Critical Asset Protection for OT, Data Center and Cloud
Protect critical environments from exploits and unauthorized access with Xage’s unified platform. Leverage virtual patching, identity-based asset-by-asset access control, and dynamic segmentation to block attacks, contain breaches and reduce risk—without costly disruption.
The Challenge
Critical environments are often exposed to high degrees of risk due to shared or unmanaged credentials, unpatched devices, and fragmented control systems. Organizations struggle to deploy uniform access protection controls for diverse systems that may or may not have native security capabilities. Traditional security approaches rely heavily on patch cycles, firewalls, and implicit trust zones, which are too slow, operationally disruptive and insecure to address modern threats.
Benefits
With Xage Asset Protection, organizations gain comprehensive, unified security to block threats, contain attacks, reduce risk, and advance Zero Trust initiatives. The Xage architecture reaches deeper into critical environments than any other solution, combining built-in resilience with a lightweight, easy-to-deploy design that simplifies management without compromising protection.

Unified & Comprehensive Protection
Xage provides end-to-end security across diverse, hybrid environments—spanning both modern and legacy systems from OT through Data Center to Cloud—through a single, integrated platform. The unified approach streamlines management and enforces consistent security policies without sacrificing usability or efficiency.

Mitigate Risk
Xage Asset Protection contains breaches in critical environments. The solution intelligently integrates virtual patching, identity-based segmentation, and access control into a cohesive solution.
Enforce Zero Trust
Xage delivers Zero Trust by continuously authenticating and controlling every user, machine, and application interaction—dynamically adjusting access based on real-time context and risk. With Xage, organizations can enforce just-in-time, least-privilege access, secure vulnerable and unpatchable devices with virtual patching, and implement adaptive, identity-based segmentation at the user and asset level.

Deep, Granular Control at Every Level
Xage extends protection deeper into critical environments than any other solution, delivering fine-grained control beyond traditional zone-based models. Unlike approaches that stop at the perimeter or zone level, Xage enforces RBAC security policies down to individual digital or cyberphysical assets.
Resilient by Design
Xage’s distributed architecture eliminates single points of hack and failure. Tamper-proof vaults and logs ensure data integrity, while local policy enforcement at every node guarantees continuous protection—even in offline, air-gapped, or degraded network conditions.

Seamless Deployment, Zero Disruption
Xage Asset Protection removes the need for complex firewall reconfigurations and simplifies security implementation with an agentless, non-intrusive design. It integrates effortlessly into existing architectures without disrupting operations—enabling deployments to be completed within hours.
Kinder Morgan Selects Xage To Cyber-Harden Critical Infrastructure
One of the largest energy infrastructure companies in North America protects against escalating cyber attacks and improves employee productivity with Xage.
- Improved security posture and reduced risks from cyberattacks
- Increased personnel productivity through a consistent approach to access management across multi-vendor systems
- Delivered cyber hardening without disruption to operations
Key Capabilities of Critical Asset Protection
While foundational, legacy security methods like firewalls, VLANs, and patching fall short in today’s complex, distributed environments. These static, hard-to-manage tools and processes often create security gaps that attackers exploit.
Xage Asset Protection replaces complexity with dynamic, easy-to-deploy solutions that adapt to modern realities—while containing breaches, reducing risk, and protecting assets without adding operational burden.
Virtual Patching
Virtual patching provides a non-intrusive, proactive defense against zero-day threats and known vulnerabilities—securing even unpatchable assets without disrupting operations. By shielding systems from exploitation and limiting lateral movement, it effectively contains threats before they can spread.
Zero Trust Segmentation
Legacy VLAN and firewall segmentation exposes critical environments to risks like implicit trust zones, lateral movement, and ongoing management burden. Xage’s Zero Trust segmentation provides dynamic, per-user and per-device policies that limit lateral movement and simplify management
IEC 62443 Zones & Conduits
Xage Extended Protection (XEPs) create secure micro-zones and conduits to control both east-west and north-south traffic—streamlining network segmentation and simplifying compliance with IEC 62443.
Just-in-Time Access
Identity-based, policy-driven controls grant only the necessary access, for the time that it is needed. By generating one-time credentials instead of relying on static ones, it eliminates a major attack vector. Granular, role-based controls extend to all assets, including end of life (EoL) and end of sale (EoS) assets.
SSO and MFA
Xage provides comprehensive, phishing-resistant MFA and SSO for secure, seamless access across all assets. Multilayered MFA and advanced access management are supported, including integration with multiple identity providers. Xage’s unique MFA solution ensures protection even for disconnected environments, delivering consistent security for every asset—regardless of location or connectivity.
Visibility to Policy Management
Create, manage, and enforce Zero Trust policies with confidence. Xage Visibility-to-Policy (V2P) Studio enables teams to build policies based on real asset behavior rather than assumptions. By translating live visibility into enforceable access controls, organizations can reduce over-permissioned access, improve segmentation, and protect critical assets across IT, OT, and cloud environments.

