Author: Geoffrey Mattson, CEO, Xage Security
It is much better to prevent ransomware than to detect and respond when it is already in your system. Often, by the time ransomware is detected, it has progressed far enough to make mitigation impossible. Many businesses have paid ransoms in the millions and still experienced operational downtime and data loss due to ransomware. The intrusive incident response measures that are often activated after detection often result in enormous costs and downtime. The situation has grown so dire that cyberinsurers have jacked up premiums for ransomware insurance, or simply stopped covering ransomware at all. Stopping ransomware as early as possible in the attack chain is the best way to avoid paying hefty ransoms, losing data, or experiencing ongoing inability to do business due to operational disruption.
Over 130 variants of ransomware have been observed, many of which take different approaches to breaking in, locating valuable data, and encrypting or stealing it (or both!) for extortion. But certain basic tactics are fundamentally the same across every ransomware attack. These tactics offer a choke point that defenders can use to cut off ransomware before it reaches terminal velocity in the target environment.
In this post, we’ll explore three of the most preventable attacker tactics, techniques, and procedures (TTPs) used in every ransomware attack, and how Xage can prevent each one.
- Initial Access (MITRE TA0001), in which the attacker first gains the ability to access and manipulate a device within the target environment
- Target Discovery & Enumeration (MITRE TA0007), in which the attacker discovers and maps additional network-connected assets, applications, users, and files to be targeted or otherwise used in the attack.
- Lateral Movement (MITRE TA0008), in which the attacker expands their access beyond the initially compromised device or user, spreading malware from device to device and ultimately gaining access to high volumes of business critical files or assets that can be encrypted and held for ransom.
Succeeding in these three steps is crucial to the success of any ransomware attack. Defenders who can successfully prevent these steps have a much greater chance of stopping the overall attack early enough to prevent real damage.
Stopping Ransomware’s Initial Access with Multi-Layer MFA and Credential Rotation
Stolen credentials are one of the easiest and most popular mechanisms for attackers to achieve initial access to a target network. Credentials are obtained via social engineering, spearphishing, or simply purchased on the dark web after being compromised in a previous attack. These credentials are then used to log in, often via remote access channels such as RDP sessions. Once initial access is achieved, the attacker will work to escalate the privileges of their compromised credentials, or create new accounts with higher privileges.
Stopping initial access via compromised valid accounts (MITRE T1078) can involve a number of defensive techniques, including:
- Rotate/update credentials/passwords frequently and automatically so that any usernames/passwords that may have been stolen in the past will no longer work in the hands of an attacker.
- Enforce the principle of least privilege, limiting the privileges of any credential to the bare minimum necessary so that their credentials will not provide much leverage, even if an attacker gains access.
- Enforce multi-factor authentication at multiple layers to assure that even an attacker with a correct username and password will be prevented from logging in. With Multi-layer MFA, even an attacker that succeeds in social engineering or MFA-bombing their way past one MFA challenge will be stymied when they try to move laterally.
The last point is crucial. As MFA has come into widespread usage, cyberattackers have adapted. MFA fatigue/bombing attacks are one mechanism for circumventing MFA. SIM Swapping a user’s cell phone to gain control of their SMS-based MFA mechanism is another technique that was recently used in a successful attack against the MGM hotel and casino group.
Cyber defenders must restrict MFA code/token delivery to mechanisms that can’t be so easily hijacked. Xage disallows text-based MFA for this exact reason. Furthermore, Xage fulfills many of the recommendations for preventing Initial Compromise via Compromised Credentials listed in the October, 2023 release of CISA’s #StopRansomware Guide, including:
- Implement identity and access management systems
- Implement zero trust access control
- Store passwords in a secured database and user group hashing algorithms
- And many more.
Read more about Xage Multi-Layer MFA and Access Management here.
