The Cybersecurity Maturity Model Certification (CMMC) is a framework for protecting information handled by the U.S. Department of Defense (DoD) and its contractors. Specifically, CMMC is geared toward protecting Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
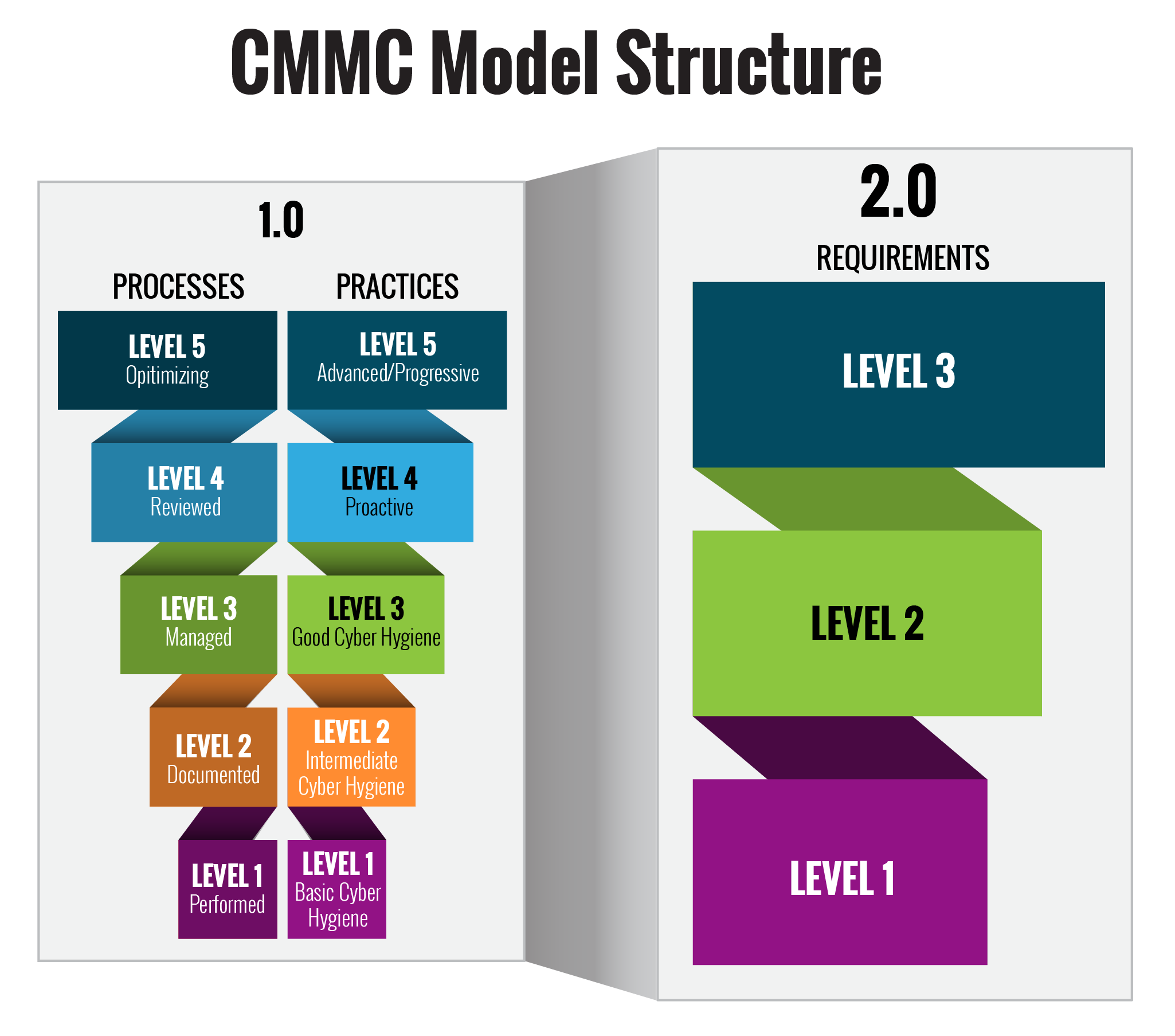
The CMMC model is in the process of being updated and simplified from a structure with five levels, split across the general categories of Process and Practices, down to a simpler three level system. The three levels of CMMC 2.0 model structure are mapped closely to the requirements laid out in NIST SP 800-171 and NIST SP 800-172. The DoD has stated that “in CMMC 2.0, the ‘Advanced’ Level (Level 2) will be equivalent to NIST SP 800-171” and the Expert level (Level 3) will be based on a subset of the controls listed in NIST SP 800-172.
