Zero trust network access (ZTNA), privileged access management (PAM), and microsegmentation in a single, simple platform that works across all of your environments.
Zero Trust Access
The Challenge
Today’s attackers are leveraging user identities, stolen credentials, and overly permissive access to wreak havoc. To prevent attacks and accelerate productivity, enterprises need the ability to control every interaction between users, data, applications and devices across their entire environment. With Xage that’s possible all from a single browser-based console—with no need for agents, clients, or network changes.

Protect Every App, Workload, and Site
Enforce MFA, SSO, and zero trust access policies on all apps, devices, workloads, and data across all cloud, datacenter, and cyber-physical infrastructure.

Manage Privileged Access and Prevent Attacks
Provide secure remote access while controlling every interaction and session to prevent credential abuse and insider threats.
Streamline Access and Reduce Complexity
Manage identities, credentials, and privileges in a single solution. Empower your workforce without compromising security.

Case Study | Learn Why Kinder Morgan Chose Xage to Protect Critical Infrastructure
Xage’s Zero Trust Access Solution
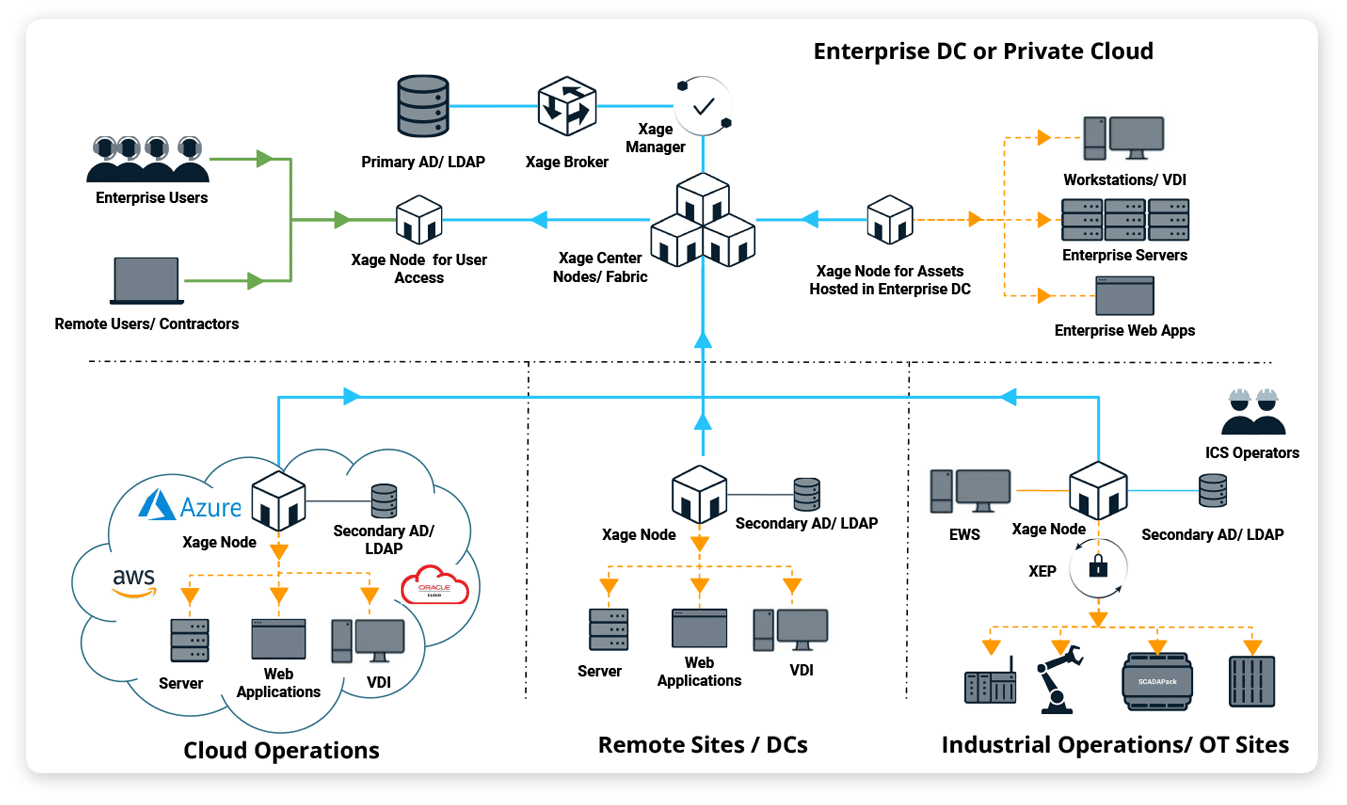
The Xage Fabric delivers complete control over who has access to your most critical assets, what they can do, when, and for how long—following the zero trust approach of never trust, always verify. The Fabric is highly available and resilient, so policy enforcement continues locally even if one site loses network connectivity. Xage offers greater capabilities than traditional IAM/ICAM and PAM solutions, while remaining simpler to deploy, manage, and use.
Secure Access
Enable remote and local access while exerting granular controls to stop lateral movement and living-off-the-land tactics. Xage eliminates the complexity of implementing clunky, agent-based PAM, firewall rule management, VLAN/ACLs, and other compensating controls.
- Enforce MFA, credential rotation, and SSO for every resource.
- Enable remote access to any device—no VPN, agent, or client needed.
- Simplify privilege management and revocation for users, including third parties.
Achieve Layered Zero Trust Security
Xage’s multi-hop architecture allows for deployment in multi-layer networks eliminating the need to poke holes through firewalls and provides session and protocol termination at each layer.
- All accounts and policies are managed centrally and enforced across the entire enterprise.
- This includes any type of asset including IoT/OT devices that do not have credentials.
- An MFA overlay is provided as an option at each layer and asset without added complexity or friction for the remote user.
