Celine Rosak, Director of Corporate Marketing & Brand, Xage Security
Today’s enterprises live and breathe digital operations. Yet, many still grant administrators sweeping, persistent access to critical systems—regardless of whether they need it. The
Even organizations that have implemented Privileged Access Management (PAM) tools often fail to reduce the scope and persistence of those privileges. This blog is our understanding of the Gartner key findings and recommendations—by adding the Xage perspective on how to operationalize these best practices across IT, cloud, and OT environments.
Key Findings & Recommendations (and Commentary)
Too Much Power, Too Often: Why Broad Privileges Are a Ticking Time Bomb
Gartner Key Finding:
“System administrators often possess broad privileged access on an ongoing, extended and permanent basis. Such privileges lead to unnecessarily increased risk, given that often these privileges are in excess of what is required to perform necessary functions.”
The Xage Take:
It’s still all too common for administrators to receive sweeping, persistent access to systems—often far beyond what they actually need—due to lack of proper tools to accomplish tighter controls. This approach can backfire dramatically. If an attacker compromises just one of these over-privileged accounts, they inherit all of its unrestricted power.
That’s why PAM solutions were created in the first place—to store credentials in secure vaults and rotate them regularly. However, these capabilities are just the tip of the iceberg. According to the report, “only 45% of organizations have deployed a PAM tool and are using it at a very basic level (that is, vaulting and rotating privileged credentials).” These measures help, but they don’t solve the root problem: why grant excessive access at all if it only increases risk?
More importantly, why keep that access always on? Static, over-privileged accounts are high-value targets. It’s time to reframe the conversation: don’t just protect privileged credentials—limit their scope and lifespan entirely.
The Danger of “Always On” Access: Standing Privileges Need to Go
Gartner Key Finding:
“Although privileged access management (PAM) tools help mitigate the risk of privileged access through vaulting and rotating credentials, the risk posed by standing privileges remains high unless efforts are made to change operational models to reduce standing privileges.”
The Xage take:
Vaulting and credential rotation are essential first steps in any privileged access strategy—but they’re only part of the equation. Even when credentials are stored securely, standing privileges still pose a risk if those credentials can be used at any time.
Access that’s rarely needed shouldn’t be permanently available. Instead, it should be time-boxed—granted only when required for a specific task, and automatically revoked once that task is complete. This minimizes exposure without sacrificing operational efficiency.
Modern PAM solutions must be able to support this Just-in-Time (JIT) model. It’s not just about storing credentials securely—it’s about controlling when and how they’re used.
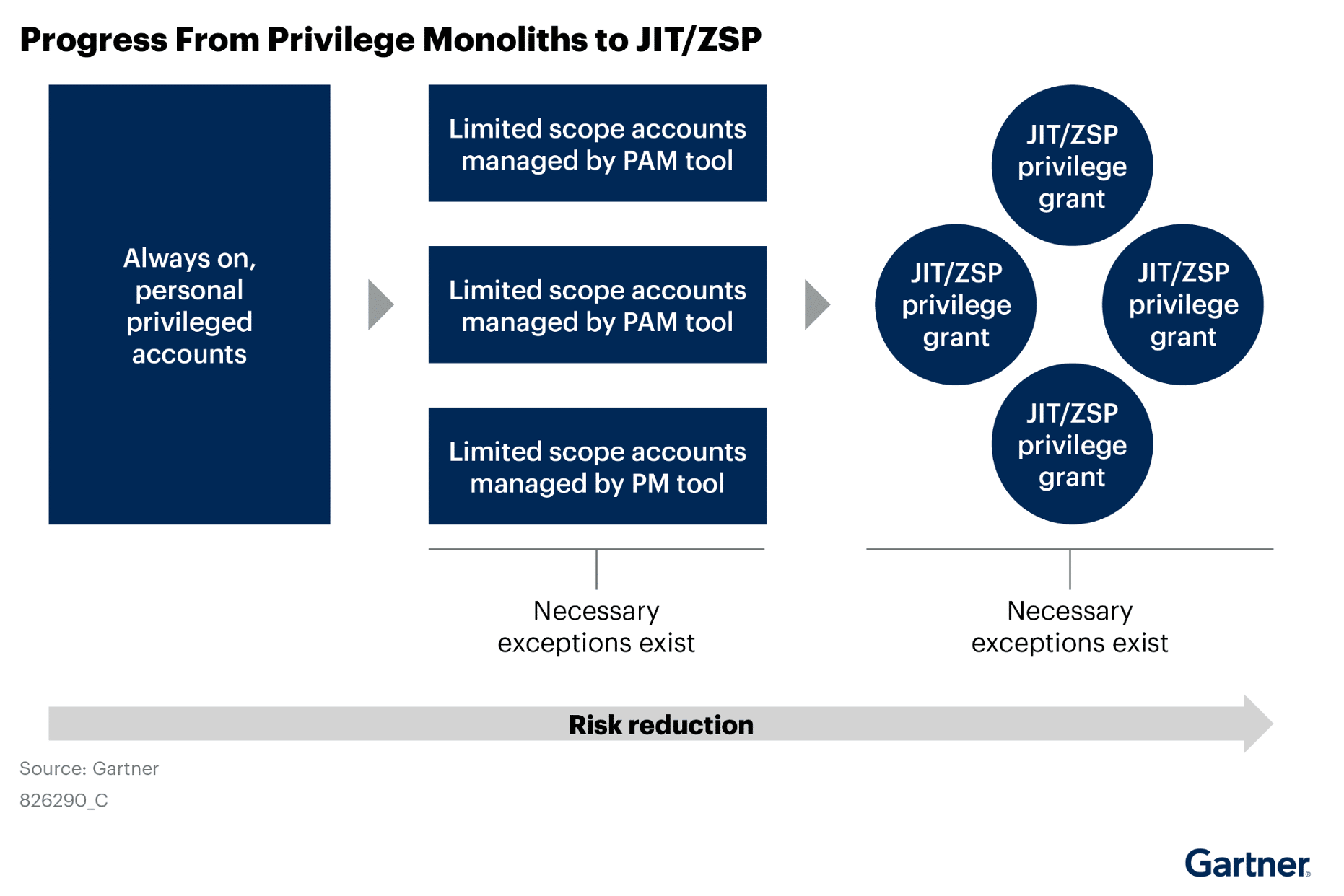
Cloud and AI Multiplies Privilege Risks