There are a lot of moving parts in this transition. The underlying document of NIST SP 800 -171 Revision 2 was superseded by Revision 3 in May, 2024. The implementation of CMMC 2.0 is happening in phases, with the current expectation being that the model is fully implemented by October, 2026. Depending on the current controls in place, and the cybersecurity staff and resources available, achieving these controls by the deadline may pose a challenge.
This article will provide a high-level overview of the CMMC Level 1 controls and some of the changes coming for how organizations will be assessed for compliance across all CMMC levels.
The website of the office of the Chief Information Officer of the DOD says that CMMC level 1 controls for CMMC 2.0 will be the same as Level 1 in CMMC 1.0. However, since the entire model is consolidating from five levels to 3, there may be some shifts in the content and nature of the content in each level, even if the overall gist is the same.
How Many CMMC Level 1 Controls Are There?
The controls in CMMC are divided across 14 domains. Of these 14 domains, six contain controls that are required for Level 1 of CMMC, with a total of 17 controls or practices falling into the Level 1 requirements.
The domains with level 1 controls, and the controls themselves, are in the table below, pulled directly from the spreadsheet published by the DOD CIO:
Domain
Controls
Access Control (AC)
AC.1.001
AC.L1-3.1.1
Authorized Access Control
Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- FAR Clause 52.204-21 b.1.i
- NIST SP 800-171 Rev 2 3.1.1
AC.1.002
AC.L1-3.1.2
Transaction & Function Control
Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- FAR Clause 52.204-21 b.1.ii
- NIST SP 800-171 Rev 2 3.1.2
AC.1.003
AC.L1-3.1.20
External Connections
Verify and control/limit connections to and use of external information systems.
- FAR Clause 52.204-21 b.1.iii
- NIST SP 800-171 Rev 2 3.1.20
AC.1.004
AC.L1-3.1.22
Control Public Information
Control information posted or processed on publicly accessible information systems.
- FAR Clause 52.204-21 b.1.iv
- NIST SP 800-171 Rev 2 3.1.22
Identification and Authentication (IA)
IA.1.076
IA.L1-3.5.1
Identification
Identify information system users, processes acting on behalf of users, or devices.
- FAR Clause 52.204-21 b.1.v
- NIST SP 800-171 Rev 2 3.5.1
IA.1.077
IA.L1-3.5.2
Authentication
Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems.
- FAR Clause 52.204-21 b.1.vi
- NIST SP 800-171 Rev 2 3.5.2
Media Protection (MP)
MP.1.118
MP.L1-3.8.3
Media Disposal
Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- FAR Clause 52.204-21 b.1.vii
- NIST SP 800-171 Rev 2 3.8.3
Physical Protection (PE)
PE.1.131
PE.L1-3.10.1
Limit Physical Access
Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- FAR Clause 52.204-21 b.1.viii
- NIST SP 800-171 Rev 2 3.10.1
PE.1.132
PE.L1-3.10.3
Escort Visitors
Escort visitors and monitor visitor activity.
- FAR Clause 52.204-21 Partial b.1.ix
- NIST SP 800-171 Rev 2 3.10.3
PE.1.133
PE.L1-3.10.4
Physical Access Logs
Maintain audit logs of physical access.
- FAR Clause 52.204-21 Partial b.1.ix
- NIST SP 800-171 Rev 2 3.10.4
PE.1.134
PE.L1-3.10.5
Manage Physical Access
Control and manage physical access devices.
