Authors: Rohit Jhangiani, Director of Engineering & Vivek Doshi, Principal Product Manager at Xage Security
As a global pioneer in zero trust security solutions, we strive to enhance the security landscape with innovative technologies. Today, we announced our latest advancements: AI-powered analytics that revolutionize how cybersecurity teams operate.
In a landscape where attacks are on the rise and the cybersecurity talent gap is growing, capabilities that enable organizations to be more effective and faster are at a premium. Organizations around the world are looking for solutions that enable them to more effectively and efficiently prevent cyberattacks. These solutions are designed to empower users with data that enables them to make more informed and quicker decisions.
How Is Xage Using AI for Cybersecurity?
Introducing AI-Driven Insights with Xage Insights and Xena
The new solutions introduced today include Xage Insights, an analysis engine powered by Xage’s unique access to user activity data at the deepest levels of the environment; and Xena, an AI copilot, both of which are designed to transform the effectiveness of cybersecurity operations. These tools are built on the resilient, highly-available Xage Fabric.
Xage Fabric Audit-Quality Data
Xage is built on a distributed ledger, which makes the data high-integrity and tamper-proof. Xage Fabric’s universal deployment allows enterprises to protect from the core to the edge of the organization’s IT, OT, and cloud resources. Thus, it operates on richer, more granular access and behavior data. This data source sets Xage apart from similar AI-powered solutions in quality. The quality of output from any generative AI improves with the quality of its input. This depth of data enables Xage Insights and Xena to provide precise insights and tailored recommendations to drive better security posture through zero trust policy.