Gartner Key Finding:
“The accelerated adoption of cloud platforms and modern tooling introduces new attack surfaces where broad and unconstrained privileges can be abused. The cloud also introduces new privileged access use cases that traditional PAM tools, originally designed for on-premises environments, have not adequately addressed.”
The Xage Take:
According to Microsoft’s 2024 State of Multicloud Security Risk Report, 98% of cloud permissions that are granted are never used, leaving a mountain of opportunity for attackers to take advantage of. The cloud has fundamentally changed the security landscape—multiplying the number of identities, entitlements, and workloads at an exponential pace. Furthermore, like cloud, as AI adoption grows, these risks will further balloon out of control. AI infrastructure is vast and diverse, spreading across infrastructure and applications like LLMs, agents, and data. Traditional PAM tools, especially those reliant on standing privileges, simply weren’t built to keep up with this level of dynamism.
Ephemeral workloads demand ephemeral access, and that’s exactly what a Just-in-Time (JIT) model provides. By eliminating always-on privileges and granting access only when needed—and only for as long as needed—JIT-based solutions address cloud risks head-on.
But few organizations operate solely in the cloud, or within a single cloud. That’s why it’s critical to choose a solution that applies JIT principles across all environments—cloud, data center, and operational.
Reduce the Blast Radius with Just-Enough Privilege (JEP)
Gartner Recommendation:
“Pursue a just-enough-privilege (JEP) approach by reducing the scope of privileged access, migrating from broad privileged grants to more narrowly scoped privileged accounts managed by a PAM tool.”
The Xage take:
Granular access is one of the most effective ways to shrink your attack surface. Just-Enough Privilege (JEP) means granting users only the access they need—nothing more, even if they’re highly trusted or in privileged roles.
This approach limits the blast radius if any one account is compromised. No single identity should be a master key to the entire environment. With JEP, each account is narrowly scoped to a specific role or function, making unauthorized access significantly less damaging and far easier to contain.
Phasing in Just-in-Time Access
Gartner Recommendation:
“Adopt a phased approach to risk reduction by implementing a just-in-time (JIT) approach, targeting low-complexity and/or high-volume cases where standing privileges exist.”
The Xage take:
Rolling out a Just-in-Time (JIT) model doesn’t have to be all-or-nothing. In fact, starting small is often the smartest path. Testing JIT with low-complexity accounts—like vendors or service desk users—gives PAM administrators a clear sense of how the model impacts day-to-day operations.
At the same time, targeting high-volume access areas early on can help reduce the greatest concentrations of risk quickly. It’s a pragmatic way to build confidence, show quick wins, and pave the way for broader adoption across more complex privileged workflows. The goal is for admins to discover how widely applicable and easy to adopt the JIT approach as they roll it out.