- FAR Clause 52.204-21 Partial b.1.ix
- NIST SP 800-171 Rev 2 3.10.5
System and Communication Protections (SC)
SC.1.175
SC.L1-3.13.1
Boundary Protection
Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- FAR Clause 52.204-21 b.1.x
- NIST SP 800-171 Rev 2 3.13.1
SC.1.176
SC.L1-3.13.5
Public-Access System Separation
Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- FAR Clause 52.204-21 b.1.xi
- NIST SP 800-171 Rev 2 3.13.5
System and Information Integrity (SI)
SI.1.210
SI.L1-3.14.1
Flaw Remediation
Identify, report, and correct information and information system flaws in a timely manner.
- FAR Clause 52.204-21 b.1.xii
- NIST SP 800-171 Rev 2 3.14.1
SI.1.211
SI.L1-3.14.2
Malicious Code Protection
Provide protection from malicious code at appropriate locations within organizational information systems.
- FAR Clause 52.204-21 b.1.xiii
- NIST SP 800-171 Rev 2 3.14.2
SI.1.212
SI.L1-3.14.4
Update Malicious Code Protection
Update malicious code protection mechanisms when new releases are available.
- FAR Clause 52.204-21 b.1.xiv
- NIST SP 800-171 Rev 2 3.14.4
SI.1.213
SI.L1-3.14.5
System & File Scanning
Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
- FAR Clause 52.204-21 b.1.xv
- NIST SP 800-171 Rev 2 3.14.5
How To Achieve CMMC Level 1 Controls
A range of tools and practices will need to be in place to achieve CMMC Level 1 Controls. Every control will require a combination of people, process, and procedure to achieve. Some are more technology-dependent, while others are more procedural in nature. Physical security is often overlooked as part of a cybersecurity practice, but is critical for protecting sensitive data with relevance to national security. The Physical Protection (PE) family of controls may require a range of tools that fall outside the typical cybersecurity toolkit, from physical gates and locks to security guards and staff to prevent adversaries from gaining physical access to sensitive resources. Similarly, the Media Protection (MP) category requires sanitization or destruction of media containing sensitive information, likely a physical process (think paper shredders) and not one covered by traditional cybersecurity software.
Even for the lowest level of practices in CMMC, a broad gamut of tools and practices will need to be deployed across any organization hoping to achieve compliance. Seventeen controls may not seem like a lot, but the depth and complexity of implementing and adhering to the controls is nontrivial.
The Urgency of Access Control and Identity and Authorization
Two of the control families in CMMC warrant special attention in today’s cyber threat landscape:
- Access Control (AC)
- Identification and Authorization (IA)
Today, many data breaches begin with the use of valid credentials, obtained by cyberattackers through illicit means, to gain initial access. After that, living off the land techniques that take advantage of overly broad access permission and lack of internal authorization mechanisms are used to maintain persistence. This type of behavior has reportedly been used by nation state adversaries, such as the group dubbed Volt Typhoon, to break into U.S. critical infrastructure systems.
The controls represented in CMMC overlap a great deal with the requirements of the DoD Zero Trust Roadmap, which is also in the process of being developed and rolled out across DoD agencies. Contractors and subcontractors of the DoD will soon find themselves under much sharper scrutiny around their use of zero trust practices, which hinge on their ability to define and enforce access policies based on the identity of users, assets, devices, and data throughout their environment. Best practices like MFA for remote access that are widely acknowledged as crucial, but still not widely deployed, will become an absolute necessity.
Every organization, whether bound to CMMC compliance or not, should take a close look at their identity and access management capabilities and assure that they are modernizing to achieve CMMC and DoD Zero Trust Roadmap adherence.
Changes in CMMC Compliance Assessment
In CMMC 1.0, all DoD contractors had to get third-party assessments for CMMC compliance. One of the planned changes for CMMC 2.0 is that many organizations were able to self-audit for their compliance to the controls, depending on the sensitivity of data they handle and the level of compliance they are seeking.
In the upcoming CMMC 2.0. organizations will be required to do self-assessments for Level 1 compliance. For Level 2 compliance, many organizations will be required to seek third party assessment for compliance. For Level 3 compliance among organizations handling data critical to national security, assessments will be conducted by government officials.
Xage Security provides Zero Trust Access and Protection for Federal Government agencies, including the U.S. Space Force. In particular, Xage can deliver on access control and identity and authorization requirements, among many other practices across the control families in CMMC.