Fast Track Your Zero Trust Strategy
Zero trust as a principle has been around for a decade, but implementation and enforcement of zero trust is traditionally a slow process, taking some organizations years to strategize and implement. Breakthroughs in generative AI have a real possibility to expedite the realization of zero trust strategy and give organizations an upper hand in the fight against cyberattacks.
Watch the video below for an example scenario of how Xage Insights and Xena can be used in combination with each other to identify and mitigate risky user behavior.
Combined, these AI-powered capabilities will enable security administrators and operators to be more effective at implementing zero trust security principles at every stage in their roles as cyber defenders. With Xage Insights and Xena, cyber defenders can:
- Understand: Xage Insights expedites your grasp of activity and risk across IT, OT, and cloud environments. It pinpoints and prioritizes unusual user and device behaviors that merit further scrutiny. This tool enables you to deeply query your security environment to harvest insights that enhance your situational awareness and understanding of potential risks.
- Respond: Armed with rich insights, you can now respond more swiftly. Xage Insights and Xena provide targeted recommendations for response strategies and policy refinements, streamlining your actions and enhancing the overall security framework.
- Evolve: These tools aid in the continuous improvement and evolution of your security policies. By adapting dynamically to emerging threats, Xage ensures your cybersecurity posture is robust and up-to-date.
