD Zero Trust Portfolio Management office, which is tasked with synchronizing zero trust efforts across the DOD, will need to explore ways of securing operational technology (OT including industrial control systems and other cyber-physical devices), and converged OT-IT-Cloud applications in ways that go far beyond what is available from traditional IT cybersecurity vendors.
How Does The DOD Define Zero Trust?
In the introduction to the DOD Zero Trust Strategy, Zero Trust is defined as “an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources.” This definition is pulled directly from NIST SP 800-207.
The DOD Zero Trust Strategy document also offers this explanation of the Zero Trust Mindset:
“…every member of DOD must adopt a Zero Trust Mindset, regardless of whether they work in technology or cybersecurity or the Human Resource department. This “never trust, always verify” mindset requires us to take responsibility for the security of our devices, applications, assets, and services; users are granted access to only the data they need and when needed.”
The term zero trust was popularized by Forrester analyst John Kindervag over a decade ago, and rapidly gained popularity among cybersecurity vendors and practitioners. As the term grew in popularity, it became used in broader and broader ways, sometimes meaning different things to different people.
Now, as the DOD focuses resources on zero trust adoption their definition and requirements have the potential to bring greater specificity to the concept of zero trust, and to drive evolution in the technologies required to make zero trust a reality from the field, through IT to the cloud.
What are the Goals of the DOD Zero Trust Strategy
The four strategic goals defined in the DOD Zero Trust Strategy are as follows:
- Zero Trust Cultural Adoption: A Zero Trust security framework and mindset that guides the design, development, integration, and deployment of information technology across the DOD Zero Trust Ecosystem
- DOD information Systems Secured & Defended: DOD cybersecurity practices incorporate and operationalize Zero Trust to achieve enterprise resilience in DOD information systems.
- Technology Acceleration: Zero Trust-based technologies deploy at a pace equal to or exceeding industry advancements to remain ahead of the changing threat environment
- Zero Trust Enablement: DOD Zero Trust execution integrates with Department-level and Component-level processes resulting in seamless and coordinated ZT Execution.
What are the Pillars of DOD Zero Trust Capabilities
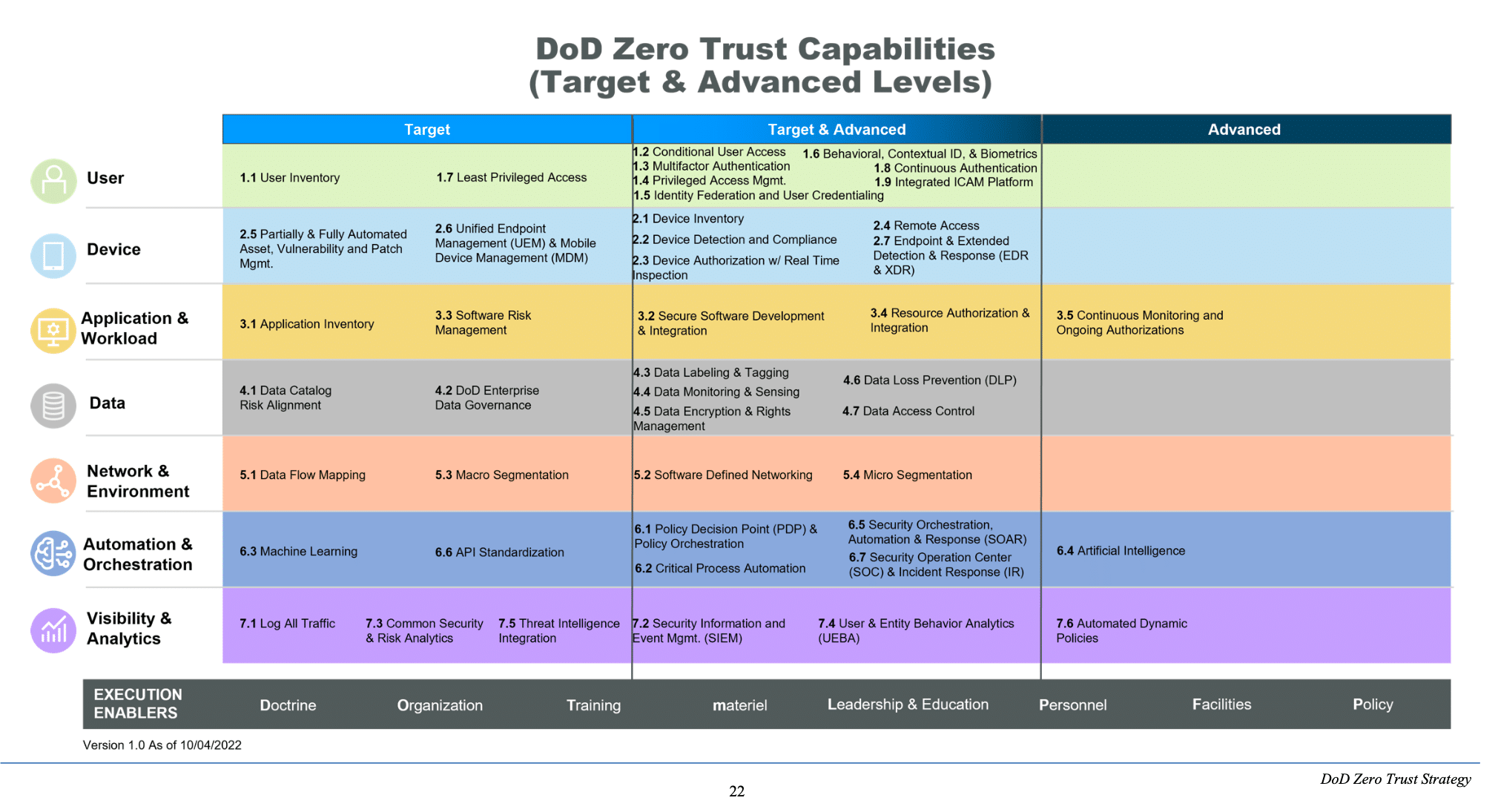
The DOD zero trust pillars are Users, Devices, Applications and Workloads, Data, Network and Environment, Automation and Orchestration, and Visibility and Analytics. The DOD Zero Trust strategy defines “target” and “advanced” levels of capabilities for each of these seven pillars.