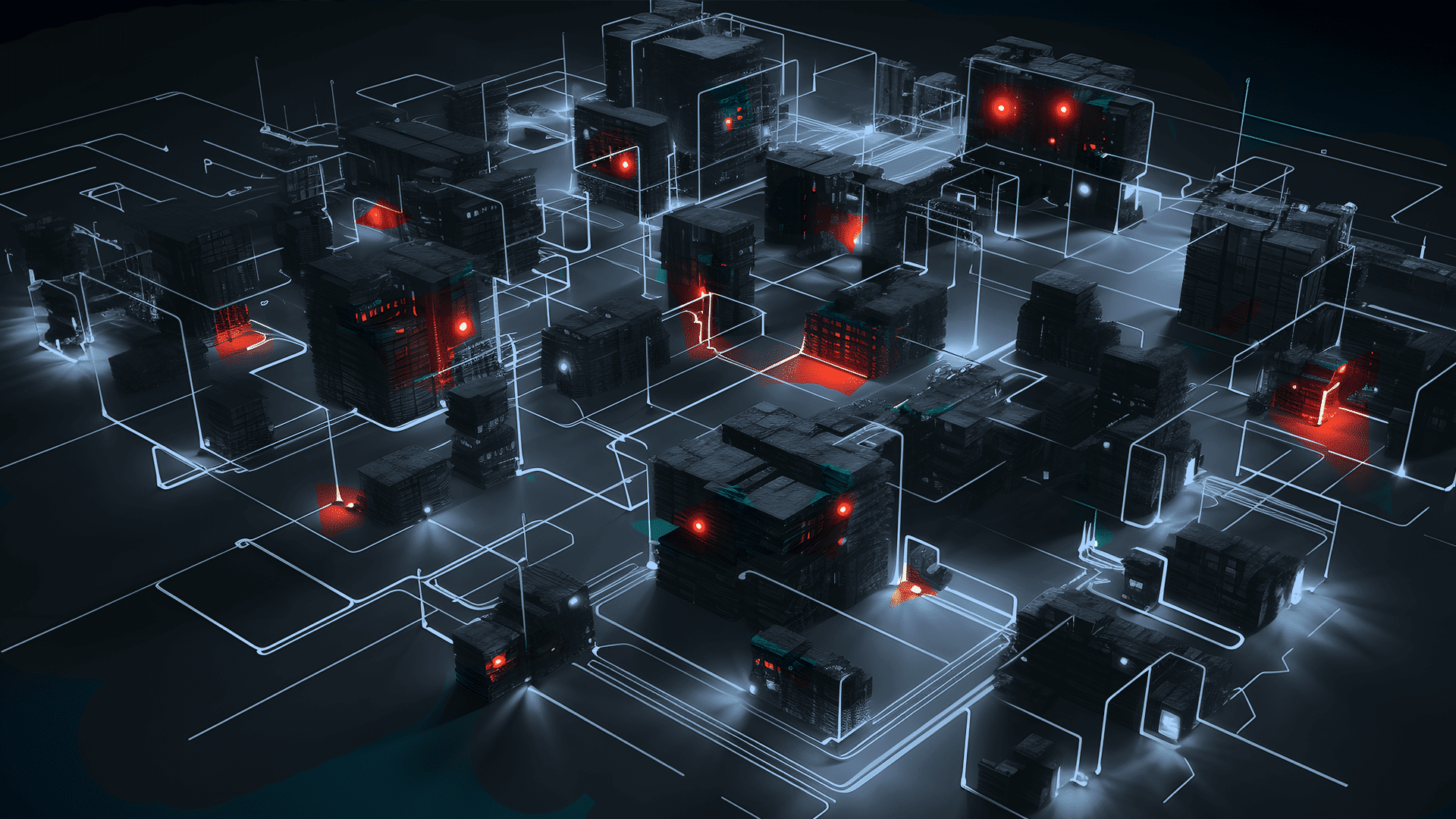
Preventing Ransomware Discovery and Target Enumeration with Machine-to-Machine Access Control
Asset discovery and target enumeration is another critical step in a ransomware attack.
