Achieving Defense in Depth for Every Asset
Author: Vishal Gupta, VP of Product Management, Xage Security
Stolen credentials are involved in many cyberattacks. Estimates from researchers are as high as 80%. These credentials may be stolen by the attacker themselves, or bought on the dark web. Cybersecurity measures such as multi-factor authentication, FIDO2/passwordless authentication, automated credential rotation, and more have made it harder for attackers, but, for every defensive method, attackers develop new tactics, techniques, and procedures (TTPs) to continue their campaigns of theft and destruction. MFA-fatigue attacks are the latest craze, but they won’t be the last identity and credential focused attack tactic. Resourceful, well-funded attackers, sometimes with nation state assistance, will always find a way to bypass any individual layer of security. This is why defenders have broadly adopted the concept of Defense in Depth. While an attacker may bypass any individual security control, a layered set of complementary controls can make it much harder for attackers to achieve their objectives. The right approach to defense in depth can stop an attacker entirely, or slow them down enough that proactive measures can be taken to eject them from the target environment before damage is done.
How Do You Achieve Defense In Depth? It Starts With Identity.
Nearly every headline-making attack of the past two decades, from Target to Equifax to Stuxnet to the Colonial Pipeline ransomware, involved stolen or compromised credentials. Since stolen credentials are so often the attacker’s key weapon of choice, defenders must make it their top priority to defend against this attack vector. Secure identity and access management is the first step in any modern approach to defense in depth. There have been great advancements in the field of IAM, including multi-factor authentication (MFA) and passwordless login, but these are only part of the picture for an identity-first defense in depth strategy. By controlling, at a granular level, the access that each individual has, you limit the damage that can be done even if one of those credentials are compromised.
Today, Xage Security is announcing the release of a new, first-to-market capability to bring defense in depth to every layer of OT and ICS environments. We’re calling it Multi-layer Access Management. This innovation pairs with our existing multi-layer multi-factor authentication capability to protect critical infrastructure. It enables our customers to stop attackers from compromising critical assets, even if they have access to stolen privileged credentials.
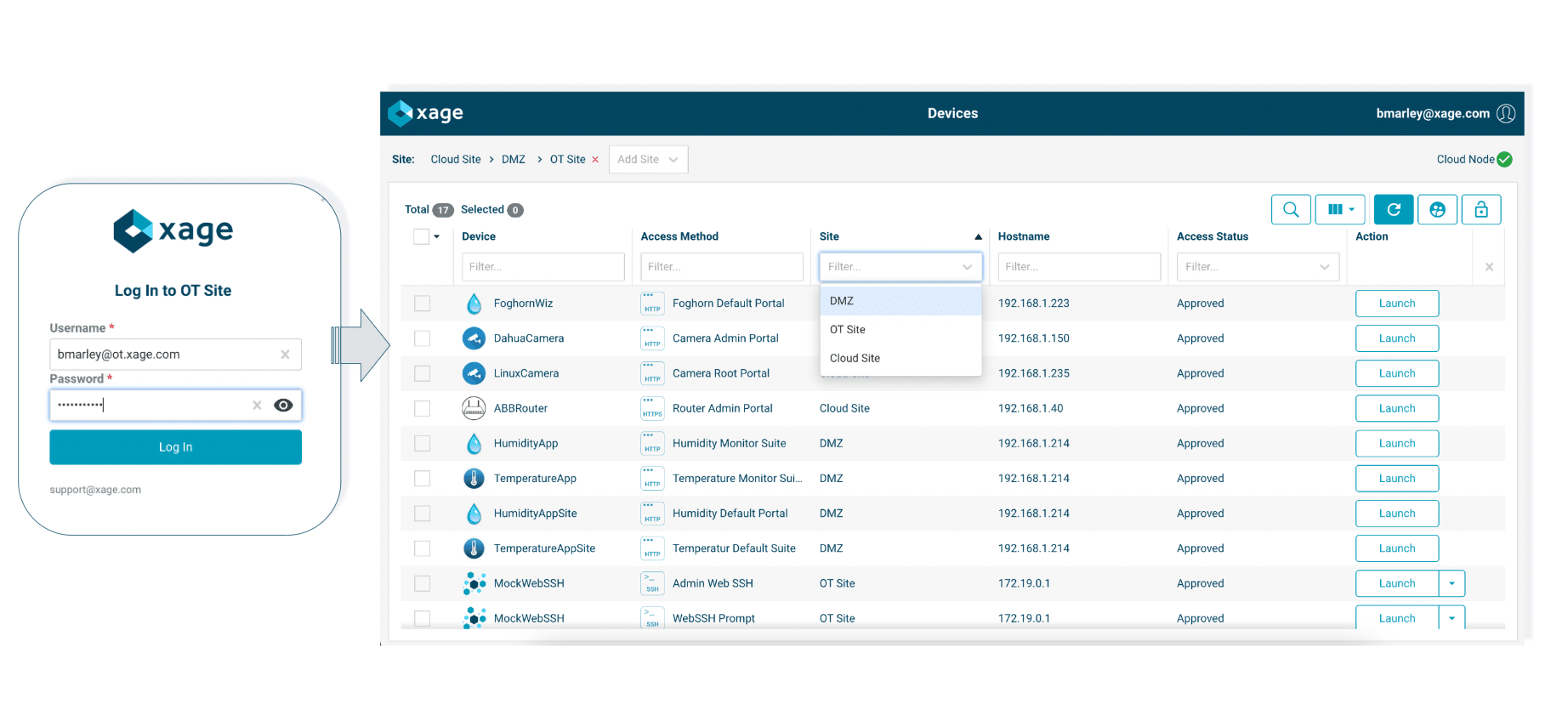