Any User, Any Environment: Make JEP + JIT Work Everywhere
Gartner Recommendation:
“Implement PAM tooling for executing the JEP approach and reducing standing privileges using JIT methods by assessing traditional PAM and specialized JIT tools that address both traditional and cloud-native use cases.”
The Xage take:
Combining Just-in-Time (JIT) access with Just-Enough Privilege (JEP) is the most effective way to reduce risk in real time. This approach aligns access controls with the natural rhythms of work—providing the right access to the right resource, only when it’s needed—rather than relying on blanket standing privileges that expose systems unnecessarily.
The result? A dramatically reduced attack surface and a more agile security posture.
But effectiveness also depends on coverage. The solution you choose must operate seamlessly across cloud environments, on-prem data centers, and operational technology (OT) systems. Xage is built for that kind of end-to-end enforcement—delivering zero standing privilege wherever your assets live.
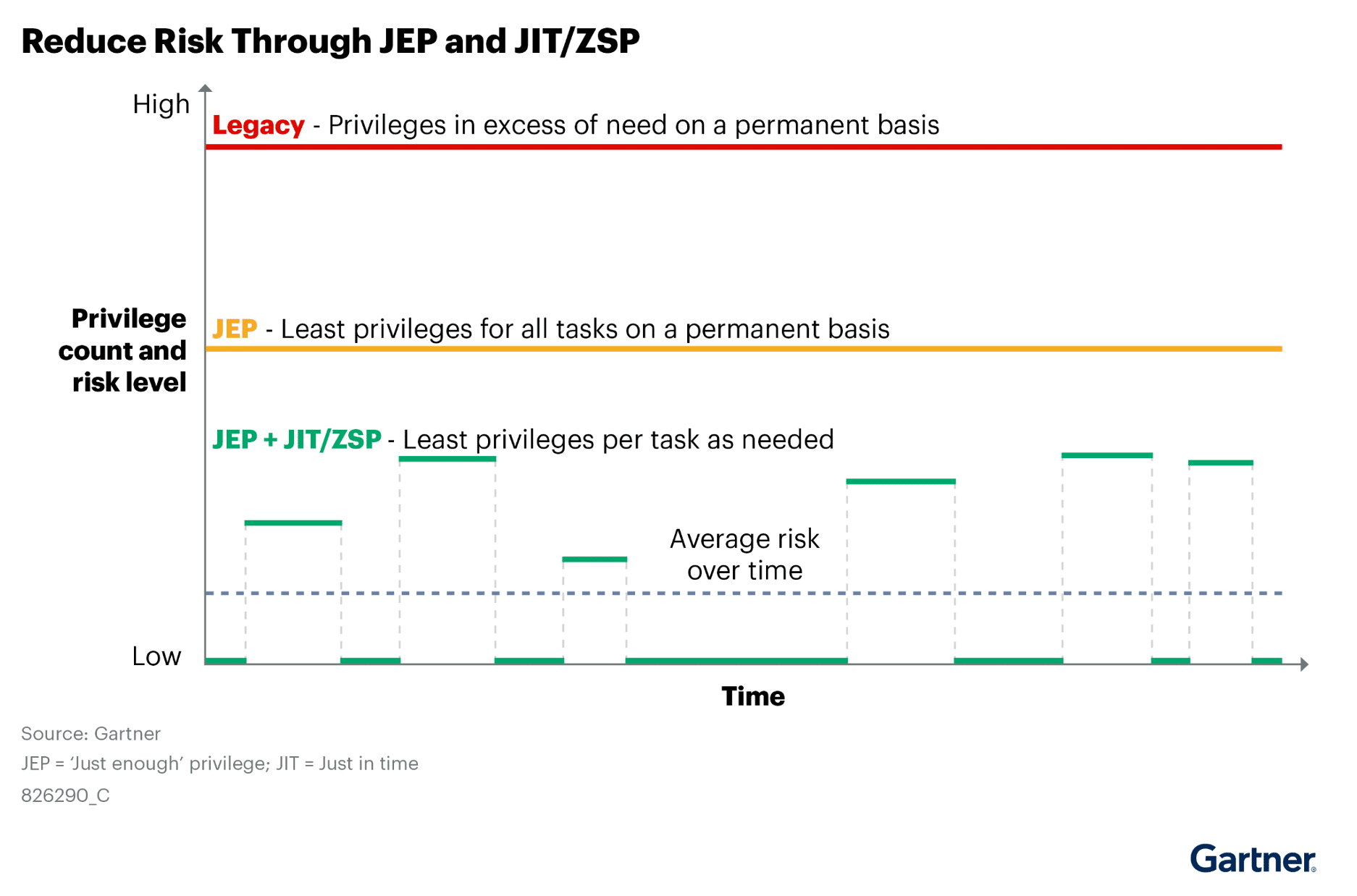
Conclusion: From Standing Privilege to Agile Security
Traditional PAM is no longer enough. To truly secure modern environments, organizations need JIT + JEP models that remove standing access, limit permissions, and adjust dynamically to how people work. Read the full report for detailed analysis and to better understand the JITPvendor landscape.
