Author: Chase Snyder, Sr. PMM, Xage Security
The results of the SANS Industrial Control Systems (ICS) Security Survey for 2023 have been released. This survey polled hundreds of active leaders and practitioners in OT/ICS security, and provides a window into the challenging arena of securing critical infrastructure and operational systems at a time when the cyber threat landscape is escalating.
This survey is a valuable resource for OT and ICS cybersecurity professionals, as it reveals the challenges their peers are facing and the solutions they are pursuing. The survey also touches on technological shifts such as increasing cloud adoption and remote access to ICS assets, that are both driving innovation and digital transformation, as well as creating new shifting attack surfaces for evolving threat actors to target.
Here are a few of the most interesting, revealing, and actionable results from the 2023 SANS ICS Security Survey.
Attackers Are Still Succeeding at Pivoting from IT to OT
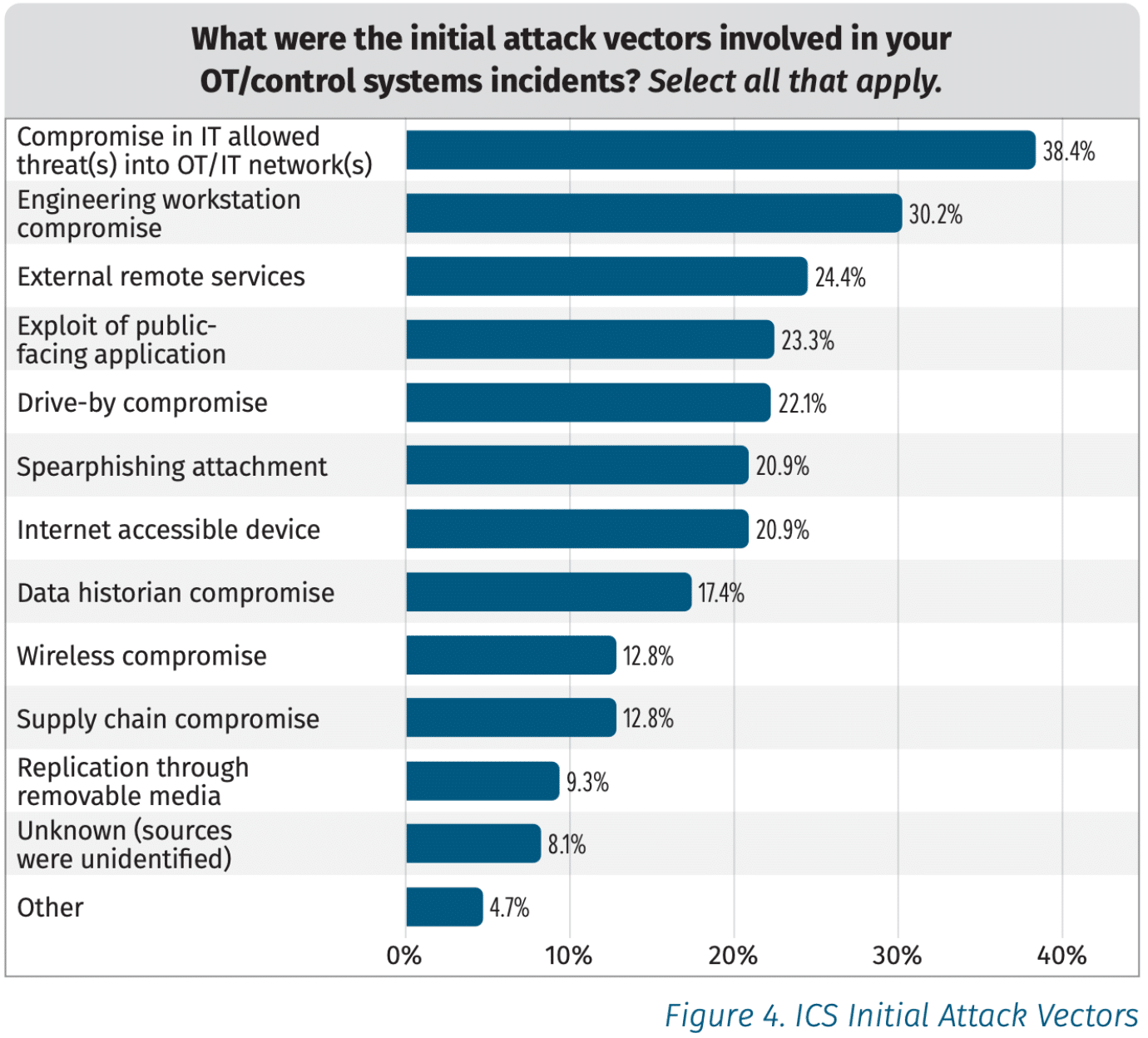
The number one reported initial intrusion vector came as no surprise: Attackers entering through corporate IT, then pivoting into OT systems. This was a key concern in the Colonial Pipeline attack several years ago, which launched OT cybersecurity into the mainstream news and into the spotlight in a way it had never been before.