With Xage Multi-layer Access Management, our customers can reduce complexity in their access management flow, improve user experience, and block attacks thanks to these unique capabilities:
- Multi-IdP/AD Support: Orchestrate multiple Identity Providers (IdPs) and Active Directory (AD) domains with different security zones or network layers. This multi-IdP and multi-AD capability supports multiple authentication methods such as LDAP, SAML, and ADFS. For example, your IT zone can be configured with Azure Active Directory with SAML, your OT zones can be configured with on-premises Active Directories with LDAP or SAML via ADFS, while at remote intermittently-connected sites authentication can be supported directly by the on-site Xage Fabric.
- Controlled asset visibility: Local and remote users see the assets and systems for a site or zone only after they successfully authenticate against that site-level IdP/AD and pass the site-level MFA challenge. This prevents attackers from identifying sensitive assets and enumerating potential targets, even if they gain access to credentials in your environment. It also allows independent control of access and visibility at each level, stopping a single compromise from exposing the entire environment.
- On-site authentication: Enable local users to authenticate locally on-site even if the site loses external network connectivity. Xage’s distributed mesh architecture is inherently secured with distributed ledger technology, and enables ongoing policy enforcement and authentication at a local level, even if a site loses network connectivity and cannot communicate with other sites.
- Passwordless authentication: Xage allows users, both local and remote, to authenticate using passwordless authentication, including biometric methods. This works across multiple layers that may be mapped to different identity providers.
- Multi-hop access: Each time a user or application traverses across network layers to remotely access any asset or data, it follows a multi-hop network path. Each hop is formed by an encrypted, signed tunnel between Xage fabric nodes, using signatures that are protected in the Xage Fabric to stop IP spoofing and man-in-the-middle attacks. Every hop forms a protocol and connection break, separating security layers from one another, and further strengthening the integrity and security of the access session.
Xage’s Multi-layer Access Management enables organizations to eliminate attacks on their critical infrastructure by delivering defense-in-depth security for their environments, orchestrating protection across multiple Identity providers, Active Directory instances, network security levels, and locations.
Learn More About Xage Security Products and the Xage Fabric Platform