Xage Insights
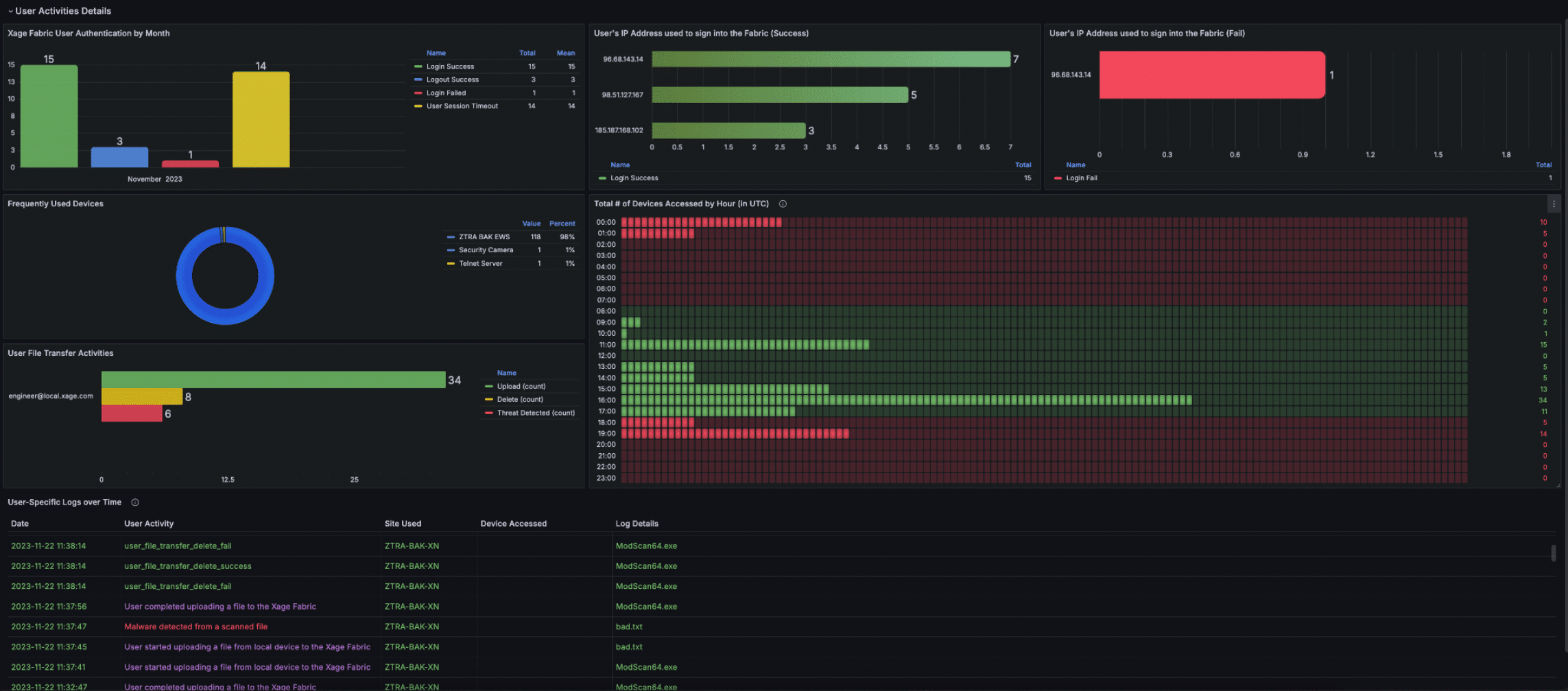
Xage Insights offers a powerful analytics engine that tracks and analyzes interactions based on identity, type, and geography. This capability not only enhances real-time situational awareness but also helps identify and address potential security risks and breaches through detailed insights into user, device, application, and workload interactions. Additionally, Xage Insights provides admins with a clear picture of the number of assets under protection and provides a protection score for the overall environment. Examples of learnings that admins can gain by looking at Xage Insights include:
User access patterns
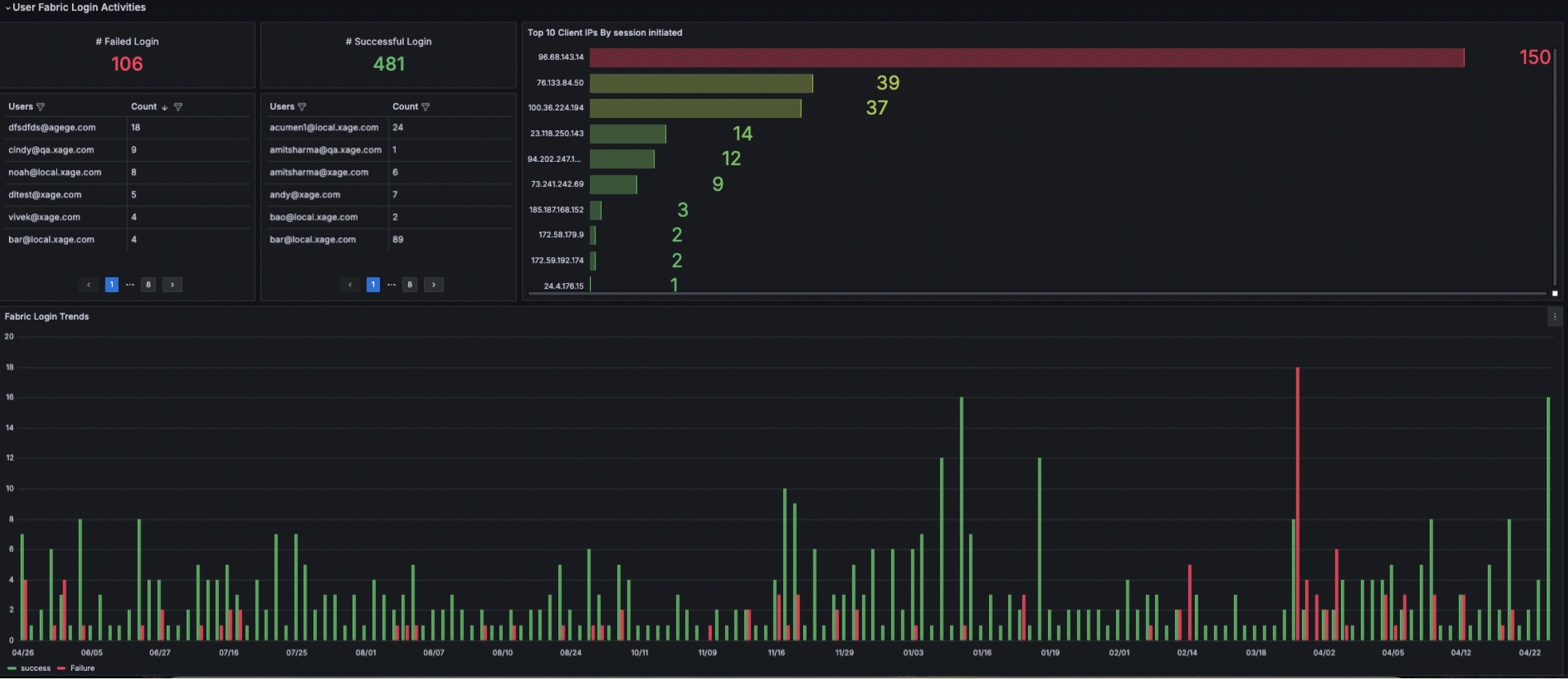
- Gain perspective into historical behavior of user’s access patterns in order to establish benchmarks and detect any abnormal login patterns
- Get a snapshot of access activities and get a pulse on how actively the Fabric is being utilized
- Zoom into a particular successful or blocked access event by day and time. Drill down into the specifics to find the user(s), number of times the user logged in during that period, IP addresses used, and geo location
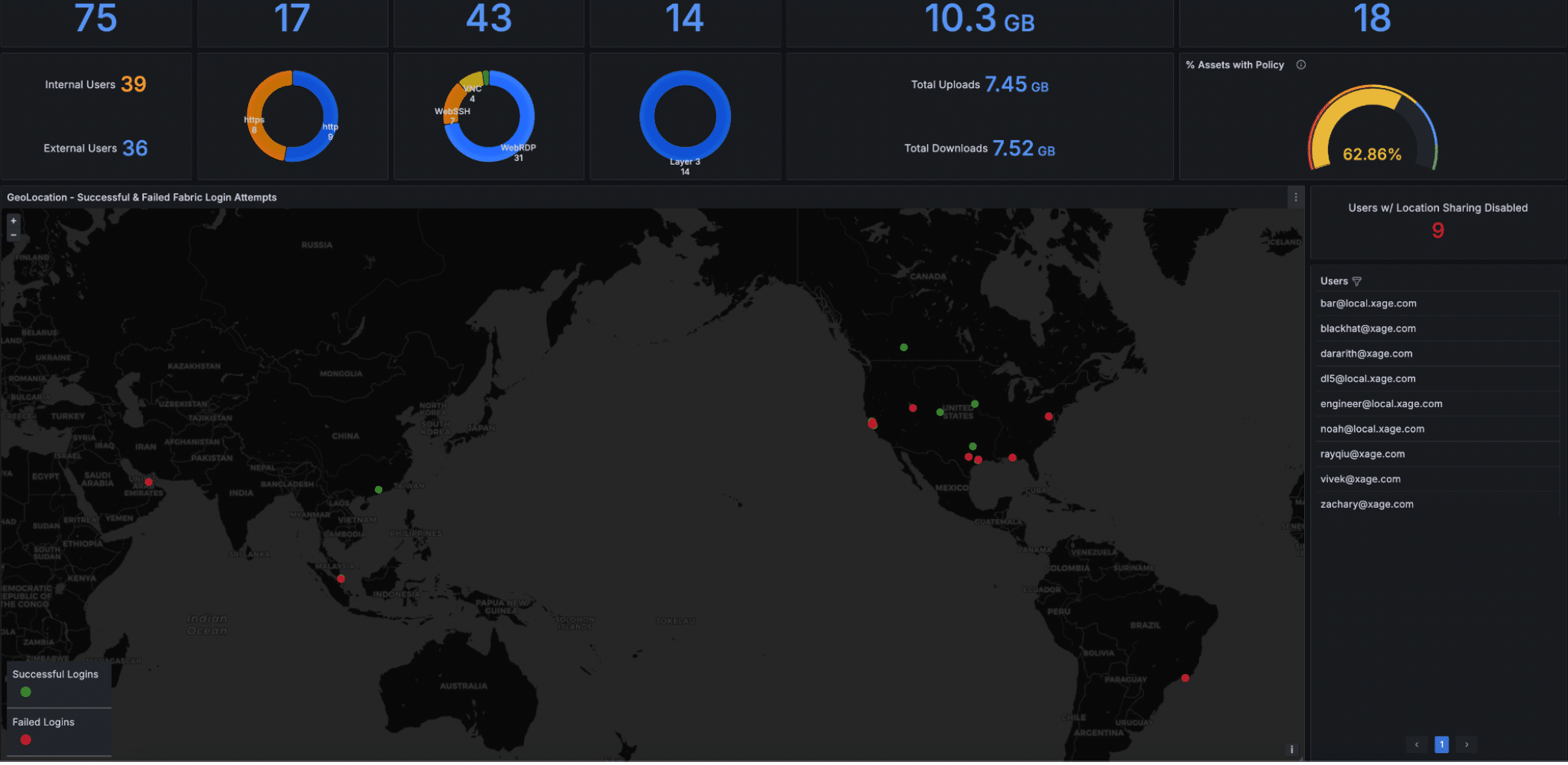
Asset (app, device, or machine)access patterns
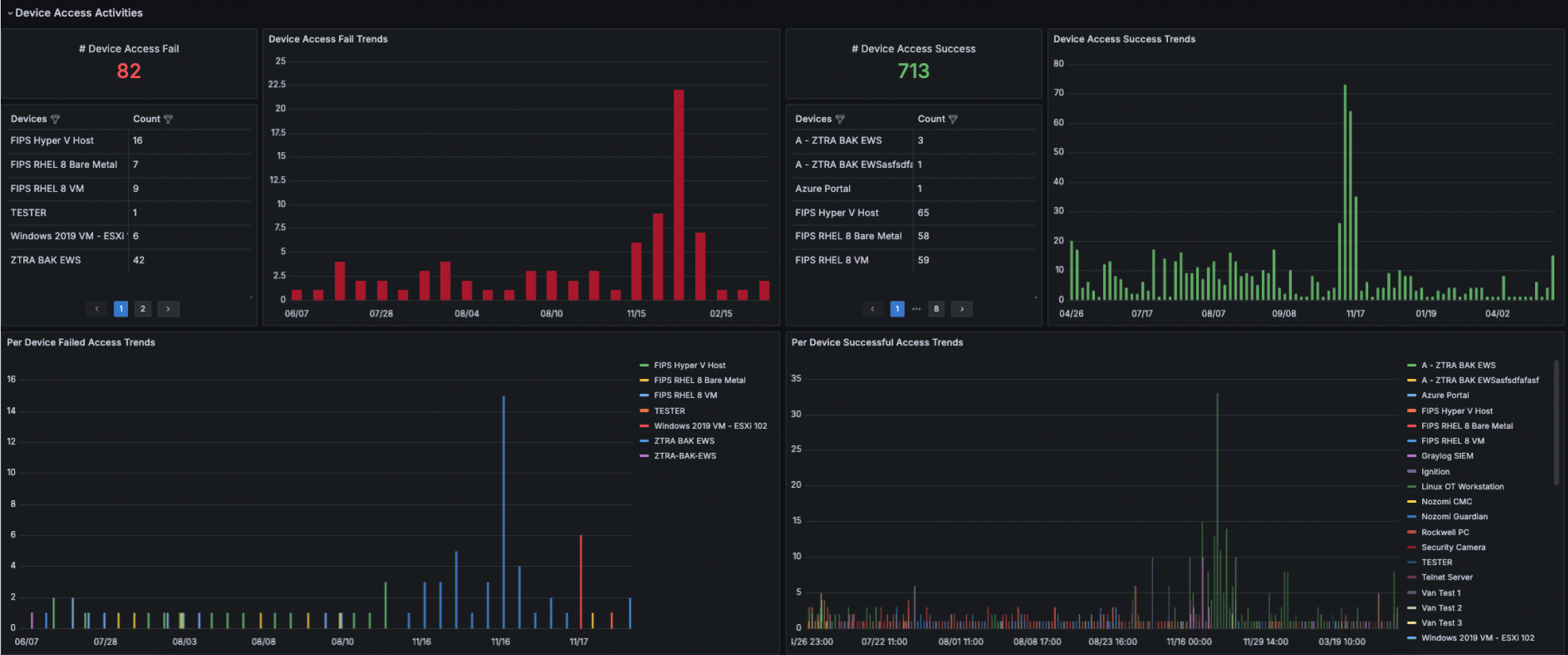
- Gain perspective into total device success and blocked access trends to detect any unusual device access activity
- Drill down into a specific access event to find all the assets that were accessed, the users who accessed them, and what activities those users carried out on the device (such as file transfers)
- Get insights into individual asset login trends in order to create a baseline on the device usage and manage load during peak access events
User specific activities