In order to extract the highest ransoms, the ransomware has to encrypt data that is valuable to the target. In order to encrypt valuable data, the attacker needs to find it within the target system. This could mean intellectual property, customer data, or even data that is required for the function of internal systems and applications within the target. The MITRE ATT&CK Framework lists dozens of techniques, sub-techniques, and procedures that attackers can use for discovering everything from other network connected devices to files and directories to user accounts and group policy details.
Discovery and Target Enumeration are not adequately protected against in most networks. This lack of protection manifests in several ways:
- Devices within the environment are able to reach out to other devices by default, rather than requiring specific permission.
- The traditional approach of bucketing assorted assets into separate network zones using VLANs or internal firewall deployments is burdensome to manage, and still gives attackers plenty of wiggle room to discover new assets, users, and data to target.
- Most organizations have not implemented the level of segmentation that would prevent a compromised device from being used to discover additional targets. End user devices and sensitive data inhabit the same network zones and environments, leaving short pathways for attackers to discover where sensitive data is stored.
Identity-based user-to-machine, user-to-application, and machine-to-machine access control is the key to preventing discovery and target enumeration. Each machine in an environment should only be able to detect the presence of other machines that it must communicate with in order to serve its function. An attacker can’t attack what they can’t see.
Learn more about Xage machine-to-machine access control here.
Blocking Ransomware Lateral Movement with Identity-based Microsegmentation and Secure Data Transfer
Lateral movement is how ransomware spreads from one machine to another to ultimately reach high value data to encrypt, and likely to exfiltrate, to extort a high ransom. As with other Tactics, there are many Techniques, Subtechniques, and Procedures for moving laterally.
Many lateral movement techniques take advantage of built in networking tools and remote access utilities such as PowerShell to discover other machines that a local user has access to, then pivot to those machines. Some lateral movement techniques require manual, hands-on-keyboard action from the attacker. Others are “wormable,” meaning that they can automatically propagate themselves through certain known pathways on the target network. Remote access protocols such as RDP are common vectors. Once an attacker has gained access to sensitive machines or file shares, they need to transfer the actual malware that encrypts and exfiltrates the data.
In every case, the lateral movement phase relies heavily on target organizations allowing open and unencumbered communication between machines inside their environment. This is the classic “squishy middle” that exists in many organizations’ IT and OT networks. Once an attacker is inside, the barriers to prevent their expansion are lacking. Cybersecurity vendors and security operations teams must adapt their practices and technologies to prevent lateral movement as part of a holistic defense-in-depth approach to stopping ransomware.
A Zero Trust approach to identity-based segmentation is the key to preventing lateral movement. Attackers have learned how to rapidly spread within network zones and VLANs, then pivot between these segments. Defenders must increase the granularity of their security and exert access control and segmentation at the individual device and asset level, so that even if an attacker compromises one device or credential, they are prevented from using that toehold to expand laterally. Additionally, controlling the movement of data, especially executable files, laterally within the network is a powerful way to limit the spread of ransomware.
Xage fulfills or supports many of the exact recommendations for preventing lateral movement listed in the October, 2023 release of CISA’s #StopRansomware Guide, including:
- Apply the principle of least privilege to all systems and services.
- Employ logical or physical means of network segmentation by implementing a Zero Trust Architecture.
- Restrict usage of PowerShell to specific users on a case-by-case basis.
- Block both inbound and outbound connections on common Remote Monitoring and Management (RMM) ports and protocols at the network perimeter.
- And many more.