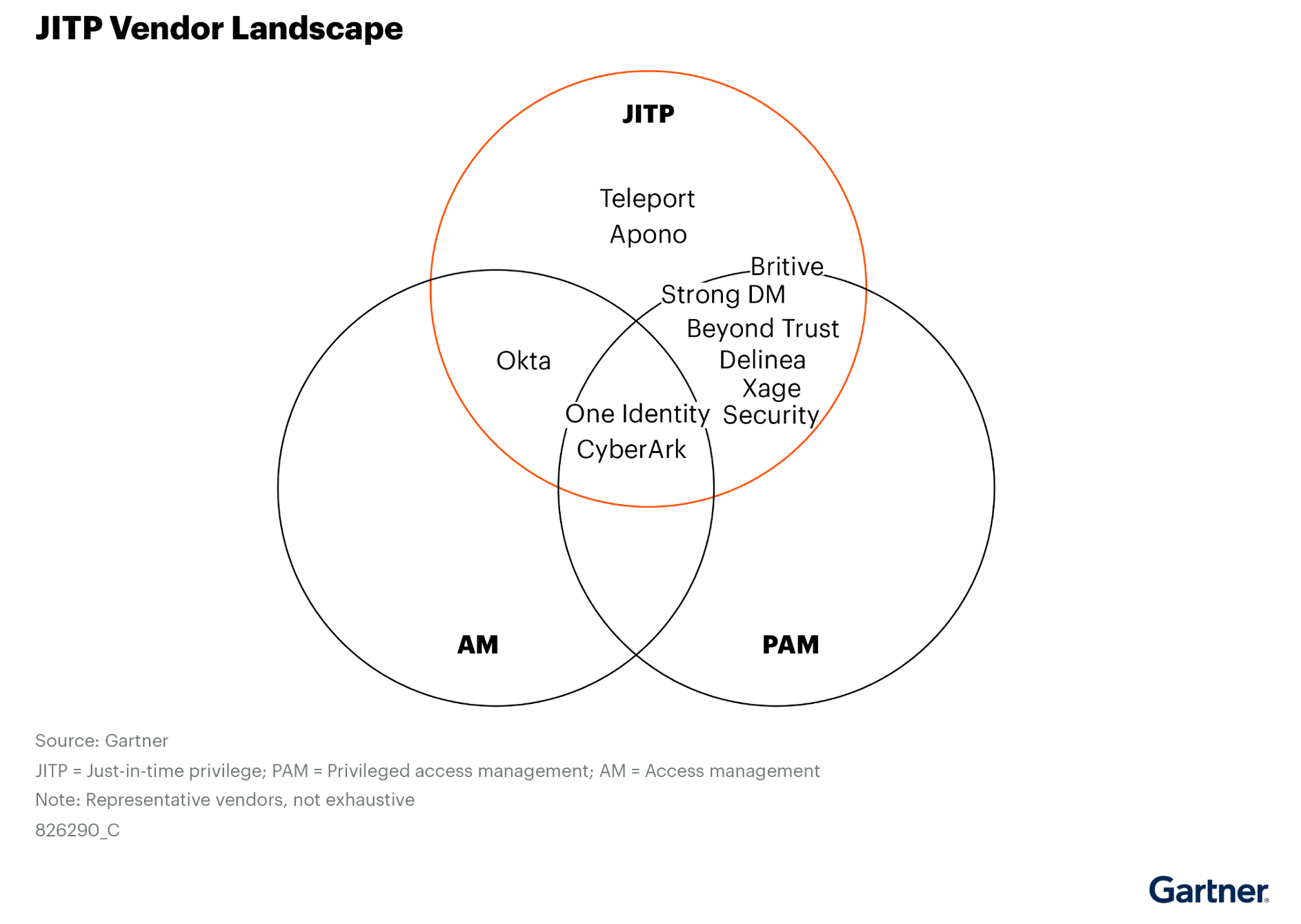
Gartner, Reduce Risk Through a Just-in-Time Approach to PAM, Paul Mezzera, Nayara Sangiorgio, Michael Kelley, Abhyuday Data, Felix Gaehtgens, April 11 2025
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.










