Reduce attack surface and achieve granular security to prevent attacks.
XAGE SOLUTION
Zero Trust Microsegmentation
The Challenge
How do you prevent an insider threat, or a user with stolen valid credentials, from spreading laterally and causing harm in your environment, from data centers to branch offices to remote sites? Abuse of stolen valid credentials for initial intrusion, internal reconnaissance and lateral movement is one of the most common and successful cyber attack tactics. Traditional internal methods for preventing lateral movement lack the granularity and scalability necessary for today’s enterprises. VLANs, ACLs, IP-based firewall rules, and cloud security policies lack awareness of user, session, or application context. These solutions lack the overall identity context necessary for effective segmentation.
Capabilities of Zero Trust Microsegmentation

Create Granular Access Policies
Deny access by default, and only allow users to access assets they need for their role. Enforce time limitations per account, and per asset, to assure the principle of least privilege, a foundation of zero trust security, is adhered to.

Verify and Authenticate Users
Zero trust microsegmentation requires the ability to verify a user or non-person entity’s (NPE) identity and permission levels to interact with other assets on a per-identity basis (as opposed, or in addition, to network zone or group basis).

Application, Process, and Workload Aware Control
Modern zero trust microsegmentation must go beyond coarse site-to-site control via network segments, and provide granular application, process, and workload aware control within each site to prevent identity-based attack tactics in real time.
Dynamic, Just-in-Time Segmentation
Traditional segmentation approaches rely on static rules that are burdensome to update, resulting in unwieldy, risk-laden rulesets. Modern zero trust microsegmentation must enable simple policy creation to streamline business without accumulating risk.
Xage Offers Unique Zero Trust Microsegmentation Benefits
Minimize VLAN and ACL Reliance. Simplify Firewall Management. Protect Every Asset.
Xage delivers unique zero trust microsegmentation capabilities to prevent attacks by blocking unauthorized access, lateral movement, and credential abuse in a single, streamlined solution. Xage is tailored especially to improve the security posture of highly distributed environments and interconnected OT, IT, and Cloud.

Prevent Cyberattacker Lateral Movement
Xage enforces least privilege by default, assuring users, machines, and applications can’t communicate unless explicitly allowed by policy. This eliminates key lateral movement and target enumeration pathways abused by cyberattackers.
Reduce Operational Complexity at Scale
Managing VLANs, ACLs, and firewall rules to control access internally is complex, expensive, and doesn’t scale. Xage allows simple, centralized policy creation to protect every asset from core to edge to cloud.

