Seamless, secure, and scalable purpose-built Secure Remote Access for Operational Technology and all Cyber Physical Systems—eliminating security risks without disrupting operations.
Secure Remote Access for OT and CPS
The Challenge
Legacy remote access technologies, including VPNs, jump servers, and outdated PAM tools, introduce security gaps, operational complexity, and scalability challenges. These outdated approaches require opening firewall holes, create centralized points of failure, and often fail to protect critical Operational Technology (OT) assets like RTUs and PLCs.
Protect vulnerable Cyber Physical Systems (OT, IoT, Industrial IoT) with Xage. Our identity-based, fine-grained access control ensures seamless, scalable, and compliant protection—down to the asset level—without adding complexity or operational disruption.
Zero Trust Remote Access for OT and Cyber Physical Systems
Xage simplifies secure remote access for both users and administrators, delivering frictionless security without complexity. With Zero Trust access and layered protection, Xage Secure Remote Access (SRA) ensures seamless, least-privilege connectivity while safeguarding your entire operational environment.

Eliminate Vendor Remote Access Risk & Complexity
Securely onboard and manage vendors, contractors, and partners without exposing your network—just-in-time access access and automatically revoke credentials after task completion, including legacy OT assets (PLCs, HMIs). By eliminating static credentials, Xage minimizes the risk of credential theft while delivering secure, seamless, browser-based access for a frictionless user experience.
Zero Trust Enforcement
Unlike traditional solutions that provide broad access (e.g., entire OT network segments), Xage allows fine-grained control down to the individual asset level, ensuring that users can only interact with the specific devices they are authorized for. Every access request is continuously authenticated, authorized, and enforced at multiple security layers (e.g., Purdue Model Zones)—not just at the initial entry point—to prevent lateral movement and block attacks like ransomware.

Eliminate Firewall Complexity
Xage simplifies network security by enabling built-in segmentation, eliminating the need for complex internal firewalls to control east-west traffic in CPS environments. With Xage, administrators no longer have to constantly open and close firewall rules to grant access—reducing operational overhead while enhancing security.

VPN Replacement
Xage replaces vulnerable VPN solutions with a purpose-built Zero Trust SRA solution designed for CPS environments. Unlike VPNs that grant broad network access, Xage enforces granular, identity-based access down to individual OT assets like PLCs and HMIs—without requiring jump servers or traditional PAM. It reduces total cost of ownership by eliminating legacy tools and accelerating ROI, often within months.
Defense-in-Depth with Virtual Airgaps
Xage enforces virtual airgaps to provide defense-in-depth without requiring any network changes. By breaking and terminating each remote session at multiple network layers, Xage ensures that OT and IT assets remain secure within their respective network layers—without exposing the industrial DMZ to the internet nor the OT layers beyond their zones. Maintain strict network segmentation while enabling secure, policy-driven remote access across IT, OT, and cloud environments.

Regulatory Compliance Made Easy
Xage enables NERC-CIP, IEC 62443, and TSA compliance with immutable audit logs, multi-factor authentication, and role-based access control.