WHITEPAPER
Explore the power and simplicity of Xage Zero Trust Access and Protection
Xage Extended Protection (XEP)
Xage Extended Protection (XEP) enables dynamic asset-level micro-segmentation, controlling both east-west and north-south traffic.
XEP can be used to implement multiple zones and conduits to adhere to IEC 62443 compliance requirements. It delivers multi-layer, zero-touch, policy-driven security by blocking compromise attempts, automating policy creation, and eliminating the need for additional firewalls. XEP provides identity-based access down to Layer 1, shields vulnerable assets, encrypts asset-to-asset communications, and can be seamlessly deployed in front of switches or devices.
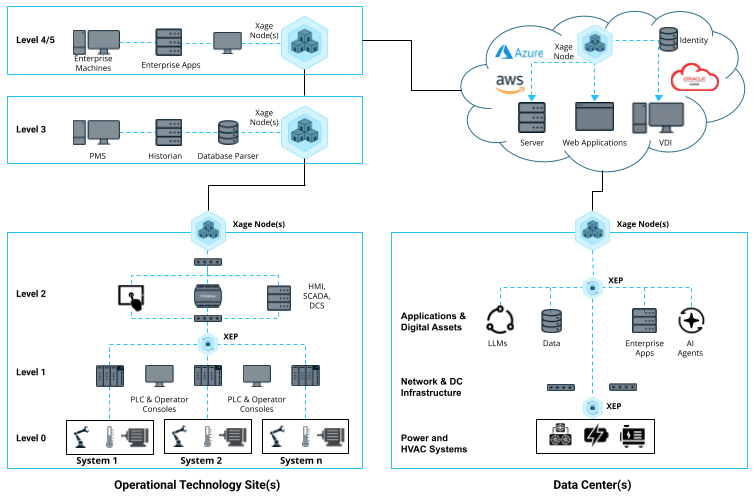
Device-to-device policies govern which machines may speak to each other, preventing lateral movement between and within sites.

Hardware XEP
Versatile security appliance that can be deployed across layers of Purdue Model. They protect up to 10,000 devices and are designed to operate in the most harsh environments.