Unified Segmentation for Modern and Legacy Assets
Xage enables zero trust microsegmentation equally across datacenters, applications, cloud assets, and even for OT/ICS devices and legacy technology. You don’t have to go without segmentation at your most critical sites, or manage multiple security technologies to achieve a zero trust architecture and fulfill security requirements.
Resilient in Distributed Environments
Xage zero trust microsegmentation policies do not require cloud connectivity to function. If a remote site loses contact, policies are still stored and enforced locally. Security teams can be confident that your security posture is strong even if network connectivity is unstable.
Xage Offers Unique Zero Trust Microsegmentation Benefits
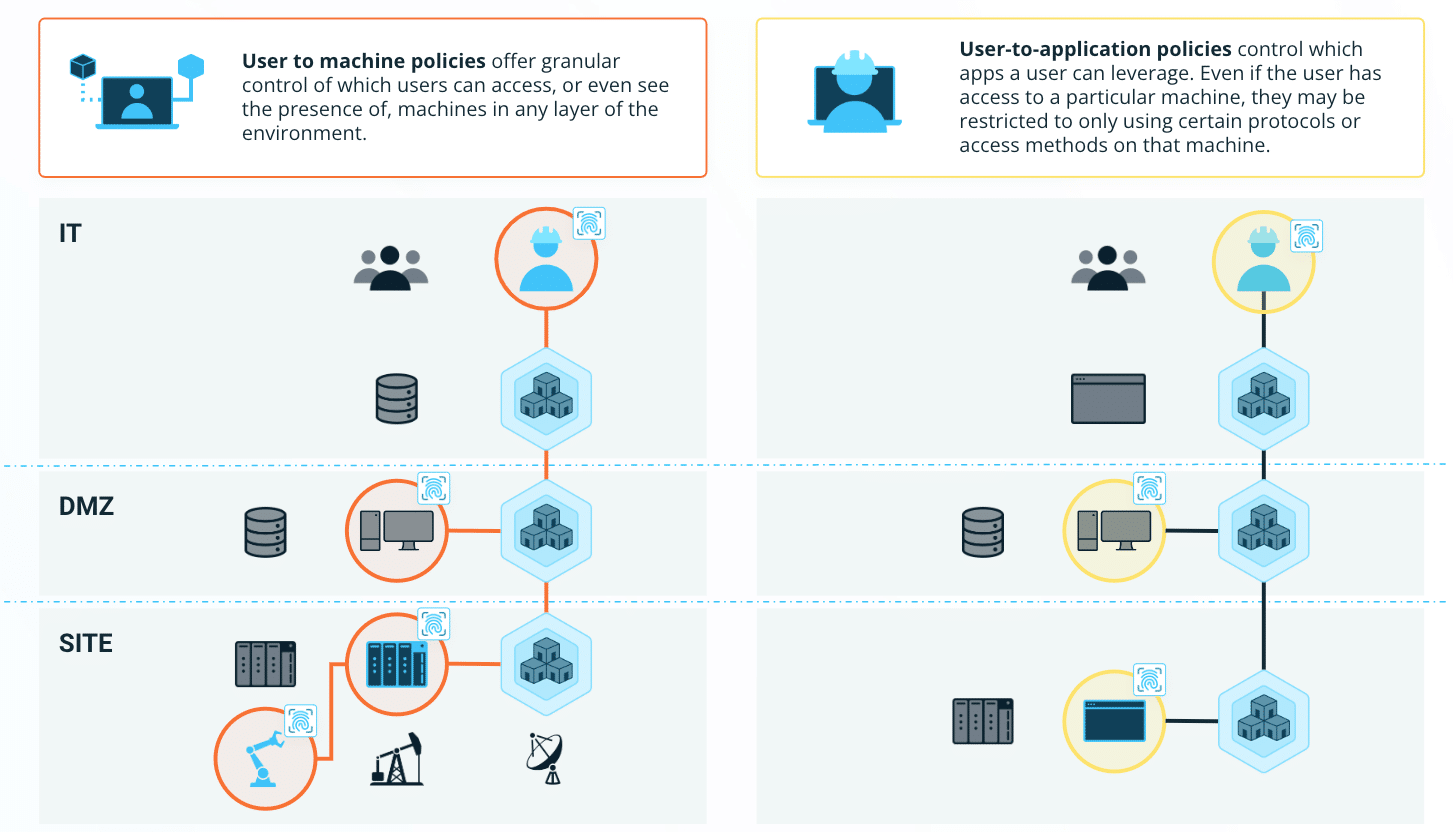
1. Users connect to Xage via Browser. They can connect to a Xage Node at IT, DMZ, or even locally at the OT site.
2. Per-identity Policy controls which devices or applications a user can see and interact with, and which protocols or access methods they may use.
3. Devices and applications not included in the user’s policy are not visible or accessible to them, preventing malicious activity.
“Universal ZTNA extends existing ZTNA technologies to use cases beyond remote access in order to support local enforcement in on-premises campus and branch locations. Universal ZTNA centralizes device and end-user zero trust access policy to enable a single access policy definition.”
August 2023 Market Guide for Zero Trust Network Access

DOWNLOAD THE GUIDE
Market Guide for Zero Trust Network Access
Xage Recognized by Gartner for ZTNA Solution
Xage Zero Trust Microsegmentation Differentiators
Xage goes beyond user-identity based zero trust microsegmentation to include machines and applications, providing greater security against ransomware, lateral movement in network traffic, insider threats, and valid credential abuse, all while minimizing management requirements, reducing firewall rules, and simplifying policy management.
Capabilities
Xage Fabric
Network-based Segmentation (VLANs, Firewalls, ACLS)
Identity-based, Least-privilege Access

Asset-level Access Control for OT, IT, and Cloud


Identity-aware Access Logging


Multi-Factor Authentication at Every Layer


End-to-End Encrypt


Session Recording


Credential Rotation and Management

Distributed Password Vault (no single point of failure or compromise)


Agentless