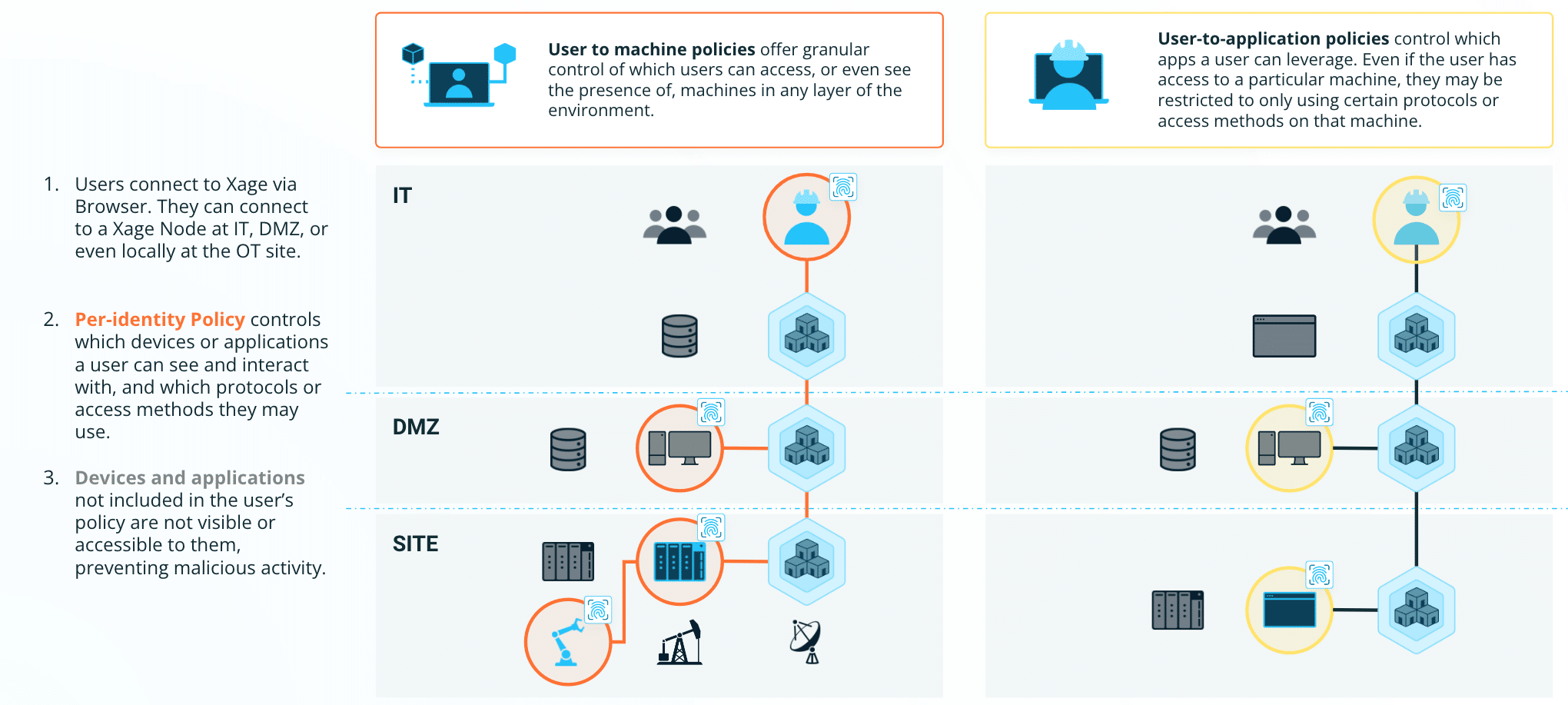
Stopping Ransomware Requires Zero Trust At Every Layer, From Network To Machine to User To Application
Ransomware has proven itself too fast and too harmful to rely only on detection and response. Organizations that invest in protection capabilities, with emphasis on the early stages of the attack chain, will find themselves in a much better position when the nearly inevitable ransomware attack does occur.
- At the Network level, Xage prevents both discovery and lateral movement by controlling which machines can communicate with each other, or even see each other’s presence.
- At the application level, Xage controls which users can interact with which applications, and which applications may interact with each other, or with other devices, enabling a least-privilege approach to application security.
- At the User level, Xage identity-based access control prevents attackers from exploiting compromised credentials to escalate privileges or conduct unauthorized activities.
Ransomware gangs will always work to adapt to new security controls. But the fundamental nature of ransomware requires them to achieve either widespread access within a target environment, or extremely targeted access to sensitive information. By deploying Zero trust protection at multiple layers, defenders can stop the progress of ransomware before it reaches the tipping point.