Virtual XEP
Cost effective VM that can be deployed across datacenters and industrial sites where virtualization infrastructure already exists.
Accelerate Zero Trust with Visibility-to-Policy Studio
Xage Visibility-to-Policy (V2P) Studio combines real-time behavioral visibility with foundational security controls to deliver Zero Trust access policies that are accurate, enforceable, and aligned to how assets actually operate.
Context-Aware Discovery
Automatically discovers assets and interactions to clearly show required access and reduce exposure.
From Insight to Policy
Observed interactions are used to create identities, group assets, and generate enforceable Zero Trust policies faster.
Lower Risk, Faster Onboarding
Speeds onboarding for new and expanding environments while reducing over-permissive access.
Watch the demo video to see V2P Studio in action.
Meet Compliance Mandates
Through fine-grained access control, dynamic segmentation, and real-time threat containment, Xage enables organizations to meet rigorous security and compliance requirements, including but not limited to:
- IEC 62443
- NIST CSF 2.0
- NERC CIP
- TSA SD02C
- NIS 2
- CIS Controls v8
- CISA Cross-Sector Cybersecurity Performance Goals
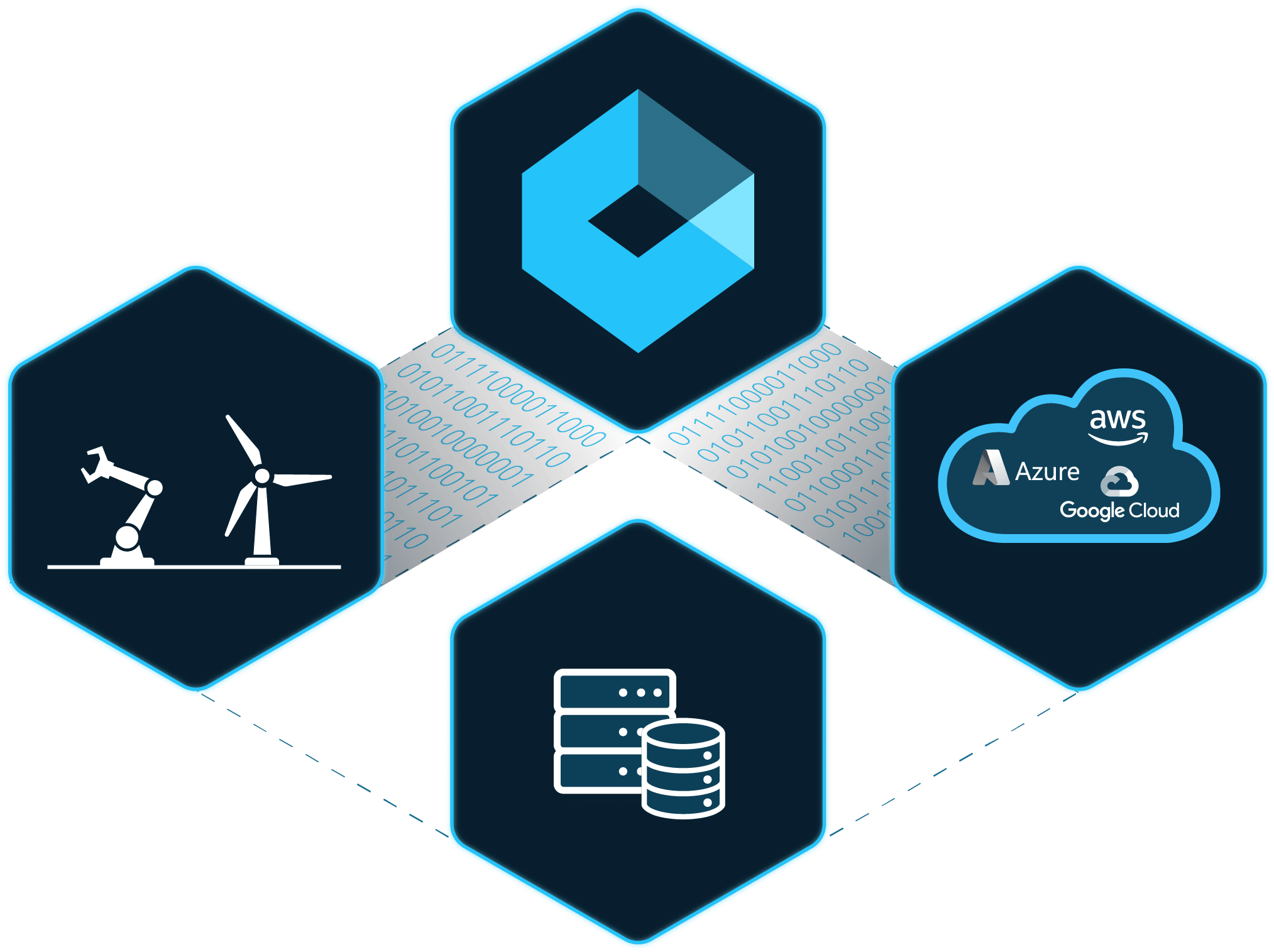
Xage Fabric Platform
Xage Security provides a suite of Zero Trust solutions that can be deployed independently or seamlessly integrated through the Xage Fabric Platform. Explore the Platform to discover how each solution works together to deliver comprehensive protection, eliminate legacy security solutions, and improve overall total cost of ownership.
Related Resources
Contain Breaches Without Complexity
Fill out the form and someone will be in touch with you within 24 hours to schedule a meeting.