After the IT to OT pivot on the list of initial attack vectors came Engineering Workstation Compromise, External Remote Services, and Exploit of Public Facing Application. Honorable mentions went to lateral movement and compromised active directory infrastructure.
Given the ongoing success of the above listed attack vectors, it is surprising that most respondents indicated an 8 out of 10 level of confidence about the separation between their ICS networks and the IT enterprise network and/or the public internet.
These all point to the near complete erosion of the air gap between OT and IT, and between enterprises and the public internet more generally. Attackers are finding their way in, which makes defense-in-depth and the “Defensible Architecture” pillar of the SANS ICS Security Pillars all the more important as these trends continue.
OT Is Starting to Move To The Cloud, Potentially Adding Risk
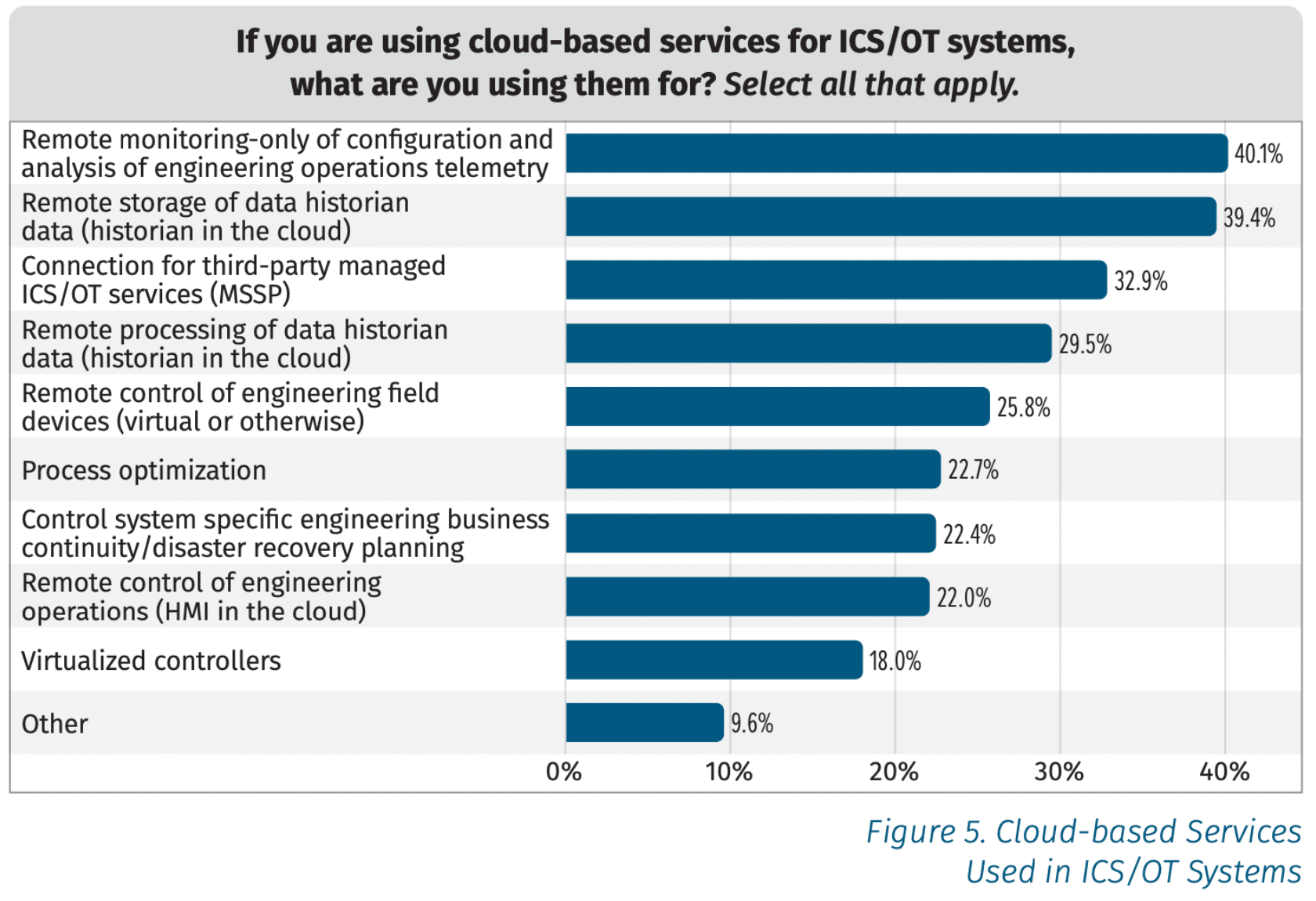
The SANS Survey found that a third of organizations are using the cloud for third-party managed ICS/OT services, and around a quarter are using cloud for remote control of engineering field devices. Some are even moving HMIs into the cloud. Given the fact that remote access applications are a common intrusion vector, moving such assets to the cloud has clear potential to introduce risk. But the business benefits may be valuable enough that such moves are inevitable. To secure against abuse of cloud-based services, OT/ICS teams need to double down on managing their credentials and assuring least-privilege for every identity.