One potential benefit that the DOD Zero Trust Strategy will have for the broader cybersecurity community is to provide common terminology and structure for discussing approaches to zero trust. We’ll save the deep-dive on each capability for a later blog post, but this table from the appendix of the DOD Zero Trust Strategy document gives an excellent window into the types of technologies and capabilities DOD considers vital for zero trust.
How The DOD Zero Trust Strategy Should Evolve for Mission Assurance
The initial DOD Zero Trust Strategy and goals are central to protecting IT systems supporting the overall mission. The next evolution of the DOD Zero Trust Strategy should extend into operational or non-traditional IT systems. ICS and OT underpin the mission from facilities and logistics depots, weapon systems, reconnaissance and situational awareness, ships and other warfighting equipment across land, sea and air, as well as launch and space-based systems that contain cyber-physical assets or mission sensors. While not traditional IT systems, these systems and operations are critical to warfighter and mission success and increasingly require services that span across cloud, IT, and operational environments. The rigor of zero trust approaches is needed end-to-end to prevent adversaries finding and compromising points of cyber weakness. The operational technology at the tactical edge needs to be a key focus in the execution of the DOD Zero Trust Strategy.
REPORT
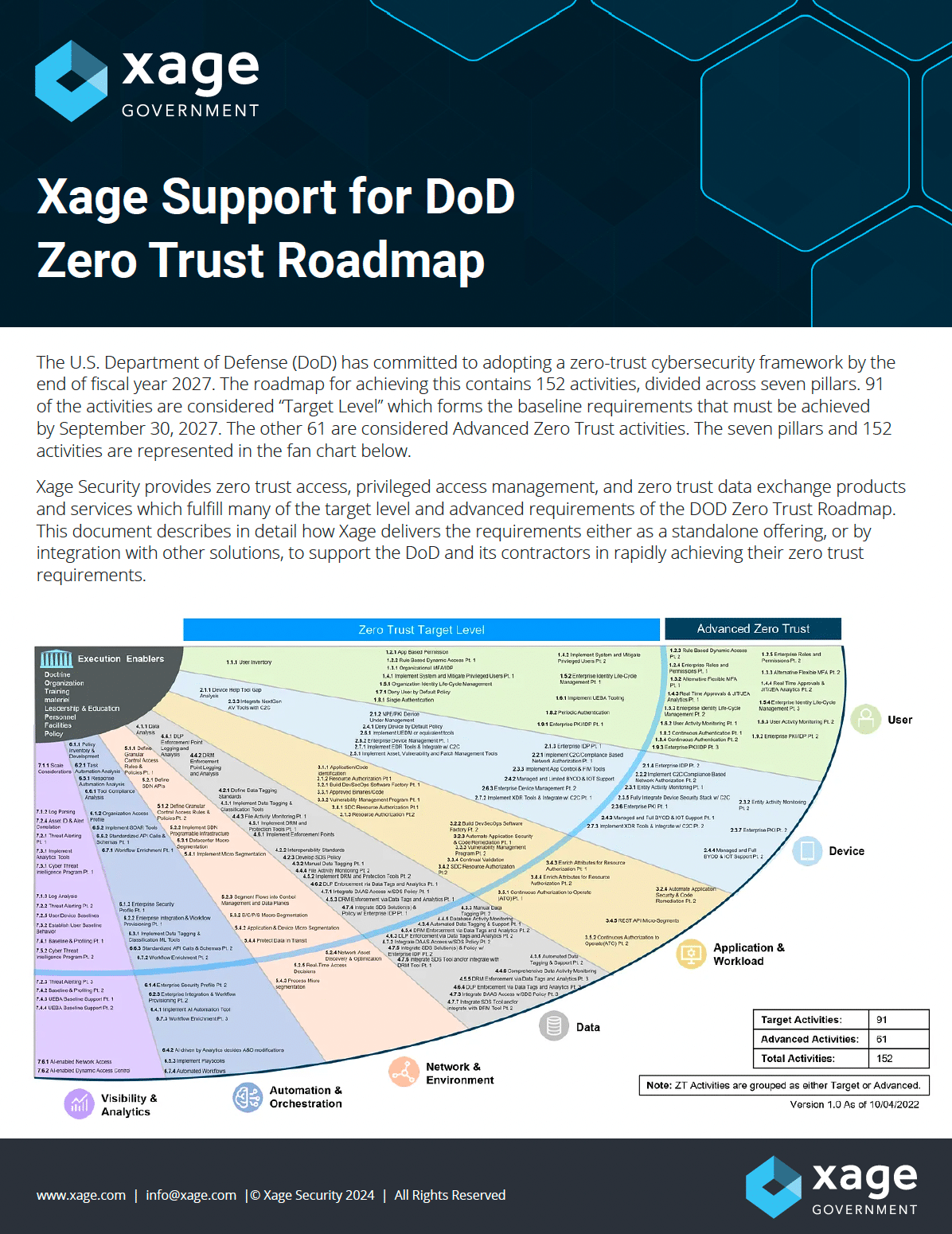
Xage Support for DoD Zero Trust Roadmap
Download the technical brief for detailed descriptions of Xage’s support or applicability to each activity and function, for a total of 90% full or conditional support.