- Get a multi-dimensional view into each user’s activities to quickly narrow down problem areas. Knowing which assets the user accessed during a given period, number of times those assets were accessed, how long each session lasted, and detailed activities that the user carried out on the device can provide security-relevant insights into each user’s behavior
- Combine this with login and asset access patterns to analyze the interactions among Fabric assets—users, devices, workloads, and applications—and to identify any suspicious activity
Xena AI Copilot
Xena gives admins and operators an easy way to ask questions of their data, harnessing its capabilities for enhanced intelligence. It provides actionable insights and suggestions that are tailored uniquely for your environment including deep intelligence into the activity in your environment, emerging threats, and guided remediation efforts.
When major organizations fall victim to cybersecurity breaches, it is often blamed on a lack of the necessary cybersecurity tools or a difficulty maintaining enough expert staff. There’s truth to this rationale, but there’s also more to the story. Most organizations have the tools they need, and staff that know how to use them, but they lack the visibility into their security posture to know which attack paths most urgently need the available cybersecurity measures. This is the core challenge that Xena is aimed to solve: identifying where your existing cybersecurity policy and enforcement capabilities should be updated to improve your security posture.
For example, in the infamous Colonial Pipeline ransomware attack and the more recent Change Healthcare attack, both started out with attackers logging in using valid credentials with no multi-factor authentication requirements. Those organizations have MFA in their environments. They have security tools that could have prevented these attacks, they just weren’t deployed in certain critical attack paths. These attacks illustrate perfectly just how difficult it is to manually identify likely attack paths that should have stronger security measures deployed. Prioritizing which security measures should go where so that staff can use their time effectively is the ongoing primary challenge for all cybersecurity efforts.
Using AI that is powered by deep visibility into user access paths and behaviors from the perimeter to the deep core of your environment, Xena shows you exactly where those critical attack paths may be. Then, the Xage Fabric itself can be used efficiently by security admins and operators to deploy the appropriate security policies and enforcement, exactly where they are most needed. Xage enables zero trust access policies, multi-layer MFA, and rapid revocation of access privileges. And now, with Xena, we can tell you in an instant where those capabilities are most urgently needed in your environment.
Prompts and requests that you can ask Xena include but are not limited to:
- From which geolocations did a user access a device or login to the system?
- What suspicious activity is happening on my systems?
- What policies in my environment need to be refined?
- Write a security posture report that I can share with my CEO.
- Give me the code to enable MFA for a user, suspend a user or have the user reset their password in Active Directory.
Xena Interface
The Xena interface starts with a handful of suggested prompts based on commonly asked questions by Xage users. Xena will then surface a response tailor-made to the organization’s unique environment.
