Critical Infrastructure Operators are Rapidly Adopting Zero Trust, But Some Risk Falling Behind
Our critical infrastructure is at an inflection point. Hackers and nation-state actors have vigorously targeted the systems that underpin our everyday lives. Reactive cybersecurity practices that pivot on threat monitoring are no longer cutting it. Operators need new security strategies that go beyond threat monitoring to block hackers at the source and prevent them from gaining hold.
At Xage, we’ve seen more and more operators invest in solutions to build a more proactive and protective cybersecurity posture by embracing zero trust strategies. We wanted to see if this was the case across the industry and better understand how the evolving threat landscape and government security directives have impacted operational cybersecurity leaders as a whole.
To do that, we partnered with Wakefield Research and surveyed 250 cybersecurity senior executives in energy, aerospace, port operations, transportation, pipeline operations, utilities, and retail supply chain and warehousing. We asked them about their progress towards implementing zero trust—the proactive security model proven to block cyberattacks or significantly mitigate their effects.
The main takeaway? Across the board, critical infrastructure cybersecurity leaders are embracing zero trust. In fact, 61% of respondents agreed that a reactive approach is no longer enough to prevent breaches, and more than half (64%) indicated that they’ve already shifted to a proactive strategy to better block and contain attacks.
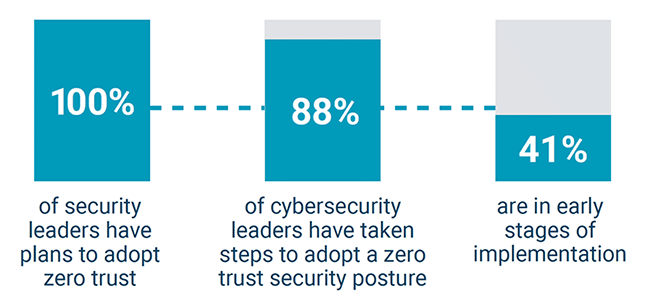
Even further, the findings make it clear that all critical infrastructure organizations are moving towards zero trust:
- 100% OT cybersecurity leaders are planning to adopt zero trust
- 88% of surveyed organizations are already taking steps to adopt.
- 41% are in early stages of implementation
Critical Infrastructure Operators Are Adopting Zero Trust Faster Than You Think
But some are moving faster than others. Nearly half of surveyed cybersecurity leaders (42%) still subscribe to the long-held notion that adopting zero trust requires a full equipment overhaul.
As Xage and its customers know, technologies that enable a zero trust security model can be delivered as an overlay on top of the existing systems. A rip and replace isn’t the only way forward, and thinking otherwise can send cybersecurity leaders down a rabbit hole and extend implementation timelines.
Our team put together a report that outlines all the key insights we gleaned from cybersecurity executives, including lingering knowledge gaps, adoption roadblocks, and how the industry can speed up zero trust implementation. You can download it here. Regardless of where you stand in your shift from a reactive to a proactive cybersecurity posture, we hope you find these insights useful.
Thanks for reading. If you have any questions about the report or the logistics of implementing zero trust in operational environments, please don’t hesitate to reach out.
-Duncan Greatwood, CEO of Xage