SANS First Look
Zero Trust-Based Access Management and Remote Access for OT-IT-Cloud
Get the SANS Report to gain expert insights into:
- Key challenges driving Secure Remote Access adoption
- Xage’s capabilities, architecture, and what sets it apart
Download the report to explore the full analysis.
Xage Delivers Unmatched Access Depth into OT and CPS Environments
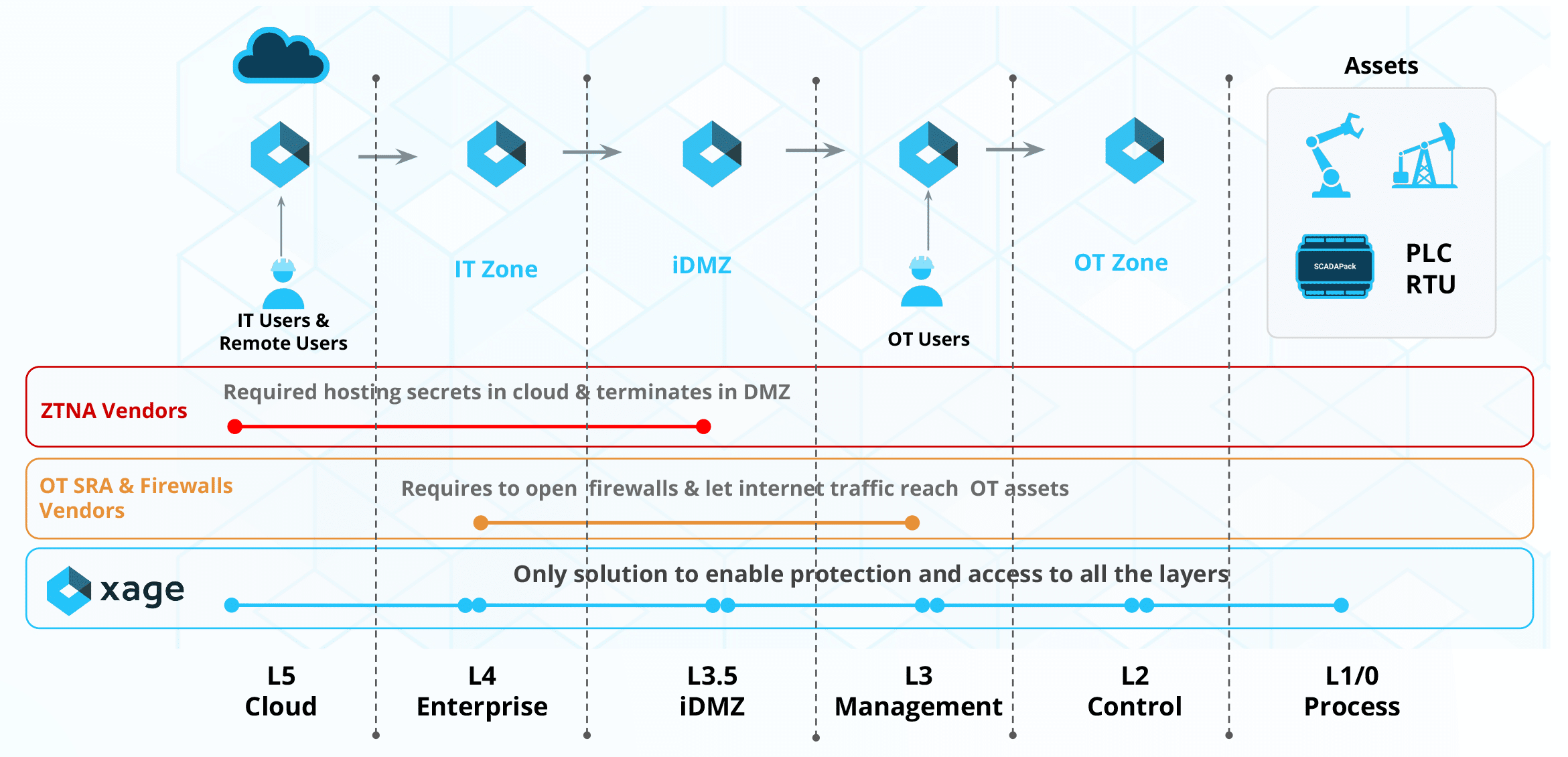
Unlike other solutions, Xage reaches beyond the DMZ to protect Layer 1 & 2 assets like PLCs and RTUs—without introducing additional security risks.
- Extends protection deeper than any other security solution.
- Eliminates the requirement to store credentials in the cloud—keeping full security control.
- Reduces firewall complexity without compromising network integrity.
- Minimizes downtime and security risks by controlling access to vulnerable assets instead of requiring disruptive patching.
Key Capabilities of Xage Secure Remote Access
Xage Secure Remote Access for OT and CPS is designed for effortless, intuitive access—whether for employees or third parties. Users simply log in through a browser and securely connect to the assets they need, with no complex setup or additional software required. Built with robust security, seamless user experience, and productivity in mind, Xage delivers a frictionless yet fully secure remote access solution.
Distributed Architecture and Password Vault
Xage is built on a distributed security fabric, ensuring resilience, scalability, and seamless compatibility with legacy systems—keeping you protected against evolving cyber threats.
Unlike traditional centralized security models, Xage securely distributes credentials across nodes, preventing attackers from deriving usernames or passwords even if a node is compromised. With no single point of failure or central target, Xage eliminates the risk of a high-value breach, delivering unparalleled security and reliability.
Agentless, Web-Based Access
Users can connect securely through a browser or desktop applications, eliminating the need for endpoint agents or pre-configured VPN laptops.
Single Sign-On and MFA for Apps & Devices
Xage enables seamless SSO to applications and devices and even extends it to legacy applications, removing the need to share passwords or remember multiple logins.
Xage provides multi-factor authentication (MFA) for remote access and local access, and can require additional MFA challenges not only at every subsequent layer of an environment, but also for individual devices, applications, and workloads across IT, OT, and cloud.
Secure File Transfer
Xage enables end-to-end encrypted file sharing, malware scanning, and file integrity verification to prevent cyber threats from propagating to CPS assets.
Native Application Support
Xage enables desktop applications (e.g., Studio 5000 and ROClink) to connect remotely to OT assets (e.g., PLCs) – without VPNs or requiring changes to existing firewall rules – while enforcing granular access policies.
Application Isolation
With Xage, operators can enforce granular controls, ensuring remote users have access only to the specific applications they need, rather than unrestricted access to all applications on the workstation.
Session Shadowing & Collaboration
Xage facilitates secure multi-user remote session collaboration with over-the-shoulder monitoring for multiple personnel to work together to resolve operational issue(s) on the same OT system.
Auditing & Monitoring
Xage simplifies compliance by addressing key security requirements. The distributed security fabric ensures tamper-proof audit logs, delivering audit-quality proof of every access attempt and device interaction. These insights are surfaced via Xage Insights, an advanced analytics engine.
Additionally, Xage enables policy-driven session recording, making it easy to configure and maintain comprehensive compliance records.
Multi-Monitor View
Multi-monitor view allows users to see and control application windows from multiple monitors when they’re working remotely, even if they might have a different number or arrangement of displays than are onsite.
Access Management with Multiple Identity Providers
Xage supports organizations to manage access to multiple IT and OT identity providers (IdPs) while giving users the flexibility to authenticate with either or both as needed.
Password Rotation
In addition to distributing password vaulting, Xage delivers automatic password rotation with every login (including OT assets like PLCs and HMIs), ensuring that credentials are always up-to-date and secure. This is a significant step in reducing the risk of compromised credentials from being used for unauthorized access.

EPIC Midstream Transforms Secure Remote Access with Xage
Discover how EPIC Midstream achieved ROI in just 3 months—boosting productivity, meeting regulatory mandates, and enhancing security across its operations.