Prevent Cyberattacks
Defenders must adopt defensive strategies as dynamic as the threats they face to safeguard organizations effectively. Xage controls access to prevent privileged accounts and living off the land techniques from being weaponized against your enterprise.
- Enable user-to-machine and machine-to-machine access control to limit attack blast radius.
- Secure file transfer between users and IT assets stops malware and ransomware from spreading.
- Prevent lateral movement with zero trust microsegmentation.
Reduce Costs, Accelerate Business
Xage overlays your existing infrastructure, meaning it can deploy in a day without requiring architectural changes.
- Provide needed third-party access quickly without compromising security.
- Xage multi-monitor view delivers a virtual operations center from anywhere.
- Users can collaborate remotely with outside technicians and experts, with the ability to invite approved users to remotely view or control a desktop, application, or terminal screen.
Easy to Use
Xage provides an improved user experience which doesn’t compromise security. Ease of use and security posture don’t need to have an inverse relationship.
- Enable SAML-based authentication to private apps without having to connect to the wider internet.
- Automated credential rotation and a distributed password vault secured by mesh architecture mean no single point of failure or compromise.
- Control and orchestrate identity across multiple IdPs and AD instances to streamline access and eliminate the risks from stolen credentials and insecure devices.

WHITEPAPER
Explore the power and simplicity of Xage Zero Trust Access.
Identity-First Security from Cloud to Edge
The Xage Fabric Platform is a highly available, resilient cybersecurity mesh that can enable access, control privileges, and enforce microsegmentation to protect cloud, IT, and OT environments without any disruption of existing systems.
“I started securing my architecture at the edge and quickly realized that anything I could use Xage for in OT, I could extend to my IT use cases too. Xage is far from just an OT tool. It’s a highly converged IT-OT solution.”
– Mark Forsythe, Senior Infrastructure Architect, EPIC Midstream

Works Where (and When) You Need It—Across IT, Cloud, and OT
- Since the Xage Fabric is based on distributed ledger technology, it can manage and secure IT, OT, and cloud infrastructure & apps with a single deployment.
- The option for local deployment in air-gapped networks can keep you protected and manage access even without internet connectivity. No cloud dependencies.
- Since Xage can integrate with local ADs across different network zones/sites, it eliminates duplication of effort and reduces identity management burden in organizations with multiple IdPs.