Author: Roman Arutyunov, Co-founder and SVP of Products, Xage Security
Cybersecurity authorities including the U.S. National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA) and international bodies have issued a joint Cybersecurity Advisory of a state-sponsored attack from the People’s Republic of China (PRC) affecting networks across U.S. critical infrastructure sectors.

The 24-page advisory provides detailed information about the exact tactics, techniques, and procedures used by PRC, including MITRE ATT&CK T-codes for reference. Notably, over 25% of the techniques listed were from the “Credential Access” tactic category (TA0006) of the MITRE ATT&CK Framework. It is well known that compromised credentials are involved in a rapidly increasing percentage of cyberattacks – over half, according to the 2022 Verizon Data Breach Investigation Report. This Cybersecurity Advisory demonstrates that even state-sponsored attackers consider legitimate credentials to be an incredibly important tool in their arsenal, and they will go to great lengths to access these credentials.
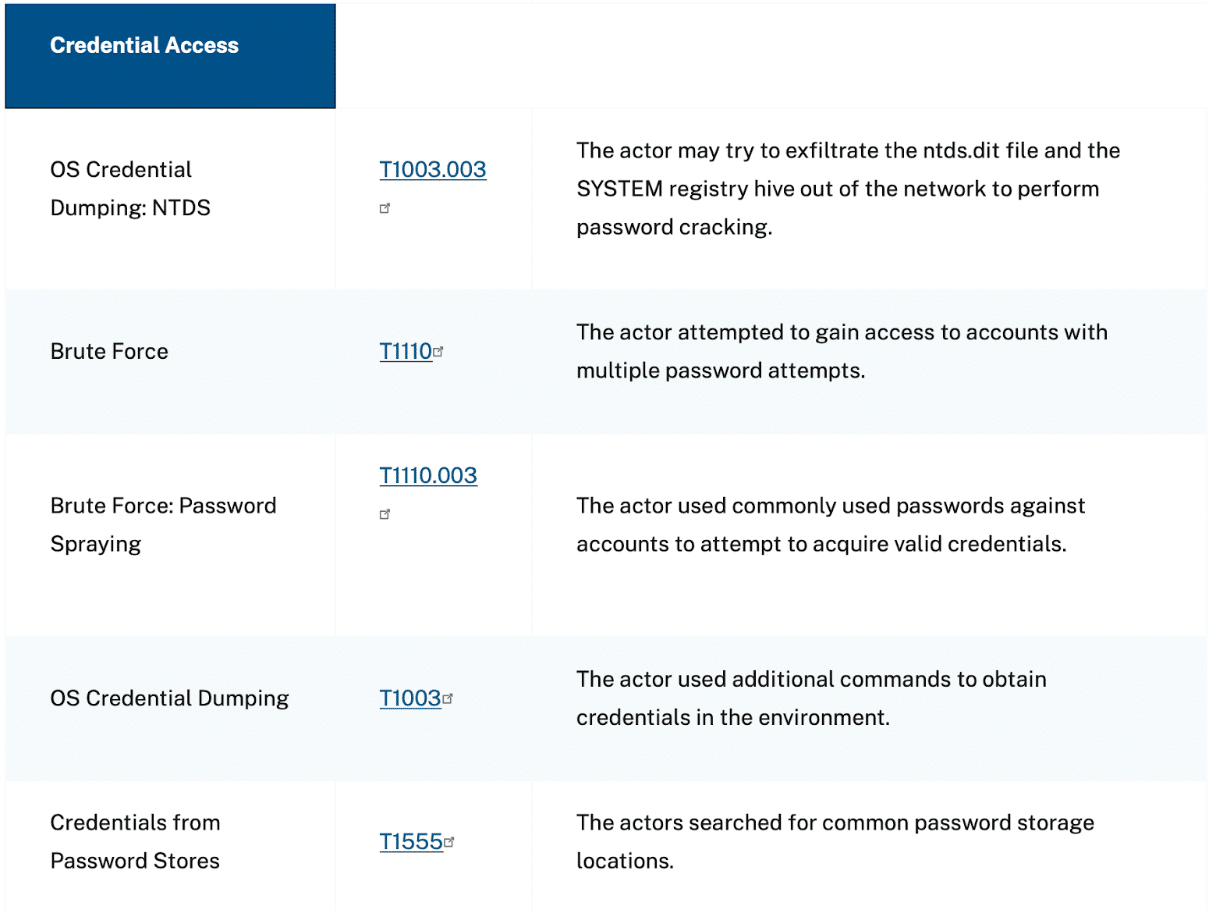
Caption: This screenshot from the Cybersecurity Advisory shows that five of the 19 attack tactics used by PRC were specifically intended to access credentials in the compromised environment.
Additionally, two more of the techniques used by PRC were to use commands to enumerate the active directory structure and overall network topology of the compromised network. These are classic precursors to lateral movement. First, the attacker figures out what other machines they can see on the network, and maps out a path to move laterally to other devices, using compromised credentials from within the Active Directory domain to gain remote and local access privileges. This is how attackers spread after gaining a toehold in a single device.
How To Stop Credential Access and Lateral Movement in Living-off-the-Land Attacks
The key to stopping compromised credentials from being such a powerful weapon in the attacker’s arsenal is to control and manage both the credentials themselves, and their access permissions to anything else in the environment. For example:
- Rotate credentials often, and automatically, so that even if a credential is compromised, it is eliminated quickly and no longer offers any level of access to an attacker.
- Store credentials securely so that an attacker cannot capture plaintext or hashed usernames, passwords, or other credential information that they can use to execute other attack tactics without being detected. Using a secure credential vault that leverages top-tier modern encryption standards is necessary to prevent the theft and abuse of legitimate credentials.
- Enforce Multifactor Authentication (MFA) at every layer of your environment to assure that even if an attacker accesses a legitimate credential, they are unable to use it to expand their access into deeper, more sensitive areas of your environment.
- Enact the principle of least privilege to ensure that every credential can only access, or even see the existence of, the bare minimum of other assets and applications necessary for that credential’s users to do their job. Today, most organizations are rife with “implicit trust zones” – network segments in which every credential inside has wide visibility and access to every asset in the same zone – which are a prime target for attacker lateral movement. Eliminate implicit trust zones to prevent attacker lateral movement.
- Control machine-to-machine communication to prevent attackers from mapping out your active directory structure or network topology. They can’t attack what they can’t see. If an attacker cannot enumerate further devices in your environment to attempt to compromise, they will be limited to the tiny footprint of the individual device in which they gained an initial toehold, and the damage they can do will be negligible.
Xage Blocks the Living-off-the-Land Attack Tactics Used by PRC
Xage offers numerous security controls to prevent the theft of credentials, and the abuse of compromised credentials, in critical infrastructure and other contexts across OT, IT, and Cloud. The Xage Fabric stores credentials in a secure vault using distributed consensus and threshold-based encryption for tamperproofing, rotates credentials automatically, and offers granular identity-based access control to every device and between devices.
To learn more about how Xage is already protecting assets and credentials to secure critical infrastructure organizations against the exact tactics being used by the PRC, please read our Customer Case Studies. If you want to learn how these capabilities apply in your own environment, please request a demo.