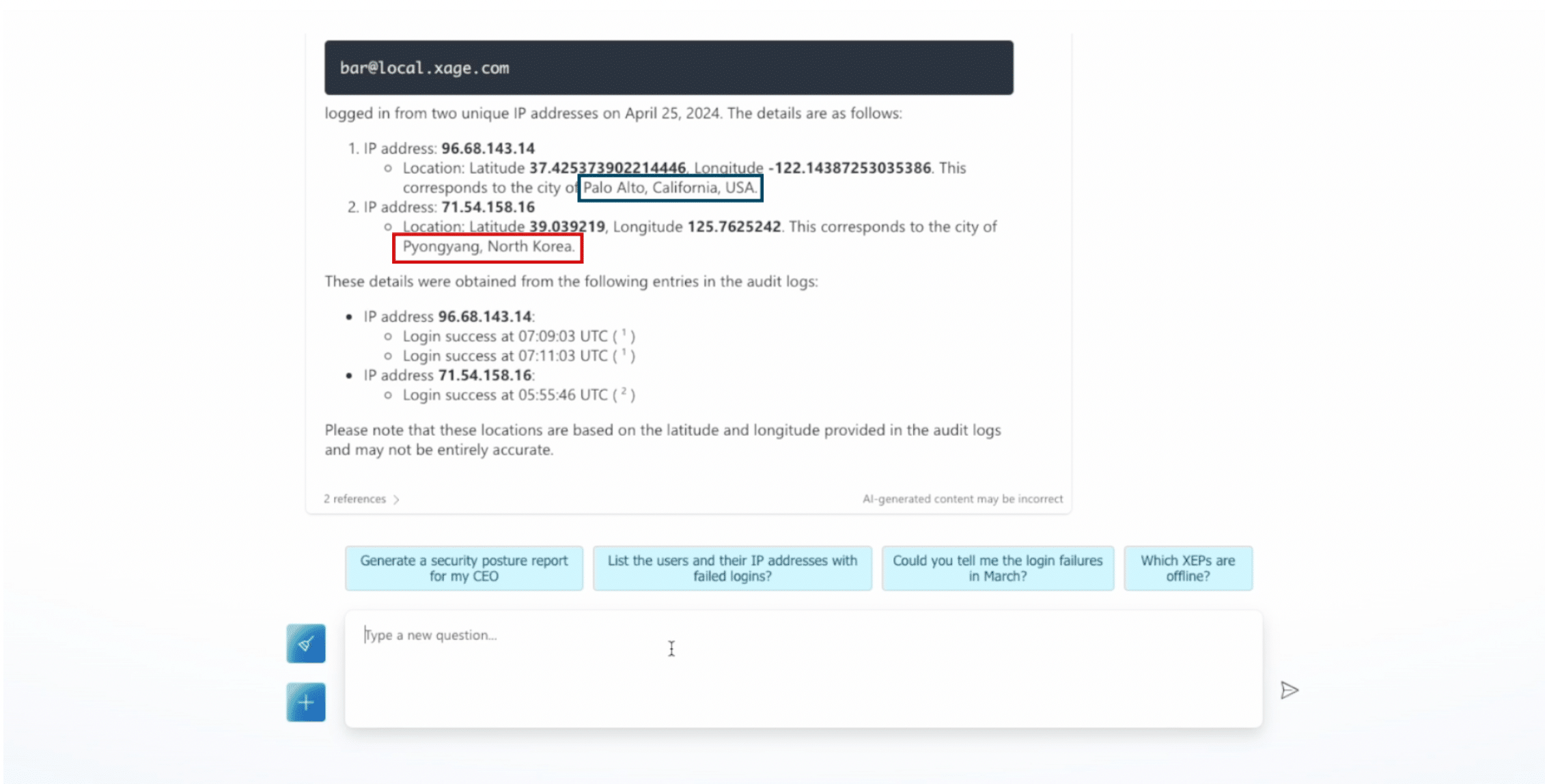
Responses generated can surface insights like the example shown below. In this example, you can see that the same user logged into the Xage Fabric from two separate IP addresses on the same day from different locations. This insight shows extremely suspicious activity and can prompt admins to reset the user’s password and enable multi-factor authentication.
Xage Insights will be generally available starting May 2024, and Xena will enter its beta phase in June 2024.