Streamlined vendor access management that enables the outside support you need while securing third-party access across every network, user, and application environment.
Vendor Access Management
The Challenge
Companies depend on vendors for essential services, including work that requires access to the company’s internal systems. That might mean creating accounts for third-party personnel to connect directly to your assets to provide support and maintenance. It can also mean providing privileged access to your network directly to vendor software, hardware, or systems. But with third parties being an increasing means of attack, how can you securely manage and monitor vendors while enabling necessary access?

Protect Every App, Workload, and Site
Wherever a third party needs access, keep it secure with MFA, SSO, and zero trust access policies across all cloud, datacenter, and cyber-physical infrastructure.

Manage Vendor Access and Prevent Attacks
Provide secure remote access while controlling every interaction and session to prevent credential abuse and insider threats.

Increase Productivity and Reduce Complexity
Manage identities, credentials, and privileges for vendors in a single solution. Accelerate business without compromising security.

Case Study | Learn Why Kinder Morgan Chose Xage to Protect Critical Infrastructure
Xage’s Vendor Access Management Solution
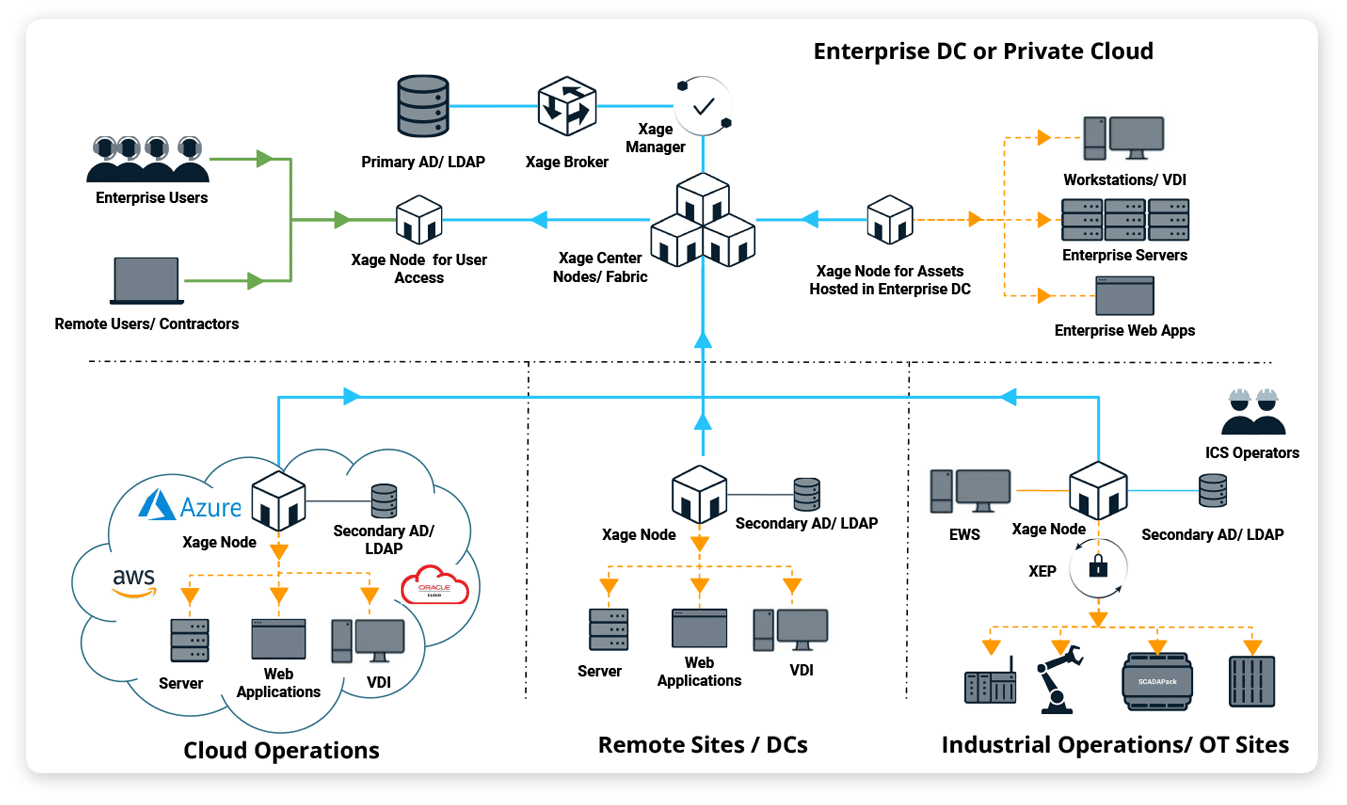
The Xage Fabric gives you complete control over who has access to your assets, what they can do, when, and for how long—enabling third-party vendors the access they need while reducing risk. The Fabric is highly available and resilient, so policy enforcement continues locally even if one site loses network connectivity.
- Provide just-enough and just-in-time access for vendors and easily revoke access as needed.
- Automatically manage and configure access permissions from a central console.
- Enable vendor remote access without risky VPNs.
Vendor Privileged Access Management
Tightly manage every third party’s privilege level and monitor privileged sessions to prevent attackers from leveraging vendor access to move within your infrastructure. Easily create granular policies to control which third-party users, applications, and devices can access critical systems and data. With Xage you can ensure security, even if vendors require privileged access to one or more of your systems.
Secure Access
Support remote and local vendor access while enacting control and monitoring of third-parties to prevent them from causing harm.
- Get built-in over-the-shoulder session monitoring and recording capabilities.
- Enable remote access to any device—no VPN, agent, or client needed.
- Simplify privilege management and easily revoke access.
Get Layered Zero Trust Security
Xage’s multi-hop architecture allows for an extra layer of security for vendor access, simplifying the configuration of firewalls and providing session and protocol termination at each layer.
- All vendor accounts and policies are centrally managed and enforced across the entire enterprise.
- An MFA overlay is an option at each layer and asset without added complexity or friction for the remote third-party user.
- Easily segment vendor accounts and privileges so they don’t have access to sensitive infrastructure.
Prevent Cyberattacks
Whether via a vendor or otherwise, attackers are likely to find a way to connect to your infrastructure. A strong security posture means that’s as far as they get. Xage controls access to prevent privileged accounts and living off the land techniques from being weaponized against your enterprise.
- Enable user-to-machine and machine-to-machine access control to limit attack blast radius.
- Secure file transfer between users and IT assets stops malware and ransomware from spreading.
- Prevent lateral movement with zero trust microsegmentation.
Reduce Costs, Accelerate Business
Xage overlays onto your existing infrastructure, meaning it can deploy in a day without requiring architectural changes.
- Provide needed third-party access quickly without compromising security.
- Xage multi-monitor view delivers a virtual operations center from anywhere.
- Users can collaborate remotely with outside technicians and experts, with the ability to invite approved users to remotely view or control a desktop, application, or terminal screen.
Easy to Use
Xage gives an improved user experience while strengthening security posture.
- Enable SAML-based authentication to private apps without having to connect to the internet.
- Automatically rotate credentials and use a distributed password vault secured by a mesh architecture with no single point of failure or compromise.
- Control and orchestrate identity across multiple IdPs and AD instances to streamline access and eliminate the risks from stolen credentials and insecure devices.
Identity-Based Access from Cloud to Edge
The Xage Fabric Platform is a highly available, resilient cybersecurity mesh that can enable access, control privileges, and enforce microsegmentation to protect cloud, IT, and OT environments without any disruption of existing systems.
Related Resources
Unlock Productivity Without the Risk
Fill out the form and someone will be in touch with you within 24 hours to schedule a meeting.







