Enforce identity-first access across applications, IT infrastructure, and cyber-physical systems—without slowing down operations.
Unified Zero Trust for Data Centers & IT
The Challenge
Modern IT Expands the Attack Surface. Point Products Fall Short.
Data centers and IT environments are rapidly evolving, with new apps, workloads, and cyber-physical systems expanding the attack surface. Threats range from insider misuse and data leakage to advanced attacks on backend infrastructure, power, and cooling systems—while AI components add further complexity. Siloed tools like VPNs and traditional PAM can’t keep pace. Isn’t it time your security matched the speed and complexity of modern data centers?
Unleash Data Center Potential—Without Compromising Security
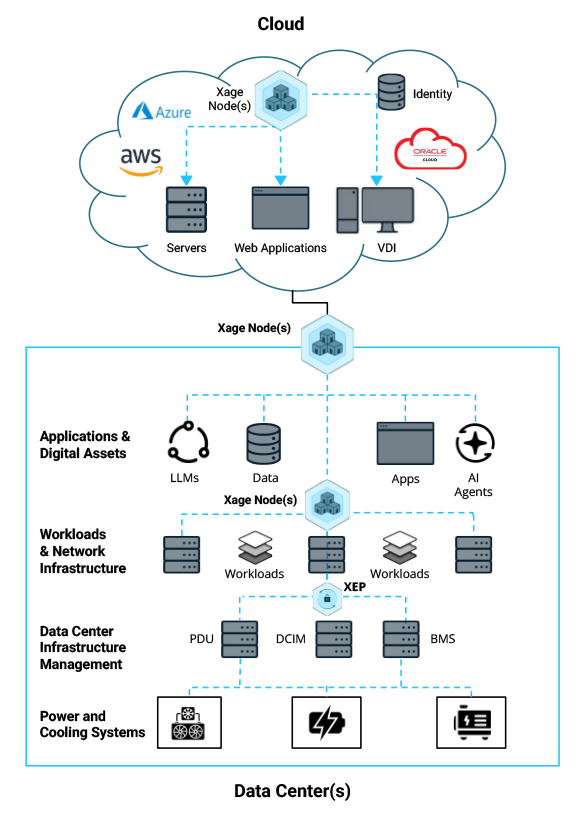
Xage delivers identity-first Zero Trust protection across the full data center stack—spanning digital workloads, IT systems, and critical cyber-physical infrastructure. This unified approach enforces least-privilege, just-in-time access for every interaction—human, machine, or agent—blocking initial infiltration, preventing lateral movement, and stopping data leakage while ensuring compliance.
Key Benefits

Harden the Attack Surface
Eliminate legacy VPNs, static credentials, and traditional PAM solutions with Unified Zero Trust Access Management.

Simplify Compliance and Operations
Centralize visibility, control, and tamperproof auditing across IT, OT, and cloud, and for everything from DCIM to AI.

Scale with Resilience
Distributed mesh architecture ensures protection even in outages or air-gapped deployments, with no single point of failure for operational or cyber resilience.
Kinder Morgan Transforms Data Center Access Security and Control with Xage
“After seeing the impact of Xage in our OT environment, expanding into the data center was a no-brainer. The platform had already proven itself—resilient, adaptable, and aligned with our Zero Trust strategy. We trusted Xage to deliver, and they did. We appreciate finding a partner that delivers equal expertise in both IT and OT environments.”
Mark Huse, CIO, Kinder Morgan
Zero Trust for Workloads and Infrastructure
Identity-Based Access Management for Workloads
- Granular, just-in-time and just-enough access—no standing privileges.
- Replace flat networks and unmanaged VPNs with identity-verified connections.
- Extended Privileged Access Management (XPAM): session-based credential issuance, rotation, and quantum-resistant vaulting.
- Phishing-resistant MFA and seamless SSO—even for legacy assets.
AI Workloads and Application Security
- Fine-grained, policy-based access to proprietary data sources.
- Secure LLM-to-database queries and agent-to-agent (A2A) interactions.
- Jailbreak-proof enforcement at the protocol level (MCP, A2A).
- Governance and auditing of all AI interactions to prevent misus
Power and Cooling System Protection
- Asset-level Zero Trust for DCIM, BMS, PDU, HVAC, and cooling.
- Policy-driven microsegmentation and virtual patching to shield OT assets.
- Temporary vendor access with full monitoring and auto-revocation.
- Continuous enforcement—even in air-gapped or disconnected systems.
Secure Machine-to-Machine (M2M) Communication
- Identity-verified enforcement for telemetry, model data, and AI pipelines.
- Broad protocol support for secure access across IT, OT, cloud-native, and legacy environments.
- Prevent unauthorized connections and stop data leakage at the source.
- Guardrails for specialized AI use cases such as MCP and A2A.

Secure Remote Access For Any Asset
Provide frictionless secure remote access for employees, contractors, and vendors—without VPNs or endpoint agents.
- Agentless, Browser-based Access – Hardened isolation with zero client-side complexity.
- Zero Trust Network Access (ZTNA) – Multi-hop validation enforces segmentation across zones.
- Distributed Mesh Architecture – Resilient enforcement with no single point of failure.
- Native App Support (Xage Access Connector) – Secure access via PuTTY, DB clients, and engineering applications.
Monitoring, Analytics & Integrations
Immutable Audit Trails & Session Recording
- Tamperproof logs with visual playback and searchable transcripts.
- Audit coverage across IT, OT, AI, and cloud systems.
- Provides the visibility and controls needed to support compliance with NIST, IEC 62443, NIS2, NERC-CIP, ISO 27001, and SOC 2.
Risk Management and SOC Integrations
- Real-time analytics across users, devices, and apps.
- Risk-based recommendations optimize security without slowing operations.
- AI-powered insights enable adaptive access based on anomalies.
- Correlate Zero Trust events with anomaly detection systems to expedite incident response across IT and OT environments.


Why Xage for Data Center Protection?
With Xage, organizations can scale securely, comply confidently, and protect the systems that keep data centers running—without complexity or compromise.
- End-to-End Coverage: Protect applications, infrastructure, and cyber-physical systems together.
- Adaptive Access: Risk-aware, policy-based enforcement powered by analytics.
- Agentless & VPN-Free: Simplify operations and speed deployment.
- Resilient Mesh Architecture: No single point of failure; works offline or air-gapped.
- Jailbreak-Proof AI Protection: Block unauthorized LLM or AI agent data access.
- Virtual Airgaps & Microsegmentation: Reduce attack surface without redesigning networks.
“As AI factories emerge as the foundational infrastructure accelerating AI innovation, safeguarding them has become a critical priority. Together, NVIDIA BlueField and Xage’s zero-trust security enable organizations to modernize their protection strategies across AI factories and infrastructure —driving secure, scalable innovation forward.”
– Ofir Arkin, Sr. Distinguished Architect, Cybersecurity Team at NVIDIA
See Zero Trust for Data Centers and IT In Action
Related Resources
Experience Full-Stack Data Center Protection
Fill out the form and someone will be in touch with you within 24 hours to schedule a meeting.