Where Does ICS Security Go From Here?
Survey results do show a heavy emphasis on the third pillar of the SANS 5 Critical ICS Security Controls: ICS Network Visibility and Monitoring. However, the survey also noted that only around 25% of organizations were actively collecting security or other event logs about remote access sessions. As cloud investments increase and remote access rises, this will present increasing security challenges. Future investments will need to be made to address the growing and shifting attack surface, and bring the other, more prevention-focused controls into parity. Given that remote access methods and IT to OT pivot were among the top intrusion vectors, it is somewhat surprising not to see Defensible Architecture and Secure Remote Access closer to the top of the investment list.
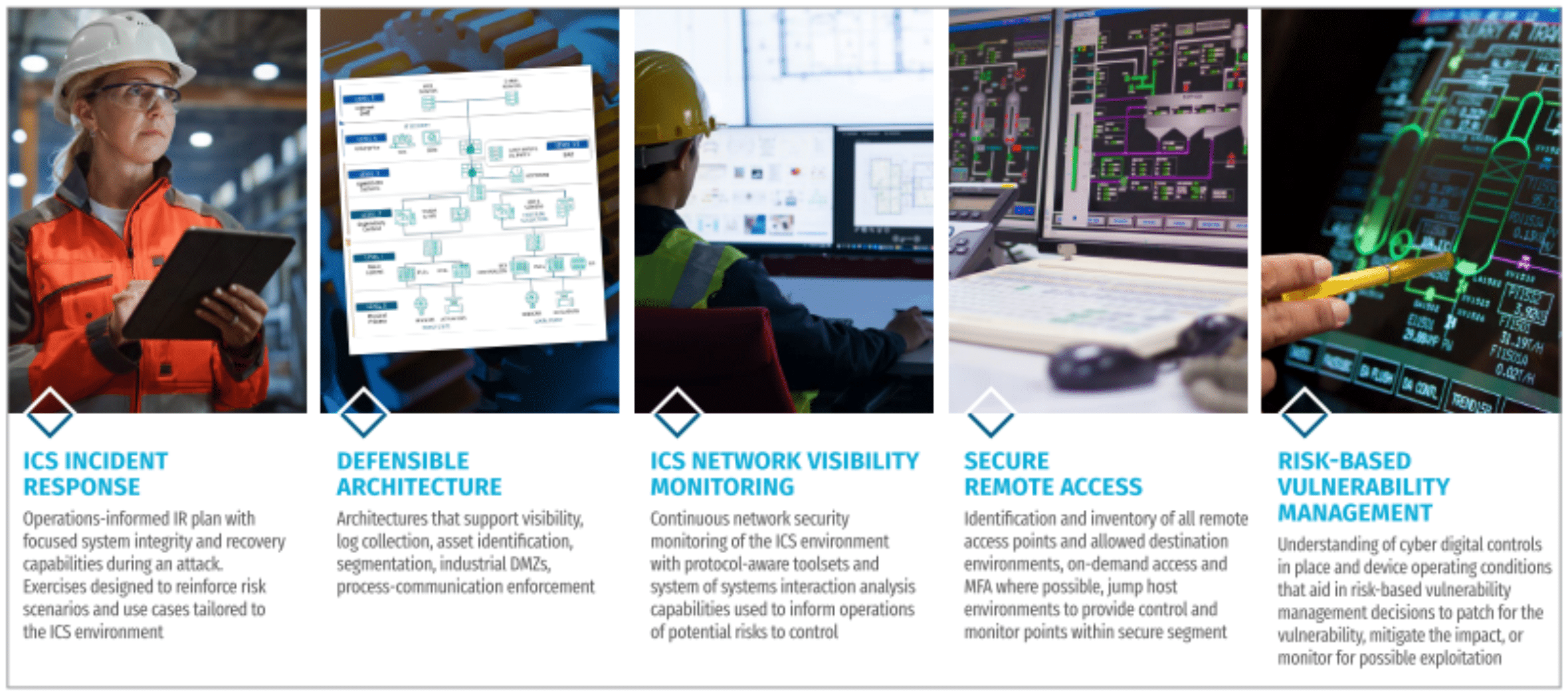
As the survey reflects, we are at a pivotal moment in history for the security of industrial control systems. Attacks have gone up, technologies are shifting to the cloud, and budgets and staff are strained. Rapid adaptation to these conditions will make the difference between organizations that excel, and those that struggle.
As ICS systems come under increasing attack, we anticipate a swing in focus from detection and response to protection and prevention. Reducing downtime through proactive prevention methods and zero trust strategies will grow increasingly important as attackers grow more effective at initial intrusion and concealing their expansion with living-off-the-land methods.
You can download the full white paper detailing the results of the SANS ICS Security Survey for 2023 here, or watch the webinar, featuring Xage Security, here.










